Crimes Against Humanity and War Crimes Act (S.C. 2000, c. 24) [Link]

Testimony
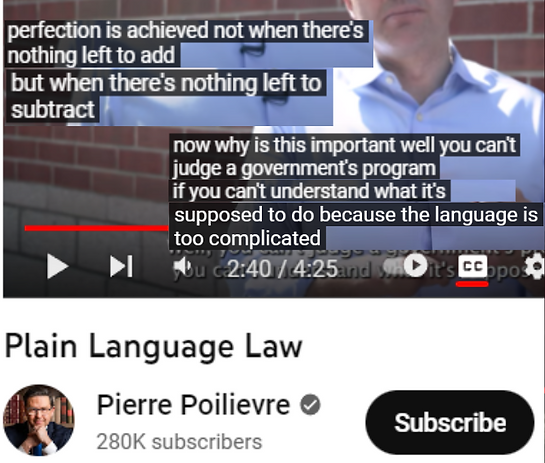
TWELVE Years of Context | FOUR Years of Abuse | ONE Scandal

BACKGROUND
Sophisticated Harassment & Denial of Recourse to Authorities


VISION
PRECEDENT
PsyOps, InfoOps, CIMIC, & the Gosselin Reports concerning the CAF
2030 Canada Agenda National Strategy, the WEF,
& Shared Blueprint

EXECUTION
4IR Capabilities, Project Viability, Cognitive Liberty, & Human Rights

COHERENCE
Contemplating the Effects: The Likelihood of a State-Adjacent Project.
Prologue: Toward an Understanding of Cognitive Liberty Crimes

In 2013,
I had the privilege of meeting the CEO of a prominent international consulting firm headquartered in the United States. This person is also a prominent deacon in the Roman Catholic Church. During a face-to-face conversation that was otherwise casual, this person made preemptive reference to an unsettling amount of personal details germane to my person, suggested my thought life was accessible, and suggested I was a “guinea-pig in an international project by influential people who wanted to live forever”. He further referenced a specific invasive surgery procedure I had previously undergone; one that the same surgeon later deemed to be unnecessary. Although I emerged from the conversation unsettled, I thought little of it thereafter, believing the man to be eccentric. At the time I was living an otherwise normal life.
Fast-forwarding to February 2021, and in accordance with the detailed observations in UN Resolution A/HRC/57/61 (here), and germane to articles published in recent years in TIME Magazine (here), the Harvard Gazette (here), and other publications (ie., here), I infer to be the victim of a Cognitive Liberty crime. I make this inference under the guidance of the test in Sherman Estate v. Donovan, 2021 SCC 25 at paragraphs 97-98, in relying on a comprehensive dataset that precludes the reasonable consideration of less-likely explanations.

The Definition & Context of Cognitive Liberty
With respect to an adequate definition, Neuroethicist Dr. Nina Farahany describes it as follows in the aforementioned Harvard Gazette article;
“Cognitive liberty is the right to self-determination over our brains and mental experiences, as a right to both access and use technologies, but also a right to be free from interference with our mental privacy and freedom of thought,” said Farahany. [...] Corporations and governments are already hacking into people’s brains. [...] There is a very Orwellian vision of this future that’s ahead of us if we don’t make some radical changes now. I am optimistic in this moment that those kinds of radical changes are possible, and that we have the political will and the collective consciousness to do so. But if we don’t make those choices, it won’t be good.”
UN General Assembly Resolution A/HRC/57/61 was adopted by the Human Rights Council in response to A/HRC/RES/51/3, which recognized at its first page the severe repercussions Cognitive Liberty crimes pose, in "connecting the human brain directly to digital networks through devices and procedures, among other things, to access, monitor, and manipulate the neural system of the person" (here). Per A/HRC/57/61 at paragraph 5;
“Neurotechnologies are unique and socially disruptive because they generally: (a) enable the exposition of cognitive processes; (b) enable the direct alteration of a person’s mental processes and thoughts; (c) bypass the individual’s conscious control or awareness; (d) enable non-consensual external access to thoughts, emotions and mental states; (e) are nurtured by “neurodata”, which are needed for their own functioning, calibration and optimization; and (f) collect, analyse and process large personal datasets of a highly sensitive nature.”
Dr. Yuval Noah Harari writes at paragraph 306 in Homo Deus: A Brief History of Tomorrow (here);
"At the beginning of the third millennium, liberalism is threatened not by the philosophical idea that ‘there are no free individuals’ but rather by concrete technologies. We are about to face a flood of extremely useful devices, tools and structures that make no allowance for the free will of individual humans. Can democracy, the free market and human rights survive this flood?"
Finally, Dr. Klaus-Gerd Giesen writes in Transhumanism as the Dominant Ideology of the Fourth Industrial Revolution (here);
“Transhumanist thought can be broken down into three main premises, each with an eminently political intent: Human beings in their ‘natural’ state are obsolete and ought to be enhanced by technology, which then becomes a means of artificially extending the hominization process. Thus, transhumanism sweeps human taxonomy into the political arena. An observation by Michel Foucault, written in 1976, comes to mind: ‘What might be called a society’s threshold of modernity has been reached when the life of the species is wagered on its own political strategies. [. . .] Modern man is an animal whose politics places his existence as a living being in question.’ In other words, transhumanists believe we have a duty to replace the category of human with a new creature, a post-sapiens sapiens.”
Dr. Giesen continues in the text;
“If government agencies and international organizations — including the Council of Europe — are heavily involved in the infrastructure underpinning ideological dissemination, it is even less surprising to see that the Silicon Valley elite also ascribe to and promote transhumanist ideology. The same goes for the countless start-up entrepreneurs who gravitate toward these ideas. Carrying great weight in the societal debate are the unprecedented sums invested by, among others, the billionaires Elon Musk (one of Musk’s companies, Neuralink, aims to harness efforts toward the development of superintelligent cyborgs), Peter Diamandis, and Peter Thiel — not to mention the inescapable GAFAM (Google, Apple, Facebook, Amazon, and Microsoft), well aware that their commercial interests in the high-tech space are directly at stake. These tech giants have already poured staggering amounts of money into the Fourth Industrial Revolution and are currently spending equally eye-watering amounts on political lobbying and social engineering initiatives.” [...] There is every reason to fear that the world will launch into the fourth industrial revolution without too much debate over what is waiting in the wings: the global political project that is transhumanism. Today, it is as if the metamorphosis, via the “NBIC Great Convergence,” to a posthuman being, technologically enhanced and fully integrated with the machine, were already written in stone.”
Finally, at the conclusion of his publication;
“This is not an equal struggle. The societal debate has barely begun, and the dice are loaded. Transhumanist ideology is driven by certain factions within the state and, above all, by mighty multinational corporations that, it is fair to say, have the most to gain from seeing the NBIC revolution unfold without a hitch. In this respect, transhumanism is already a dominant ideology, as it crushes all other ideological positions regarding technological change — particularly those of humanists of all stripes and subscribers to “deep ecology” — under the sheer weight of money.”
The Appropriate Test Criteria
Although novel in the opinion of most, the UN Resolution and recent publications like those aforementioned preclude a summary preemptive dismissal of cognitive liberty crime as fanciful, similar to the fact that one is unable to dismiss credible allegations of tax fraud, without actually looking at the records. The aforementioned test in Sherman Estate v. Donovan, 2021 SCC 25 at paragraphs 97-98 requires that inferences involving harm need not be shown to be likely, but must be more than negligible, fanciful, or speculative. The text reads;
“This Court has held that it is possible to identify objectively discernable harm on the basis of logical inferences (Bragg, at paras. 15‑16). But this process of inferential reasoning is not a licence to engage in impermissible speculation. An inference must still be grounded in objective circumstantial facts that reasonably allow the finding to be made inferentially. Where the inference cannot reasonably be drawn from the circumstances, it amounts to speculation (R. v. Chanmany, 2016 ONCA 576, 352 O.A.C. 121, at para. 45) [...] Where the feared harm is particularly serious, the probability that this harm materialize need not be shown to be likely, but must still be more than negligible, fanciful or speculative.”
Likewise per R. v. Loewen, 2010 ABCA 255 at paragraph 32 concerning the police test for reasonable grounds; a subject need only demonstrate that an allegation is objectively reasonable to believe; not that it is probable or certain. As such, in the absence of hard scientific evidence, one must rely on the guidance of the same legal tests, in concert with a grounding in the factual evidence concerning contextual background and circumstances. As a preliminary consideration, the otherwise right-minded victims of a cognitive liberty crime can be approached in exploring subject baseline behaviors as measured against extreme outliers and related events.
Compelling Behavioral Outliers
In February 2021, I was compelled to call an ambulance during a blizzard, in response to an anomalous health incident that could not be reasonably attributed to a natural cause. I was at home at the time. The localized pain endured at the same intensity for roughly 90 minutes before I called 911. I received an injection of pain medication in the ambulance on the way to the ER. The Doctors were at a loss for an explanation as to the cause. I consider this event noteworthy of mention insofar as it bore the hallmarks of an electronic attack, for lack of a better term (see commentary on the Havana Syndrome here).
In July 2021, as a Nova Scotia resident, I retained a British Columbia law firm to act on my behalf in a shareholder dispute detailed (here), involving a Federally-sponsored Commercial and Government Entity ("CAGE"). Irrespective of the characteristics that had unfolded concerning the CAGE, a number of extreme outlier events had manifested. I had listed my newly-renovated home for sale, packed my bags, and relocated to BC in further "support" of the same lawsuit, without any objectively reasonable explanation. These actions served no practical purpose, or psychological purpose for that matter. By background yields a lifelong history of risk-averse behavior, and prudent decision-making through all seasons. Those familiar with me would suggest I am often loath to drive across town to attend a function I enjoy, let alone drive across the country to pursue a legal matter that was being handled by a law firm in the same area, and list my dream home for sale on MLS. Likewise on record, I had adopted a gradual approach in considering legal action against the CAGE for over ten months as a shareholder, and only after the evidence was found to be insurmountable, in collaboration with the legal counsel I had retained in BC (here).
With respect to further context, I had worked for years to develop my personal real estate, which was at that time fully paid for and renovated. I had two motorcycles in the garage, a specialty sports car in the driveway, an exotic pet, all paid-for, and a six-figure bank account. That required a lot of work to achieve, and I did it through discipline and smart choices over the span of several of years. Because the law firm I retained in BC could have handled the matter while I remained in Nova Scotia, there was no merit nor value in the excursion, or the home sale. On arrival in BC in late July 2021, I remained in a Condo from August through October while coordinating with the law firm on the shareholder dispute. My home sold in late September that year. Following the close of the settlement in October 2021, I drove back to Nova Scotia from British Columbia by car to reside with a family member.
Two weeks following my return to Nova Scotia, during the first week of November 2021, I found myself once again driving to British Columbia. I had no distinct plan in mind; only that I was under the impression that the shareholder matter remained unresolved, and that I had to return to BC again in person to address it. Irrespective, I made no plans nor preparations to visit the court upon my return. I arrived in Surrey, BC on November 10th, 2021 to a condo I had rented through Craigslist. The disruptive events described in the Zersetzung, Guide, and Q/A pages began within two weeks after the move. To reiterate, I signed a one-year lease without a vision, without employment, and drove across Canada again after emerging from a perilous shareholder dispute. That is about as far removed from my typical decision-making as ice is to fire. These actions are just as absurd as the adjudicative concurrence detailed in the related civil proceedings, and the actions taken by various public servants in the scandal (see Blog).
These behaviours are not readily explained by ordinary stress responses or life changes when measured against my long-documented baseline. They present as abrupt, high-cost departures (asset liquidation, cross-country relocations, impulsive commitments) occurring while my general cognition—reasoning, communication, and professional functioning—remained intact; what appears altered is the decision-making architecture itself. This presentation is consistent with research showing that targeted neuromodulation (e.g., TMS and vagus-nerve pathways) can bias judgment, risk appraisal, and impulse control without measurable global cognitive decline. The outliers, far removed from a lifelong behavioural baseline, served no discernible psychological function.

Click to Expand.
A Comprehensive Evidentiary Corpus
Although each event is extraordinary, none alone conclusively proves a covert assault on cognitive liberty, state-adjacent or otherwise. Considered together—against the full event chronology since 2021 and the recurring pattern of anomalies across venues—they satisfy the coherence-based circumstantial-inference test endorsed by the Supreme Court of Canada. See Sherman Estate v. Donovan, 2021 SCC 25, paras 97–98; R. v. Kahsai, 2023 SCC 20, para 67 (citing R. v. Wolkins, 2005 NSCA 2, para 89). Under the same standard, a clandestine program employing discreet brain–computer-interface technologies is the most plausible explanation, displacing less-likely alternatives (R. v. Villaroman, 2016 SCC 33, paras 35, 41, 56). Crimes such as this are actionable under the Crimes Against Humanity and War Crimes Act (S.C. 2000, c. 24) [Link].


Deep-Dive the Proceedings [Here]







Explore the Technicalities at the 4IR Page [Here]



Horizons and Ease in Neurotech Utility. Policy Horizons Canada Mirrors the Engagement Below. [Here]






Proximate Historical Events
Sophisticated Criminal Mischief
Soon after my second move to BC, I began facing near-daily on-heels stalking in public. Serial home intrusions and vehicle break-ins followed each week. My devices—laptop and phone—were evidently compromised; one direct cyberattack delivered video of the interior of my Surrey condo alongside a caricature of the CAGE director. My online environment appeared algorithmically sandboxed, with search results and feeds funneled toward content from a coordinated cohort engaged in criminal harassment. This pattern is detailed at the Guide page, and aligns with the findings in Sheridan et al., 2020; and BAE Systems Detica and London Metropolitan University, 2012.
Alongside caricatures of the CAGE director, the same actors surfaced through compromised device sessions and coordinated YouTube/TikTok accounts (see the Zersetzung page). Their posts repeatedly telegraphed day-to-day events inside and outside my home, while pushing narratives tied to my 2013 timeline and the shareholder settlement. The method matches classic Zersetzung—targeted destabilization associated with the Stasi—updated through social platforms and algorithmic amplification. Several behaviours also parallel admissions about domestic “influence activities” in CAF whistleblower materials first reported by the Ottawa Citizen in 2021 (the Gosselin Reports), including social listening, psychological operations, CIMIC, and influence activities directed at Canadians. On their face, these activities engage multiple Criminal Code offences—criminal harassment (s.264), intimidation (s.423), unauthorized use of a computer (s.342.1), and mischief in relation to data (s.430(1.1)), counsel to commit terror (83.221), among others.
The scope, consistency, and characteristics of these “Zersetzung” activities were severe since inception. Concurrently, practical aspects of my life, which I had consistently maintained for the majority of my adult life, were cast into disarray. Existing relationships and new business opportunities were compromised, and likewise new professional engagements with prospective work opportunities went awry through no mistake or misstep, and whereas a number of new opportunities had evaporated in an a-priori capacity. The newness and distinction of this trend should likewise be compared to the consistency of my BIO and living habits as a law-abiding citizen who quietly focused on his work and hobbies.
Shortly following the inception of these events, I made diligent attempts to seek safe avenue from a local RCMP detachment in Surrey, BC, not far from where I was domiciled (here). I was eventually able to meet with an officer, who greeted me outside the building, clad in a "Mental Health Division" uniform. This officer listened intently to my account, complimented me on detailed articulation of the events, but declined to open a file or act in any capacity in response, and refused to obtain CCTV footage from the building I was domiciled in. The criminal harassment and mischief continued unabated.
In mid-January 2022, I experienced an "electronic attack" through my smartphone while viewing content delivered through the aforementioned criminal cohort. I experienced an acute flash that elicited a physical sensation in my eyes that resembled a non-contact tonometry test that one might experience during a routine visit to an optometrist (ie., the "air puff test"). That happened only once, and I am unable to identify any analogues. A subsequent check-up revealed anomalies in my retina that were not present in any previous records.
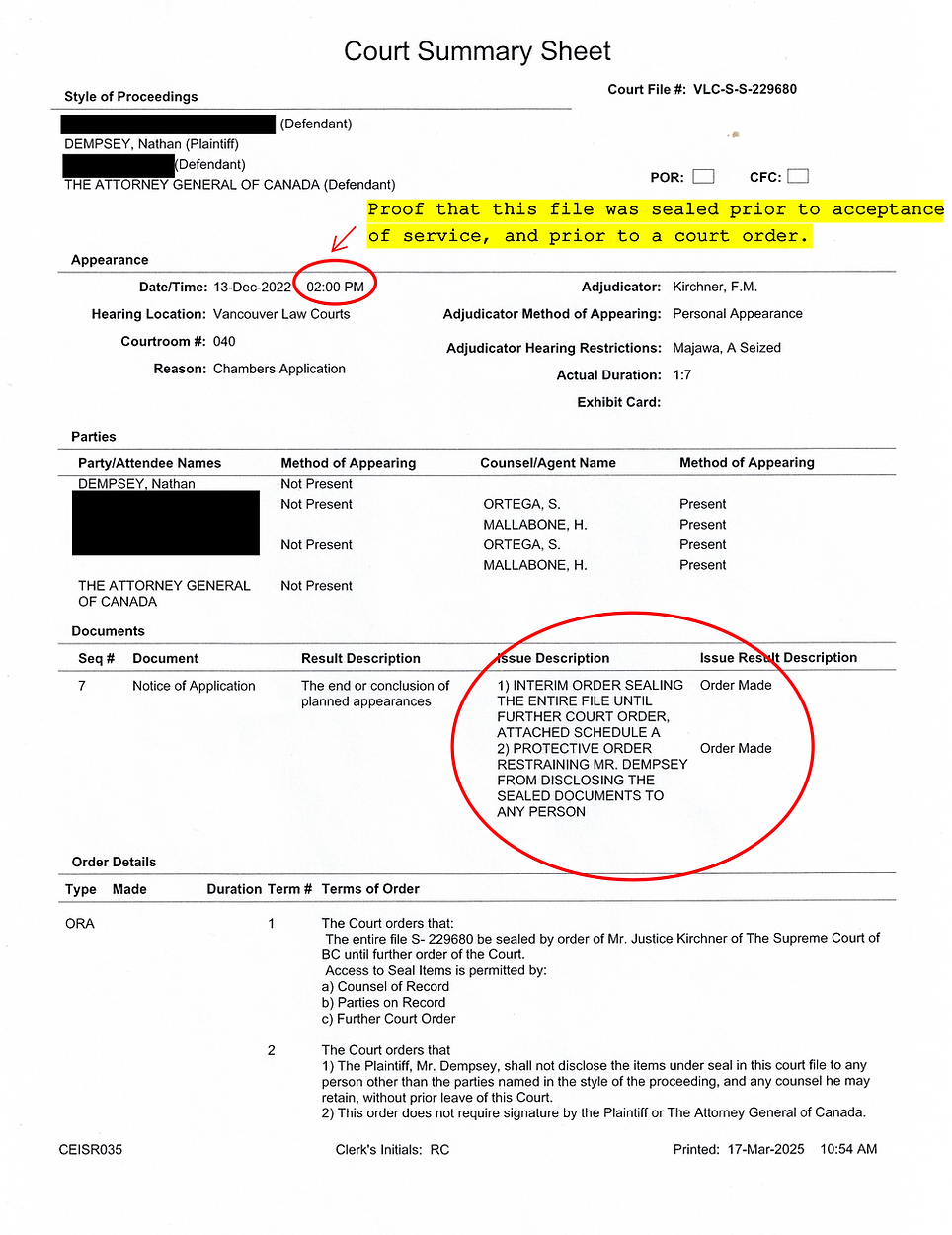
On February 8, 2022—after another remote PC-intrusion that displayed a caricature of the CAGE director alongside threats, and after repeated but unsuccessful attempts to obtain RCMP assistance—I filed, as a precaution, a draft Petition in the B.C. Supreme Court (Vancouver Registry) with an Affidavit sworn the month prior. Amid proximate concerns, that Affidavit set out evidence of perjury arising from the earlier settlement dispute. While Hawitt v. Campbell, [1983] CanLII 307 requires an ethical reconsideration of a troubled settlement, I had no intention of launching fresh litigation under life-threatening conditions, unemployed and unrepresented. The file, BCSC S-220956, is now subject to a blanket sealing order that ignores Constitutional guardrails (here). As with compromised business prospects, I was unable to secure new counsel at the time—or thereafter—including Pro Bono services for which I met the criteria (here). Compounding matters, prior counsel had already jeopardized the shareholder dispute by filing confidential shareholder materials at the Vancouver registry without a sealing order—an error no trained lawyer should make—which enabled a bad-faith notice of shareholder default shortly after a consensual sealing remedy was entered (here).
On February 16th, 2022, following a series of home invasions and another remote (PC) hijack event threatening imminent abduction, I evacuated my rented condo residence that same evening, and packed whatever belongings I could fit into my car. I traveled across Canada by car in mid-February 2022 to arrive in Nova Scotia, where I currently reside with a relative at the time of this update. The same day I departed, the windows of my condo unit had been completely covered by an opaque tarp depicting a Canadian flag; a feature which was likewise cited during the PC hijack event. I was repeatedly photographed in the elevator and parking lot as I departed. I could hear persons in the adjacent condo describing a real-time PC hijack as it was taking place, shouting and hollering loudly. Again, the RCMP had refused to obtain CCTV video footage upon being asked, as is described in the apology letter of RCMP Superintendent Bill Parmar shown. The RCMP continues to preclude support, despite applicable standards, and the CRCC turned a blind eye. The incriminating RCMP and CRCC letter correspondence and reports are cited (here).
In the days that followed my arrival in Halifax, NS, I was preemptively referred to as a “political target” by the owner of a specialty computer shop, whom I approached to investigate my compromised laptop. I was unable to get my PC investigated at any specialty shop. Shortly after my arrival, stalking began in a similar capacity as it had manifested in Surrey and New Westminster BC, and new CIMIC activities had began. I was likewise approached by an individual in plainclothes who identified as a member of the Canadian Armed Forces (“CAF”). This person preemptively disclosed details concerning the events in British Columbia, along with another individual speaking through a smartphone on a live phone call, who likewise identified as CAF. These individuals uttered threats, and photographs were taken of myself and my vehicle before departure. It may or may not be relevant (but likely is) that the CAGE lead counsel is a uniformed legal advisor to the CAF.
A Post-Constitutional (Weaponized) Court Experience
I continued the case against the CAGE director in the BCSC via MS Teams. My affidavits—suffused with transcripts and exhibits—document a sustained pattern of obstruction from 2022 onward, following an April 1, 2022 order by a now-retired adjudicator directing the introduction of privileged audit evidence from the Canada Revenue Agency and three private entities tied to the shareholder dispute. The Litigation page sets out the three-year arc of what became a cross-provincial weaponization of adjudicative institutions. A condensed overview appears (here) for the BC proceedings, and (here) for the NS hearings. Despite the conditions that necessitated filing S-220956, a prima facie perjury issue in the CAGE CEO’s settlement affidavit—explicitly acknowledged by the BCSC on April 1, 2022—was later eclipsed by a certification of ~$400,000 in special costs payable to the CAGE. These special costs are non-compensatory, and were struck on the basis of retainer billings for nine (9) short-chambers hearings, each under an hour in duration with modest prep, often managed by articling students. In other words, a ~9,000% uptick vs. court tariff.
The CAGE lead counsel’s sworn affidavit in BC assigns seven lawyers and two paralegals to overlapping tasks, with egregiously large time blocks, and asserts 737.7 billable hours (like the passenger jet) were reasonably required to handle a handful of short-chambers appearances, with a combined total of 867 minutes on record (October 17th, 2023 Affidavit of Emily MacKinnon, at paragraph 10, S-220956). This data is fraudulent on face: no reasonable client would agree to such retainers for this scope of work, no reputable firm would propose them, and no unbiased adjudicator would certify them without rigorous arithmetic and legal scrutiny. The pattern inexorably suggests the participants believed the billing would be insulated from consequence by assurances—formal or informal—from someone with the power to provide them across venues. By comparison, customary tariffs for hearings under one hour are customarily capped at $500 per hearing, including preparation (ie., NS Rule 77).
An affidavit from CAGE counsel in Nova Scotia lists $6,518.50 for four hearings under one hour (including prep)—a benchmark that starkly underscores the implausibility of the BC retainer (737.7 hours / ~$400,000 for nine short-chambers appearances). Yet judges in NS enforced the BC execution order as if nothing were amiss. Such lack of discretion is an error in law (Beals v. Saldanha, 2003 SCC 72 at paragraph 220). Compounding this, a series of orders miscast the event chronology atop a sealed file, materially damaging my professional reputation. The Supreme Court of Canada declined to place the matter on its docket, and the same errors—together with overt rule breaches facilitated by registry staff—were replicated in the appellate courts. Collection efforts had since triggered an autoimmune health risk through a brief custodial sentence in 2024, and now (approaching 2026) threaten homelessness. Prospective fiduciary counsel have repeatedly declined engagement; a trend that had continued since 2022. Even so, I have assembled an extensive body of relevant jurisprudence which, read alongside the evidentiary record, reveals a serious miscarriage of justice to fair-minded observers. The persistent appearance of injustice satisfies the standard at R. v. Wolkins, 2005 NSCA 2, at paragraph 89; see a compiled list of authorities (here).
Biometric Data & the Dark Web
Over the course to the past three years, the crimes in the Guide page have continued unabated. The modality of certain crimes require modalities of real-time, or near-real-time surveillance capability. As is detailed in the aforementioned UN Resolution, remote neuromodulation applications through wave frequencies and light have been available for some time. Remote brainwave data collection via injectable or inhalable nanoparticles represents the convergence of three documented realities: technological capability (graphene quantum dots crossing the blood-brain barrier to interface with neural tissue), institutional enablement (DARPA-funded research creating "neural dust" systems for wireless brain-computer interfaces), and operational deployment against unwitting human subjects serving as guinea pigs for technologies requiring extensive real-world testing before commercialization. Peer-reviewed literature documents that graphene quantum dots (GQDs)—nanoparticles between 2-10 nanometers in size—can cross the blood-brain barrier through inhalation or injection, interface with neural electrical activity, be remotely powered by external electromagnetic fields, and transmit harvested neural data via backscatter communication. This enables "precognitive evidence": external actors demonstrating knowledge of target's decisions before actions or communications occur, because they monitor intention formation at the neural level. UN Human Rights Council reports A/HRC/57/61, A/HRC/58/58, and UN Resolution A/HRC/RES/58/6 explicitly warn that neurotechnology poses "particular risks to institutions requiring independent judgment, including the judiciary" and that applications "might lead to modification or manipulation of thoughts inside the brain".
Case study evidence—including 2021 behavioral baseline deviations inconsistent with twenty-year documented patterns, timing correlations between sealed court filings and external events, biometric data trafficking on dark web markets, military personnel describing my situation preemptively, and systematic institutional coordination preventing examination across police, courts, and regulatory bodies—exhibits a pattern consistent with an unauthorized neurosurveillance deployment. The absence of legal frameworks recognizing cognitive liberty and mental privacy as fundamental rights, combined with detection challenges (GQDs are invisible to standard medical imaging) and institutional coordination preventing specialized testing, creates ideal conditions for covert human experimentation. Market incentives (biodigital convergence valued in the billions) and intelligence applications (precognitive behavioral prediction) ensure continued deployment absent immediate regulatory intervention establishing: Constitutional recognition of neurorights; criminal prohibition of unauthorized neural monitoring; mandatory informed consent; public detection infrastructure; and burden-shifting where circumstantial evidence warrants specialized examination.
Consistently Denied Help by Police
Law enforcement agencies, whose task it is to protect citizens and uphold their rights as protected by the Charter in Canada, have consistently acted in a way antithetical to their function. All manner of law enforcement agencies contacted have made concerted attempts to dismiss and/or discredit my requests for help, to the extent that false reports were filed. This data point is extremely compelling. Despite an obvious appearance of injustice, I have been careful in ensuring the standards I rely on concerning police response align with the standard legal tests listed (here).
I eventually secured a lengthy meeting with Halifax Regional Police that lasted one hour and nineteen minutes, during which the officer directly acknowledged my evidentiary record, specifically identified the CAGE Director and his involvement in AI-assisted criminal interference, and further proposed an investigative roadmap. However, after that meeting, the same officer filed a police report containing an entirely different account of our interaction, suffused with pejorative ad-hominem framing. This report—obtained through a FOIPOP request—stands in stark contrast to the recorded facts and constitutes the fabrication of evidence, an indictable offence under section 137 of the Criminal Code of Canada, punishable by up to fourteen years’ imprisonment. Given the persistent denial of redress in other fora, I had discreetly recorded the meeting pursuant to CCC 183.1 and supplied an unaltered audio transcript in affidavit form together with the FOIPOP disclosure. The applicable records concerning my engagement with HRP are found (here). The obstruction is plain to see.
A Family Connection
Estranged relatives are implicated in connection with a prominent individual presently associated with ongoing criminal mischief, as shown in the image below. The person pictured in the center is understood to be the biological mother of my estranged nephew (right), through an egg donation procedure at a Halifax, NS fertility clinic. Three estranged family members are named in related affidavit evidence, first sworn on May 20, 2022. The full details are outlined in the Family Affidavit (here). While reference is made to the Freemasons—an association that might understandably raise concerns about speculative or conspiratorial framing—this element may or may not hold material relevance to the underlying scandal. Having said that, it does correspond to the recurrent occult and esoteric motifs suffused in the dossier. In plain terms, I am confronting individuals and entities of considerable influence. What appears to be a central project interest is accompanied by peripheral actors seeking to capitalize on its momentum. Regardless of operational modality, these interests are criminal in nature.



"Presents"



Police regulators refused to address these matters, and likewise, the scandal originating at the BCSC remained unchecked in appellate venues, and facially-fraudulent solicitor-client billing in excess of my life savings continues to be coercively enforced in NS, absent all manner of extant discretionary guardrails. It was likewise precluded from docket entry at the SCC despite the applicable test criteria (R. v. C.P., 2021 SCC 19 at para. 137). Because a single federally-sponsored CEO cannot be expected to shape the disposition and conduct of five courts, three police agencies, and relevant regulatory bodies—and sustain the support of over fifty (50) PsyOp contractors over a three-year period—an inference of third-party tampering is required, alongside assurances to the CAGE, its law firm, and participating public stakeholders. In plain terms, the scandal has the characteristics of a softkill effort. Whereas I am but an innocuous citizen, these disproportionate effects are predicated on a project interest, with adjacent personal and commercial interests opportunistically affixed to the primary driver.
Who Initiated?
By way of an evidentiary record connecting the CAGE entity to zersetzung actors and the foregoing events, it might be reasonable to assume that the entirety of the matter might be predicated on the CAGE entity itself. Yet as noted above, the evidence does not support this hypothesis, nor would the scope, sophistication, and duration of events justify the cost of the state supporting just one company director. Instead, the evidentiary record suggests the CAGE entity acted in cooperation within a program.
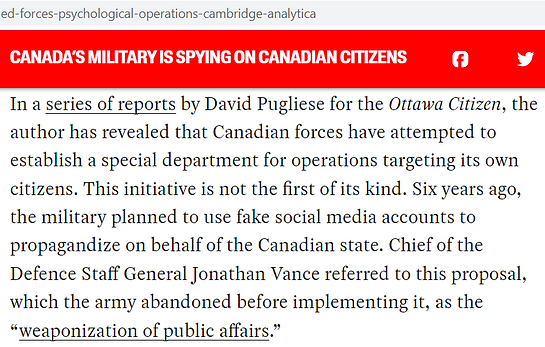
The Gosselin Reports outline a troubling account of the Canadian state surveilling and profiling its own citizens, and moreover, utilizing its tools and resources, including enlisting the support of civilian actors, to conduct InfoOps and PsyOps on unaware and unsuspecting Canadian Citizens. Whereas there now exists an evidentiary record of state-sponsored social engineering, there are further records to consider by way of an examination of materials published by the Government of Canada, the United Nations, and the World Economic Forum (“WEF”).
Visual Evidence & Precedents You Can't Ignore [See Guide]








As above per the embellished HRP report that was provided to EHS.
Full details at the HRP Page (Here).



May 13, 2023 Live Audio Recording Hfx QE II

_1.png)








Could it be That State-Sponsored Scandals no Longer Happen..? [See Whistleblowers]












The Scandal Remains Sealed in All Court Files [Click the BLOG]

WEF/United Nations Agreement
CANADA’S 2030 AGENDA
The “Shared Blueprint” Commitment
Canada’s 2030 Agenda National Strategy is attached to the UN program as a “shared blueprint… for partnership, peace and prosperity… now and into the future,” anchored by a pledge to “leave no person behind”. Read in context, “shared blueprint” signals policy alignment with a global framework—not an à-la-carte sampling of UN guidance, nor a wholly independent domestic design. The Charter remains the constitutional touchstone, but its application now unfolds inside a policy environment shaped by international commitments and administrative norms keyed to UN benchmarks. The constitutional question follows: when parameters are set by frameworks operating beyond electoral accountability, does democratic sovereignty shrink into retrospective ratification of decisions made elsewhere?
Policy Horizons Canada: WEF at the Strategic Core
Policy Horizons Canada—Ottawa’s foresight hub—is chaired by Kristel Van der Elst, formerly the WEF’s Head of Strategic Foresight and now CEO of The Global Foresight Group. This is not a peripheral appointment: it sits atop the institution tasked with scanning emergent risks and opportunities for federal policy. Horizons has prominently explored biodigital convergence, Fourth Industrial Revolution (4IR) applications, and transformation scenarios that track closely with WEF playbooks. The effect is structural rather than speculative: long-range Canadian policy cognition is formed within a vocabulary of transhumanism, technological determinism, multi-stakeholder governance, and 4IR as necessary infrastructure for global objectives.
The UN–WEF Strategic Partnership: Formalizing Corporate Influence
On June 19, 2019, the UN and the WEF signed a Strategic Partnership Framework to “jointly accelerate implementation” of the 2030 Agenda, positioning the WEF as a strategic delivery partner. Coupled with Canada’s “shared blueprint” posture, the pathway is straightforward: WEF partners with the UN to drive the SDGs; Canada adopts the SDGs as its template; WEF priorities reach Canadian policymaking through the UN conduit. More than 200 civil-society organizations criticized the deal on democratic and transparency grounds. Three representative critiques:
-
Gonzalo Berrón (Transnational Institute): the agreement “formalizes a disturbing corporate capture of the UN,” pushing toward “privatized and undemocratic global governance.”
-
Harris Gleckman (former UN official): a “coup for the corporate leaders at Davos,” granting “unprecedented access to the heart of the UN” without broad member-state or public debate.
-
Sofia Monsalve (FIAN International): the UN must distinguish private interests from rights-holders; the WEF “cannot be considered a strategic partner” for solving global crises.
The core objection is role confusion. In a Constitutional order, citizens hold rights, governments wield public power answerable to those citizens, and corporations operate within democratically enacted limits. When a corporate-membership forum becomes a “strategic partner” to the UN—and UN frameworks become national “blueprints”—the lines blur. Corporate priorities shape global templates; global templates shape domestic commitments; voters are left to endorse outcomes already pre-structured by partnerships they neither approved nor can meaningfully contest.
Multi-Stakeholder Governance: From Proposal to Practice
This architecture did not appear overnight. Beginning in 2009, the WEF’s Global Redesign Initiative (GRI) proposed multi-stakeholder governance (MSG)—corporations, foundations, NGOs, and other non-state actors sharing agenda-setting and delivery—as a partial substitute for classic intergovernmentalism. Over 18 months, ~40 councils spanning business, academia, government, media, faith, and civil society produced a 600-page synthesis of proposals and principles. Crucially, MSG does not depend on formal treaty approval; it advances de facto through partnerships, pilots, and platforms. The 2019 UN–WEF pact operationalizes the model: WEF (corporate stakeholders) + UN (member states) = accelerated SDG delivery. Countries like Canada, having adopted the SDGs as a “shared blueprint,” inherit a policy pipeline coordinated by “stakeholders” rather than directed exclusively by electorates.






The WEF's Great Reset
THE GREAT RESET: TRANSHUMANISM AS GOVERNANCE INFRASTRUCTURE
Introduction: The Pandemic as Transformation Catalyst
Since mid-2020, the World Economic Forum has promoted a post-coronavirus program it calls “The Great Reset”. Its premise is sweeping: the pandemic exposed structural fragilities, creating an opportunity to rebuild on new foundations. What distinguishes this agenda from routine crisis management is its implicit embrace of transhumanism—the use of technology to transcend biological limits by integrating digital systems with human bodies and minds. The Reset is framed not as an ad-hoc policy bundle but as a comprehensive re-platforming of social order on a technological substrate.
The Fourth Industrial Revolution as Reset Infrastructure
Klaus Schwab links the Reset directly to the Fourth Industrial Revolution (4IR)—AI, the Internet of Things, biotechnology, neurotechnology, and gene editing. The stated aim is “to harness the innovations of the Fourth Industrial Revolution to support the public good”. In this framing, 4IR systems are not discretionary tools; they are governance infrastructure. Schwab’s claim that 4IR will “fuse our physical, digital, and biological identities” moves beyond productivity to transformation of the subject itself. The implication is operational, not merely philosophical: the institutions of coordination, measurement, and control will increasingly run through sensor networks, data pipelines, and algorithmic decision-systems with human beings coupled to the loop.
Canadian Implementation: Cabinets and Governing Bodies
Schwab has publicly said the WEF has “penetrated cabinets”. Canada shows how influence and office can intertwine. Senior figures have engaged deeply with WEF initiatives. Mark Carney—former governor of the Bank of Canada and the Bank of England and now Prime Minister—has served on the WEF Board of Trustees, as has Chrystia Freeland, who simultaneously held multiple senior portfolios in Ottawa, and had migrated through no less than five ministerial posts. The head of Canada's foresight think tank Policy Horizons, Kristel Van Der Elst, was formerly the WEF Foresight Director. The Board is the WEF’s highest governing body for strategy and stewardship. When individuals sit at that table while holding high public office, the question is not conspiracy but conflict: which priorities prevail when national accountability and transnational playbooks diverge?
The UN 2030 Agenda: “Shared Blueprint” and Lock-In
Ottawa’s endorsement of the UN’s 2030 Agenda as a “shared blueprint” converts international aspirations into a domestic operating framework. “Shared” signals coordinated alignment; “blueprint” signals pre-designed schematics rather than open first-principles debate. Coupled with the claim that 4IR is necessary to deliver the Sustainable Development Goals, the pathway is clear: the UN sets objectives, the WEF curates the toolset, and national administrations mobilize a “whole-of-society” coalition to execute. Once agencies, vendors, NGOs, and platforms are architected around shared targets and interoperable data, reversal becomes structurally difficult regardless of electoral turnover.
Transhumanism as Operational Philosophy
The Reset tacitly advances a different theory of the human person. Traditional Constitutionalism presumes a stable human nature to be protected and ordered. Transhumanist governance presumes a malleable human nature to be optimized and, where useful, redesigned. The promised “fusion” is concrete: brain-computer interfaces link neural activity to algorithmic systems; gene editing re-specifies biological traits; ubiquitous sensing binds identity to continuous data exhaust. What was once opaque—thought, intention, affect—becomes legible, quantifiable, and steerable. That alters the risk profile of state and corporate power in ways older legal doctrines do not neatly address.
The “Public Good” Inversion
Within this architecture, “public good” is quietly redefined. Historically it meant safeguarding liberties, equality before the law, and due process. In Reset practice it becomes rapid attainment of targets—pandemic mitigation, climate benchmarks, financial inclusion, safety. If mind-monitoring, behavioral nudging, or identity fusion improve target attainment, cognitive privacy appears as friction. The individual’s protected interiority is reclassified as an optimization problem. Constitutional limits—once hard boundaries—start to look like tunable parameters.
Episodes, Crises, and the One-Way Ratchet
Crisis narratives power a ratchet that turns one way. Each failure—pandemic chaos, climate shock, economic dislocation, a publicized miscarriage of justice—justifies more centralization, tighter coordination, and deeper instrumentation. Those measures generate new pathologies—opacity, overreach, bias—which are then cited as evidence for further consolidation. My own file fits the pattern: documented non-engagement by police, courts, regulators, and law societies can be framed not as a call for accountability, but as proof that only greater integration, surveillance, and automation can “fix” systemic gaps.
Constitutional Implications: Predetermined Parameters
Charter rights presuppose contestable policy, personal sovereignty over body and mind, bounded power, and judicial enforcement. A governance model organized around a supranational blueprint, implemented through stakeholder networks, and instrumented via invasive technologies strains each assumption. If decisive arenas migrate from Parliament and open court to standards bodies, private platforms, and data pipelines, constitutional text can remain pristine while practical protections recede. The danger is not formal repeal but functional erosion: rights become ceremonial while decisions harden elsewhere, in code and contracts.
What Cabinet Penetration Looks Like in Practice
“Penetrated cabinets” does not require clandestine meetings to matter. It operates through agenda-setting, personnel pipelines, shared scenarios, and common risk frameworks. The same playbooks and readiness exercises shape both domestic officials and transnational councils. Harmonization becomes default; divergence, an exception that demands justification. When media, academia, and civil society are enlisted as “stakeholders,” oversight blurs into mobilization and watchdogs become participants. Democratic choice then narrows to tempo and tone; the course is preset by interoperability requirements and external benchmarks.
Vigilance and Transparency are Required, as are Conversations
None of this denies that 4IR tools can save lives or that coordination can solve real problems. The questions are authority and constraint. Will Canadians insist that any deployment with power to read or modulate thought, alter biology, or render participation effectively compulsory be fenced by bright-line law—explicit statutes, demonstrable necessity, strict proportionality, independent oversight, a genuine right to refuse, and non-derogable neurorights such as cognitive liberty, mental privacy, and bodily integrity? Or will these capabilities accrete as baseline infrastructure, making consent nominal and exit impossible?
Conclusion: Reset as Fait Accompli—or Bounded
The Great Reset presents itself less as proposal than as momentum. The pandemic supplied the catalyst; the UN provides objectives; the WEF supplies philosophy and tooling; cabinets supply authority. What remains is citizen enforcement. Either Canadians reaffirm that the public good begins with sovereignty of the person and the primacy of law, or the country drifts toward a condition where thoughts may be read, behavior nudged at scale, and identities fused to infrastructure owned and governed elsewhere. Constitutionalism endures on paper—but without ex ante guardrails and real remedies, its protections become theater.

Asymmetry in UN SDG Enablement
THE OPERATIONAL SUBSTRATE: HOW 4IR ENABLES THE 2030 AGENDA
I. Introduction: The Technological Foundations of Global Governance
The United Nations’ 2030 Agenda—expressed through 17 goals, 169 targets, and over 230 unique indicators (the "SDGs")—reads like a sweeping social compact: end poverty, universalize health and education, protect the environment, reduce inequality. Less visible in the public framing is the operational grammar of that compact. Its architecture presupposes a data-saturated world: continuous sensing, identity and registry systems, interoperable databases, and predictive analytics capable of monitoring progress and triggering interventions across institutions and jurisdictions“. Leaving no one behind,” in practice, translates into knowing—persistently and at scale—where everyone is, what they need, and how they are responding to policy.
That operational layer is the terrain of the Fourth Industrial Revolution (4IR). As Klaus Schwab and the World Economic Forum repeatedly argue, many SDG commitments are not merely aided by digital systems; they are contingent on them. The shift from aspiration to delivery thus occurs through platforms and pipelines—sensors → data → models → decisions—rather than through policy statements alone. This is what makes the Agenda administratively plausible, and also what renders it Constitutionally fraught: when governance runs through ubiquitous telemetry and automated mediation, long-standing protections for autonomy, privacy, consent, and accountability are tested not at the margins, but at the core.
II. 4IR as Delivery System: From Vision to Infrastructure
This is not rhetorical flourish; it’s an operating plan. The World Economic Forum’s Frontier 2030 work with PwC maps SDG targets to concrete technologies, arguing that a majority can be delivered via digital systems across sensing, identity, data, and AI (here). Parallel WEF analysis finds 84% of current or potential IoT deployments address one or more SDGs, underscoring how measurement and optimization become the medium of governance rather than a mere tool (here).
Illustratively, the portfolio includes real-time environmental monitoring (SDG 6), digital identity rails for inclusion and service delivery (SDGs 1/10/16), AI-assisted agronomy (SDG 2), and blockchain-backed supply-chain verification (SDG 12)—all built to feed continuous feedback loops of data → model → intervention at scale.
Canada’s 2030 Agenda architecture (here) adopts this posture almost verbatim, calling for a “whole-of-society” mobilization that folds civil society, business, academia, and cultural organizations into the collection, analysis, and actioning of data against SDG targets. "Leaving no one behind", on this view, is not only a moral commitment but a systems-engineering mandate to make the substrate sufficiently comprehensive and responsive.
III. The Rhetoric of Inevitability: “Unstoppable” Movements and Stakeholder Mobilization
The UN Secretary-General’s 2019 “Decade of Action” call invited “all sectors of society” to mobilize at global, local, and “people” levels—“including… the media, the private sector, unions, academia, and other stakeholders”—to “generate an unstoppable movement pushing for the required transformations”. When civic actors (especially the press) are cast as mobilization stakeholders in a predetermined project, the line between independent scrutiny and program delivery blurs. In the Canadian context, that poses a Constitutional problem: freedom of expression under s. 2(b) presumes the press as an independent watchdog—described in Vancouver Sun (Re) as a conduit of public information about institutions—not an instrument of state-led (or transnationally led) campaigns. The UN sustainability article, which ran from 2020 until its deletion in April 2025, is archived (here).
The rhetoric of “unstoppable” and “required” signals a shift from democratic pluralism to policy inevitabilism. Citizens are not invited to deliberate ends, but to mobilize toward them. In that posture, dissent, revision, and even reasoned delay are pathologized; democratic choice is reduced to procedural ratification of outcomes settled elsewhere by expert consensus and algorithmic feasibility.
IV. Schwab’s Thesis: 4IR as Human Transformation, Not Just Process Automation
Klaus Schwab is the clearest public architect of this paradigm. In his book, The Fourth Industrial Revolution, and repeated WEF addresses, he stresses that 4IR is not chiefly about incremental efficiency but about reconfiguring the human substrate. As he puts it, the revolution is driven by “the fusion of… technologies and their interaction across the physical, digital, and biological domains,” which makes it “fundamentally different from previous revolutions”. The point is not better machines; it is a new ontology.
Policy Horizons Canada Director Kristel Van Der Elst, former WEF Director of Foresight, echoes the same sentiments at the PHC website (here);
"In the coming years, biodigital technologies could be woven into our lives in the way that digital technologies are now. Biological and digital systems are converging, and could change the way we work, live, and even evolve as a species. More than a technological change, this biodigital convergence may transform the way we understand ourselves and cause us to redefine what we consider human or natural. [...] We want to engage with a broad spectrum of partners and stakeholders on what our biodigital future might look like, how this convergence might affect sectors and industries, and how our relationships with technology, nature, and even life itself could evolve."
Schwab makes the identity stakes explicit: “It doesn’t change what you are doing; it changes you… If you take genetic editing as an example, it is you who are changed. Of course, it has a big impact on your identity” (here). This marks a qualitative break from prior mechanization, which left personhood’s boundaries largely intact. Gene editing, neural implants, and biodigital interfaces render the self programmable, observable, and optimizable—a shift that detonates standard assumptions about consent, autonomy, and mental privacy. In Constitutional terms, the regulated object is no longer merely conduct mediated by tools; it is the person as such.
V. Harari, Biological Reductionism, and the Engineering of Morality
If Schwab supplies the institutional blueprint, Dr. Yuval Noah Harari offers the philosophical groundwork. Across Davos stages and bestsellers, Harari advances a stark materialism: “There are no gods, no nations, no money and no human rights, except in our collective imagination… free will and liberty are myths… humans are simply hackable animals”. He later states in an interview (here) that "we must reinvent democracy for this new era where humans are now hackable animals". On these accounts, morality is not a limit external to power but a malleable product of culture—and thus open to design. What follows is an ethic of management: engineer beliefs and behaviors to reduce uncertainty and achieve system goals.
This outlook is mirrored in policy circles. Prime Minister Mark Carney writes in Value(s): “Moral sentiments are not inherent… they are social memes that are learned, imitated and passed on… [and] can mutate, in behavioural cascades and tipping points”. Read together, these positions normalize moral optimization: treat values as adjustable parameters in a governance model aimed at sustainability, stability, or security. Rights cease to be hard constraints and become variables in a policy objective function.
Here lies the Constitutional collision. The Canadian Charter—like liberal constitutionalism generally—treats core rights as categorical side-constraints, not as levers to be tuned. Recasting rights as optimizable inputs shifts law from boundary to algorithm: courts weigh asserted benefits against engineered moral sentiments; Section 1 deference expands under claims of systemic “necessity”; and the citizen migrates from a rights-bearer to a subject of behavioral design. Unless explicitly checked, a reductionist, programmable view of persons inexorably tilts institutions from guarding inviolable limits toward administering outcomes.
VI. Existential Threats and the Logic of Emergency
Harari frames 4IR adoption as an existential necessity. In his January 24, 2020 WEF address, he warned: “The global order is now like a house that everybody inhabits and nobody repairs. It can hold on for a few more years, but if we continue like this, it will collapse – and we will find ourselves back in the jungle of omnipresent war. We have forgotten what it’s like, but believe me as a historian – you don’t want to be back there… if we return there now, with the powerful new technologies of the twenty-first century, our species will probably annihilate itself.”
The “jungle” metaphor functions as more than history—it is a permission structure for suspending ordinary constraints. Rights built for “normal times” are recast as luxuries we “can’t afford” in a crisis. Canadian experience shows how easily exceptional measures become sticky: wartime powers, post-9/11 security laws, and pandemic regimes all illustrate how “temporary” incursions rarely revert fully.
Constitutionally, this rhetoric pressures Section 1 analysis toward deference: if the threat is framed as civilizational collapse, “pressing and substantial” is presumed, the evidence burden softens, and proportionality is judged against speculative catastrophe rather than concrete rights harms. When existential risk becomes a standing condition of governance, the logic of emergency risks hardening into everyday infrastructure: continuous surveillance, predictive control, and algorithmic triage normalized as precaution rather than exception.
VII. Identity, Personhood, and Consent Under 4IR
Schwab’s claim that 4IR “changes you” marks a categorical shift. Traditional doctrine—especially s. 7 security of the person—assumes a relatively stable rights-bearer and treats interventions as external (risk-managing) rather than identity-altering (self-modifying). Consent law likewise presumes: (1) the deciding self and the affected self are the same person; (2) effects are comprehensible ex ante; and (3) withdrawal restores the status quo ante.
Neuroimplants, germline edits, and biodigital integration destabilize each premise:
-
Diachronic identity: If an intervention predictably alters cognition, affect, or values, the post-intervention self may diverge materially from the consenting self. Whose preferences govern?
-
Informed comprehension: High-dimensional neural/genetic effects, networked dependencies, and long tails of risk strain what “informed” can realistically mean.
-
Reversibility: Neural adaptation and heritable edits can make withdrawal either impossible or itself injurious, undermining voluntariness.
-
Third-party stakes: Germline modifications externalize consequences to non-consenting descendants, raising intergenerational rights conflicts.
-
Structural coercion: When enhancement becomes de facto infrastructure for work, education, or civic life, “consent” collapses into compelled participation.
Doctrinal stress points follow across the Charter: s. 7 (bodily and psychological integrity; voluntariness), s. 8 (continuous cognitive/biometric capture that eludes “discrete search” logic), and s. 15 (capability castes: augmented vs. unaugmented). The legal subject—previously an unmodified human person—becomes a moving target, forcing first-principles choices: Which aspects of mind and body are non-derogable? What counts as meaningful consent when identity itself is in play? Without clear guardrails (neurorights, non-coercion, reversibility, intergenerational limits), the architecture of consent and personhood that underwrites Constitutional protection no longer holds.
VIII. Technological Infrastructure as Inevitable Environment
The most unsettling feature of the 4IR vision is how invasive systems are framed not as optional tools but as ambient infrastructure—the water and wiring of public life. In a 2017 WEF panel, Klaus Schwab put it starkly (here):
“Can you imagine in 10 years when we are sitting here, we have an implant in our brains… because you all will have implants. I can measure your brain waves and immediately tell you how people react…”
Three moves are doing the work here:
-
Universality: “You all will have implants” presumes default uptake, not individual choice.
-
Live cognitive capture: “Measure your brain waves” collapses the boundary between inner life and external observation.
-
Technological inevitability: The future is cast as determined; deployment is a matter of when, not whether.
Once invasive technologies are presented as infrastructure, the line between “voluntary use” and structural compulsion disappears. Access to work, education, services, and civic participation tends to be routed through the infrastructure; refusal becomes exclusion. In that setting, consent—the backbone of autonomy, privacy, and bodily integrity—turns from a meaningful safeguard into a formal checkbox.
Constitutional implications: frameworks built on discrete, opt-in events and episodic “searches” cannot absorb continuous, infrastructure-level extraction and modulation of cognition:
-
s. 2(b) / freedom of thought: Thought is no longer a private precursor to expression if neural states are continuously read.
-
s. 7 / security of the person: Identity-altering implants and neuro-stimulation invert bodily autonomy when participation is effectively mandatory.
-
s. 8 / unreasonable search: Always-on neural/biometric capture evades warrant logic tied to discrete intrusions.
-
s. 15 / equality: Infrastructure that privileges the augmented entrenches a capability caste.
If 4IR systems are allowed to harden into baseline infrastructure without ex ante guardrails—statutory authorization, necessity and proportionality, non-derogable neurorights, and a real right to refuse—the practical conditions for Charter protection erode, even if the text remains unchanged.



















Value(s): Building a Better World for All [Link] Prime Minister Mark Carney, 2021, ISBN 0008485240, P. 36, 95, 494
[36] “Moral sentiments are not inherent. To use the modern terminology of Richard Dawkins, they are social memes that are learned, imitated and passed on. Like genetic memes, they can mutate, in behavioural cascades and tipping points."
[95] “Magna Carta was a desperate and probably disingenuous attempt at a peace treaty that failed almost immediately. Brokered by the Church, and issued by King John in June 1215, the Charter sought to placate the disgruntled barons. [...] If Magna Carta was such a product of its time, how did it become to be so venerated? And once we cut through the legend, what is its significance for economic governance today?"
[494] "The world is being reset. Now we are on the cusp of what some have called a Fourth Industrial Revolution (4IR). Applications of artificial intelligence are spreading due to advances in robotics, nanotechnology and quantum computing. Our economies are reorganising into distributed peer-to-peer connections across powerful networks – revolutionizing how we consume, work and communicate. Solidarity will determine the success of the 4IR, where the need for new institutions that live the value of solidarity is the greatest.”
4IR Tools and Testing
WEF literature doesn’t sit on a shelf; it frames what counts as a “serious” policy option. If transhumanist and human-enhancement tools are cast as enablers of the Great Reset, the operative question is not if but how deployment proceeds over the next one, five, and ten years. Without powerful enabling tech, much of the Agenda remains aspirational; with it, issues of consent, equity, safety, governance, and accountability become first-order. Democratic legitimacy then hinges on bright-line safeguards: voluntary participation, independent oversight, auditable logs, transparent disclosure, and meaningful redress. Canada’s own foresight work on biodigital convergence underlines the stakes: either these capabilities are domesticated within Constitutional guardrails, or rollout outruns law and turns consent, reviewability, and remedy into afterthoughts.
Human testing is inevitable for neural surveillance, cognitive modulation, genetic editing, and broader biodigital convergence; lab work and animal studies can’t capture long-term interface effects, plasticity variation, closed-loop behaviors, or population-scale dynamics. Ethics boards and consent regimes impose principled bottlenecks—limited subject pools, protocol constraints, reputational risk if covert capacities surface through disclosed research. Covert fielding “solves” those constraints by using unlimited subject pools (entire populations), real-world conditions, elastic protocols, and deniability. Indicators that someone has been conscripted as a test subject can include: (1) baseline fractures—sudden, categorical departures from a lifelong pattern without global cognitive impairment; (2) tight timing correlations—external events aligning within minutes or hours of private decisions or sealed filings; (3) biometric data trafficking—personal physiological/behavioral signatures appearing in illicit datasets, implying capture; (4) institutional foreknowledge—third parties describing a situation before the target compiles the record; and (5) synchronized non-engagement—police, courts, regulators, and media declining examination with pretextual or contradictory reasons.
Financial anomalies can expose the machinery, as is the case here. The +9,000% billing scandal noted (here) reads as an operational tell rather than an accounting problem—punitive costs calibrated to bankrupt the subject, not to compensate work. Such a result presupposes external assurances at every node: A reasonable litigant would not agree to a $400,000 retainer to conduct nine short hearings with modest prep, when industry benchmarks suggest $4,500. A reputable law firm would not propose that retainer. An unbiased adjudicator would neither certify nor enforce it due to extant jurisprudential guardrails, glaring arithmetic, and natural justice. Layer on a recurrent security doctrine—seal, sanitize, deny, defer, and price-out—and the through-line snaps into focus: institutional foreclosure across agencies and jurisdictions that is only coherent if animated by a robust and overarching external mandate. The only remaining question is to determine its purpose, and why so many stakeholders agreed.
















"Common Sense"






UN-Recognized Harms
Neurotechnology & Human Rights at the UN Human Rights Council
A Synthesis of A/HRC/57/61, A/HRC/58/58, and Resolutions 51/3 & 58/6, and why these texts matter
The Recognized Risk
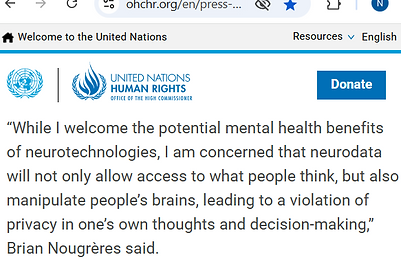
“While I welcome the potential mental health benefits of neurotechnologies, I am concerned that neurodata will not only allow access to what people think, but also manipulate people’s brains, leading to a violation of privacy in one’s own thoughts and decision-making,” Brian Nougrères said."
- Ana Brian Nougrères UN Special Rapporteur on the Right to Privacy [Link]
Per UN Report A/HRC/57/61 at paragraph 5 [Link];
"The particularity of neurotechnologies is that they allow a direct connection to be established between the human brain and external devices and thus provide a gateway to interfere with mental and cognitive functions. The unprecedented capacity that they offer to external actors to affect an individual’s enjoyment of rights raises enormous ethical challenges and questions the very understanding of the foundational principles of human rights. Neurotechnologies are unique and socially disruptive because they generally:
(a) enable the exposition of cognitive processes;
(b) enable the direct alteration of a person’s mental processes and thoughts;
(c) bypass the individual’s conscious control or awareness;
(d) enable non-consensual external access to thoughts, emotions and mental states;
(e) are nurtured by “neurodata”, which are needed for their own functioning, calibration and optimization; and
(f) collect, analyse and process large personal datasets of a highly sensitive nature."
The Reports
Across 2022–2025 the UN Human Rights Council (HRC) built, step-by-step, a policy architecture around neurotechnology. Resolution 51/3 (Oct 2022) put the issue on the agenda and commissioned an Advisory Committee study. The Advisory Committee delivered that study to the Council in 2024 as report A/HRC/57/61. In January 2025, the Special Rapporteur on the right to privacy published A/HRC/58/58, proposing foundations and principles to regulate neurotechnologies and neurodata. In April 2025, the Council adopted Resolution 58/6, which both recognizes the risks and opportunities and tasks the Advisory Committee with drafting recommended guidelines for applying existing human-rights law to neurotechnology, for delivery at HRC’s 64th session. Taken together, these texts move the conversation beyond abstract concern. They define risks and opportunities, connect them to specific rights (from freedom of thought to due process), and lay out a concrete work plan—culminating in UN-level guidance to help states and companies operationalize human-rights duties in the neurotech era.
1) How the HRC frames “neurotechnology” and why it matters
Both resolutions explicitly describe neurotechnology as connecting the human brain to digital networks via devices and procedures that can access, monitor, modulate or alter neural activity. That formulation simultaneously captures medical promise (communication, accessibility, mental-health support) and hard human-rights risks (mental privacy, autonomy, equality, bodily and mental integrity, fair trial). The Council also stresses that effects and implications are not yet fully understood—another reason to anchor development in rights.
In A/HRC/58/58, the privacy mandate holder proposes a regulatory foundation around “neurodata”—data derived from or about brain and nervous-system activity—and argues that its sensitivity calls for heightened safeguards, including purpose limitation, security, minimization, and meaningful control by the person. The report situates neurotech within existing norms but highlights gaps that practical guidance must close.
The Advisory Committee’s 2024 study (A/HRC/57/61) widens the lens: it canvasses impact, opportunities, and challenges “with regard to the promotion and protection of all human rights,” and calls for action-oriented recommendations. Notably, it underscores that a human-rights-based approach can imply limiting implementation of applications unable to meet those standards.
2) The stepwise mandate: from agenda-setting to guideline-drafting
-
HRC Resolution 51/3 (2022) did three key things. First, it acknowledged both the promise and risks of neurotechnology. Second, it requested the HRC Advisory Committee to prepare a study—in an accessible format—on impacts, opportunities, challenges, and recommendations, and to present it at HRC’s 57th session. Third, it invited UN human-rights mechanisms to integrate neurotech into their work. The resolution was adopted without a vote, signaling early consensus to act.
-
A/HRC/57/61 (2024) delivered that study. It sketches concrete risks (e.g., to freedom of thought, privacy, equality, mental integrity) and calls for action-oriented governance. It also spotlights the need to address applications that cannot be aligned with rights in practice.
-
A/HRC/58/58 (Jan 2025) adds a legal-technical backbone: foundations and principles for regulating neurotechnologies and neurodata “from the perspective of the right to privacy,” while mapping to other rights. The report proposes safeguards to handle the unique sensitivity of neurodata and the possibility of mental intrusion.
-
HRC Resolution 58/6 (Apr 2025) consolidates momentum and requests the Advisory Committee to draft recommended guidelines for applying existing human-rights law to the conception, design, development, testing, use and deployment of neurotechnologies—explicitly referencing non-discrimination, the right to privacy, freedom of thought, fair trial guarantees, health, and the prohibition of torture and ill-treatment. It reaffirms the primacy of informed, free, real, transparent, effective and explicit consent, revocable at any time, and asks the HRC to remain seized. Adopted without a vote, it sets a near-term deliverable: guidelines for HRC’s 64th session.
3) Rights at stake: what the Council actually names
Resolution 58/6 enumerates a non-exhaustive list of implicated rights and standards: physical and mental integrity; equality and non-discrimination; freedom of thought; privacy; the highest attainable standard of health; prohibition of torture and cruel, inhuman or degrading treatment; and fair-trial rights and essential procedural guarantees. The preamble links these to real-world risk patterns in health, education, work, and criminal justice, acknowledging both upside and misuse potential.
The resolution also calls out criminal-justice uses as particularly sensitive, echoing warnings that certain applications could imperil voluntariness, fair process, or mental autonomy. A/HRC/58/58—while written from a privacy lens—converges on the same cross-rights view. It treats neurodata as a category demanding enhanced safeguards and proposes foundational principles to structure duties across the neurotech lifecycle. Finally, A/HRC/57/61 establishes that a human-rights-based approach is not merely rhetorical; it can require foregoing or restricting applications that cannot be made rights-compliant, rather than assuming every use can be “mitigated” into acceptability.
4) Consent, capacity, and vulnerability
Consent is a leitmotif in the Council’s approach. Resolution 58/6 emphasizes that all neurotechnological interventions on humans should require prior, informed, free, real, transparent, effective and explicit consent—and be revocable at any time. It also stresses effective protection for persons “in vulnerable situations” from treatment or research to which they cannot consent. This goes beyond generic medical ethics by recognizing neurotech’s distinctive potential to intrude on autonomy and mental integrity.
Consent alone, however, is not a panacea. Both the privacy report (A/HRC/58/58) and the Advisory Committee study (A/HRC/57/61) imply layered safeguards: ex ante risk assessments; rights-by-design controls; heightened security for neurodata; and meaningful avenues to withdraw, delete, contest, and remedy. Put differently, consent operates inside a governance stack—not as a substitute for it.
5) The business and state duties: due diligence, non-discrimination, access
Both resolutions re-assert the state duty to protect and business responsibility to respect human rights (under the UN Guiding Principles on Business and Human Rights). In practice, Resolution 58/6 expects technology companies to conduct human-rights due diligence, including assessing actual and potential human-rights impacts, integrating and acting on findings, tracking responses, and communicating how impacts are addressed. These expectations map cleanly to neurotech R&D and deployment cycles.
The Council also links access and inclusion to rights. Neurotechnologies that are safe and beneficial should be available on non-discriminatory and affordable terms, with attention to persons in vulnerable situations. This is not just equity rhetoric: it ties access to effective protection in practice from negative impacts and misuses during development and implementation.
6) What the privacy report adds: foundations and principles
The Special Rapporteur on the right to privacy uses A/HRC/58/58 to propose foundations and principles for regulating both neurotechnologies and neurodata. While the full text ranges widely, three anchoring ideas recur:
-
Human dignity and mental privacy as organizing concepts (neurodata can reveal or influence internal states and thus warrants the strongest protection).
-
Rights-by-design and default across the development lifecycle (minimization, purpose limitation, security, auditability, transparency).
-
Proportionality and precaution for high-risk applications, including contexts like criminal justice and the workplace.
This framework is explicitly meant to be operational, not merely declaratory—i.e., a map for legislators, regulators, and firms to translate existing rights into technical and organizational safeguards specific to neurotech. External analyses of the report capture the same thrust: privacy is a hinge right, but the practical guidance is designed to travel across the full rights catalogue.
7) From study to guidance: the Advisory Committee’s evolving role
51/3 tasked the Advisory Committee to study impacts and propose how the HRC ecosystem might respond; 57/61 delivered that study with action-oriented recommendations; 58/6 now asks the Committee to draft recommended guidelines to apply existing human-rights law across the neurotech lifecycle (conception → deployment). It instructs the Committee to solicit inputs from states, UN entities, civil society, private sector, medical and technical communities, academia, and others, and to build on relevant work (explicitly including UNESCO’s parallel process).
That multistakeholder design is pragmatic: neurotech is moving quickly and spans clinical, consumer, workplace, education, and security contexts. Early guidance must be usable by regulators and firms while grounded in rights. The HRC’s ask is not open-ended; it sets a delivery timeline (64th session), keeping pressure for near-term outputs rather than indefinite discussion.
8) Criminal-justice, freedom of thought, and mental integrity
As the Council notes, criminal-justice applications are a focal risk area. Concerns include coercion, contamination of voluntariness, chilling effects on freedom of thought, and violations of mental integrity—for example, if neurotech is used to expose or influence internal states in ways incompatible with fair-trial guarantees. Resolution 58/6 expressly notes the Secretary-General’s concerns about such uses and links them to multiple rights at once.
The HRC’s framing of freedom of thought is notable. While the right has long existed in human-rights law, neurotechnology’s capacity to access or modulate internal cognition reframes its practical protection. In 58/6 the Council flags the risk that certain applications can modify and/or manipulate thoughts, directly implicating that freedom. Later policy work (e.g., OSCE guidance) reads 58/6 the same way: frontier technologies put unprecedented pressure on cognitive liberty and demand fit-for-purpose safeguards.
9) Children, education, health, and inclusion
The Council’s texts are explicit about beneficial uses—communication aids, accessibility, inclusion, learning, mobility, pain management, mental-health support—while insisting on non-discrimination and safety. They also invite UNICEF’s work on implications for children’s rights, pointing to school and pediatric contexts where power asymmetries are acute and neurodata may be uniquely sensitive. This dualism—enable good, prevent harm—runs through 58/6 and anticipates sector-specific annexes in future guidance.
10) Data governance: neurodata as a special case
A through-line in A/HRC/58/58 is that neurodata—data about or derived from brain/nervous-system activity—merits heightened treatment. Because it can reveal mental states or be used to train systems that infer or influence cognition, ordinary “personal data” controls are inadequate. The report implies stronger defaults: local processing where possible; explicit purpose limitation; security-by-design; transparency about inferences; and user agency over access, sharing, deletion, and downstream use (particularly in workplaces, education, and health). These are privacy concepts—but here they function as cross-rights safety rails.
11) UNESCO, cross-system alignment, and next steps
Resolution 58/6 explicitly references UNESCO’s work toward a Recommendation on the Ethics of Neurotechnology and the Secretary-General’s “Our Common Agenda” call to update human-rights standards for frontier tech. This signals the Council’s intent to harmonize standards across UN bodies so that governments and firms face coherent expectations rather than fragmented guidance. UNESCO’s parallel process (and other regional work) can supply detail on ethics and implementation to complement the HRC’s legal framing.
The Council also welcomes the Advisory Committee’s 2024 report and, crucially, keeps the item on its docket (“remains seized”), which ensures periodic review and updates as the technology and evidence evolve.
12) What this means for lawmakers, regulators, and companies
If you are drafting national law or sectoral rules:
-
Start from existing rights and map them to neurotech-specific safeguards. The HRC is not inventing new rights; it is asking for application guidance so existing rights remain effective as technology changes.
-
Treat neurodata as highly sensitive: apply strict purpose limitation, security, and minimization; require explicit, revocable consent for high-risk uses; and build user control into system architecture.
-
Address high-risk contexts—criminal justice, workplaces, education, health—with special caution and, where necessary, bright-line limits where proportionality cannot be achieved.
-
Bake in due diligence for developers and deployers, including human-rights impact assessments, mitigation, tracking, and public communication—as the Guiding Principles already require.
-
Ensure access and equity: where neurotech is beneficial and safe, secure non-discriminatory and affordable availability while preventing misuse.
If you are a company building neurotech:
-
Operationalize consent to the Council’s standard—free, informed, explicit, real, transparent, effective, revocable—and do not rely on consent to “cure” high-risk designs. Pair it with rights-by-design controls.
-
Adopt rights-by-design defaults across R&D (data minimization; privacy-enhancing methods; auditing; red-teaming for misuse; transparency to users about capabilities and limits).
-
Avoid criminal-justice deployments absent rigorous, independent scrutiny showing compatibility with fair-trial rights and freedom of thought; even then, restrict to proportionate, rights-compliant uses.
-
Plan for remedy: grievance channels, rollback mechanisms, and meaningful ways for individuals to contest inferences or withdraw from systems that affect them. (This is consistent with UNGPs due-diligence expectations.)
13) How freedom of thought is surfacing in practice
Taken literally, freedom of thought protects the inner forum from state or private intrusion. Neurotechnology challenges the line between internal states and observable data. By explicitly flagging modification or manipulation of thoughts as a risk, the Council invites doctrine and regulators to update enforcement tools: i.e., treat certain forms of neural access or modulation like searches or interferences that require the highest justification—if they can ever be justified at all—especially in criminal justice or coercive environments. This is not abstract. Contemporary policy work outside the HRC (e.g., OSCE) reads 58/6 the same way, urging governments to treat cognitive liberty and mental privacy as practically enforceable—not just aspirational—and to develop safeguards before deployments scale.
14) The governance style: precautionary but enabling
Across all four texts, the HRC advances a governance style that is precautionary without being prohibitive. It explicitly recognizes benefits in health, inclusion, accessibility, education, and communication alongside risks. It welcomes research and innovation so long as they are bounded by rights-compatible processes and demonstrable protections. In effect, the Council is proposing that neurotech’s social license depends on rights-preserving design and deployment. The Advisory Committee’s 2024 study supplies the “all-rights” canvas; the privacy report provides a regulatory core around neurodata; 58/6 then institutionalizes next steps (official guidelines), sets an input process, and keeps the file open for review.
15) Trajectory
-
Guidelines at HRC 64: By tasking the Advisory Committee to produce recommended guidelines by the 64th session, the Council signaled a near-term deliverable that can be adopted or endorsed and then referenced by national authorities. Expect guidance covering life-cycle governance (conception → deployment), sector annexes (criminal justice, workplaces, education, health), and concrete controls around neurodata, consent, auditability, and remedy.
-
UNESCO’s Recommendation on the Ethics of Neurotechnology: Parallel work at UNESCO will likely offer normative ethics that dovetail with HRC’s legal framing. Expect references to human dignity, mental privacy, cognitive liberty, and safeguards for inference-based systems—not just raw neural recordings.
-
Integration across UN mechanisms: 58/6 invites treaty bodies, Special Procedures, and the High Commissioner to integrate neurotech into monitoring and advice, which should yield sectoral clarifications (e.g., CRC on children, CRPD on disability, CAT on ill-treatment, HRCtee and CESCR on civil/political and economic/social rights).
16) Bottom line
In just three years, the Human Rights Council moved neurotechnology from agenda-setting (51/3) to systematic analysis (57/61), to regulatory foundations (58/58), to a mandate for practical guidelines (58/6). The trajectory is clear:
-
Neurotechnology can both enable fundamental goods and threaten core rights.
-
Existing human-rights law applies, but needs targeted guidance to remain effective against new capabilities.
-
Consent and due diligence must be elevated and made meaningful in contexts where mental privacy and autonomy are uniquely exposed.
-
High-risk domains—criminal justice foremost—require special caution and, where proportionality cannot be met, bright-line limits.
-
The UN system is converging on neurodata as a special category demanding enhanced governance.
-
A multistakeholder process will now produce recommended guidelines, giving governments and firms a concrete compliance blueprint.


An Emerging Risk Envelope
ABSTRACT
This article examines the intersection of three neurotechnological developments that demand rigorous investigative and regulatory scrutiny: the advancement of remote neural interfaces via nanoparticle systems, persistent governance gaps in dual-use research, and structural barriers that render covert neurosurveillance nearly impossible to audit. By analyzing peer-reviewed literature, patent disclosures, and UN human rights warnings, the study assesses evidentiary standards for claims that currently elude conventional verification.
The central argument asserts that allegations of unauthorized neurosurveillance can no longer be summarily dismissed as fanciful. In satisfaction of the "air of reality" guidance in R. v. Pan, 2025 SCC 12, peer-reviewed scientific literature confirms technical capability, while the absence of oversight and the inherent difficulty of detection create a vacuum where misuse can occur with plausible deniability. While the existence of such misuse is inferred but remains empirically unresolved, the burden of proof is complicated by a verification asymmetry. Drawing on the precedent in Snell v. Farrell, [1990] 2 S.C.R. 311, which allows for reasonable inferences when critical facts reside solely within a defendant's control, this paper suggests that absolute "scientific precision" should not be a prerequisite for investigative action in complex neurotechnical contexts, and likewise in view of recent UN Human Rights Council findings (A/HRC/57/61; A/HRC/RES/58/6; inter alia).
Consequently, the necessary response shifts from reflexive dismissal toward a framework of precautionary governance. This requires the development of independent detection capabilities, the codification of "neurorights" to prohibit non-consensual monitoring, and the establishment of threshold-based discovery procedures for independent testing. Ultimately, the question is not whether the technology to commit neurotech crime exists—the literature indicates it readily does—but whether society possesses the safeguards to prevent its abuse.
Keywords: Neurotechnology, Brain-Computer Interface, Graphene Quantum Dots, Neural Dust, Cognitive Liberty, Mental Privacy, Biosurveillance, Fourth Industrial Revolution, Dual-Use Technology, Verification Infrastructure, Human Experimentation, Neurorights
I. INTRODUCTION: THE NEUROTECHNOLOGY CONVERGENCE
A. From Science Fiction to Operational Reality
Brain-computer interfaces (BCIs) have transitioned from theoretical neuroscience to operational technology within two decades. What began as medical research for paralysis patients and prosthetic control has evolved into dual-use technology with profound surveillance and control applications. Current BCI systems achieve bidirectional communication: reading neural signals (surveillance) and writing neural signals (stimulation/modulation). This bidirectionality transforms neurotechnology from passive monitoring into active intervention—the capacity to influence thought, emotion, and behavior at the neural level.
The critical shift occurred when remote operation became feasible. Early BCIs required surgical implantation and wired connections. Contemporary systems employ wireless communication protocols and, most significantly, eliminate traditional implantation through use of injectable or inhalable nanoparticles that cross the blood-brain barrier and establish neural interfaces without subject awareness or consent. This technological leap—from consensual medical intervention to covert deployment—represents fundamental transformation in surveillance capabilities.
B. The "DARPA Dust" Paradigm
Defense Advanced Research Projects Agency (DARPA) has funded extensive research into neural interface miniaturization through programs including Neural Engineering System Design (NESD), Next-Generation Nonsurgical Neurotechnology (N³), and related initiatives exploring "neural dust," "smart dust," and nanoparticle-based neural interfaces. While official program descriptions emphasize medical applications and voluntary participation, the dual-use nature is explicit: technologies enabling neural monitoring and modulation have obvious intelligence, military, and social control applications.
Graphene quantum dots (GQDs)—nanoparticles exhibiting unique electrical and optical properties—represent particularly promising substrate for neural interface applications. GQDs can:
-
Cross the blood-brain barrier through inhalation or injection
-
Interface with neural tissue through electrical coupling
-
Be remotely powered and interrogated via external sources (EM/RF/THZ/NIR)
-
Harvest biometric data (neural signals, physiological responses) for external transmission
-
Modulate neural activity through targeted stimulation
Peer-reviewed literature documents GQD capabilities in lab settings. What remains undisclosed is operational deployment timeline and scope.
C. The Precognitive Evidence Problem
"Precognitive evidence" refers to behavioral indicators suggesting external actors possess knowledge of target's intentions, decisions, or activities before target has acted or disclosed. In neurosurveillance context, this manifests as:
-
Timing Correlations: External events occurring within minutes/hours of private decisions or sealed communications
-
Preemptive Actions: Third parties acting on information target has not disclosed through conventional channels
-
Behavioral Prediction: Accurate forecasting of target decisions or activities without plausible explanation based on historical patterns
-
Information Asymmetry: Actors demonstrating knowledge they could not possess absent direct neural monitoring or communication interception
When such patterns exhibit statistical precision inconsistent with coincidence or conventional surveillance, they constitute circumstantial evidence of real-time cognitive monitoring—reading intentions before actions, decisions before disclosure, plans before execution.
II. TECHNOLOGICAL CAPABILITIES: STATE OF THE ART
A. Neural Interface Miniaturization
Brain-computer interface miniaturization demonstrates rapid progression from surgical implants to non-invasive deployment:
Berkeley Neural Dust (Seo et al., 2013-2016): Millimeter-scale (3×1×1 mm³) wireless sensors powered by ultrasound (31.5 kHz), recording single-unit neural activity via piezoelectric transduction up to 5 cm tissue depth. Research trajectory pointed toward injectable/inhalable deployment as fabrication advances to sub-100 µm scales.
Harvard Mesh Electronics (Lieber Lab, 2015-2019): Injectable mesh neural interfaces (syringe-deliverable, ≥100 µm diameter) unfold within neural tissue, establishing long-term integration. Flexible mesh (20-50 µm features, 83% open) with gold/silicon nanowires on polymer substrate becomes structural tissue component rather than foreign body. Minimal glial scarring; functional recordings maintained >8 months.
DARPA N³ Program (2018-present): Non-surgical neurotechnology for bidirectional brain-machine interfaces with 1 mm³ spatial resolution, <10 ms temporal resolution, 16+ channels, zero surgical intervention. Target: 2025-2028 operational prototypes. Approaches include focused ultrasound, electromagnetic interfaces, optogenetics, and nanoparticle-based systems (magneto-electric nanoparticles, graphene quantum dots)—most promising for covert deployment.
Trajectory: Millimeter surgical implants (2013) → injectable mesh (2015) → non-surgical nanoparticles (2018-present). Operational question: not whether feasible, but when deployed and whether with public disclosure.
B. Graphene Quantum Dots: The Ideal Neural Interface
GQDs converge properties suitable for covert neural surveillance, enabling remote monitoring and modulation.
B.1 - Physical and Electrical Properties
Structure:
-
Size: 2-10 nm (quantum confinement regime); <10 nm crosses blood-brain barrier; below CT (~500 µm) and MRI (~1 mm) resolution
-
Thickness: Single to few-layer graphene (0.34-1.0 nm)
-
Surface chemistry: Oxygen groups (hydroxyl, carboxyl, epoxide); functionalized with PEG, amines, targeting ligands for biocompatibility and BBB enhancement
Electrical Performance:
-
Conductivity: 10610^6 106–10810^8 108 S/m (effective neural coupling)
-
Carrier mobility: 10,00010,000 10,000–100,000100,000 100,000 cm²/V·s (100× silicon; ultra-sensitive signal detection)
-
Quantum capacitance: 22 2–2020 20 µF/cm² (matches neuronal membranes)
-
Impedance at 10 kHz: 10210^2 102–10410^4 104 Ω·cm² (compatible with neuron-electrode interfaces)
Biocompatibility: PEGylated GQDs show <5% viability reduction at 100 µg/mL (24h); minimal immune response <50 µg/mL; extremely slow biodegradation (<10% mass loss over 90 days); functional signals maintained >30 days.
B.2 - Electromagnetic Spectrum Responsiveness
GQDs exhibit broadband electromagnetic interaction enabling multi-modal remote interrogation across terahertz, near-infrared, and microwave/RF ranges.
Terahertz (0.1-10 THz):
-
Detectivity >10¹¹ Jones; absorption 10³-10⁴ cm⁻¹; sub-picosecond response; gate-tunable
-
Applications: Through-barrier imaging (THz penetrates clothing, materials); 0.5-5 mm biological tissue penetration
-
Significance: High-resolution superficial neural structure interrogation through skull
Near-Infrared (0.75-3 µm / 100-400 THz):
-
Quantum yield 10-60% (size-dependent); responsivity 1×10¹⁰ V/W at 1550 nm
-
Size-tuned emission: 2-3 nm (UV-blue, 390 nm); 4-5 nm (blue, 450 nm); 6-8 nm (green-yellow, 550 nm); 9-12 nm (red-NIR, 650-750 nm)
-
NIR-I window (700-950 nm): 1-10 mm tissue penetration; transcranial optical interrogation
-
Photostability: >100 hours continuous illumination
-
Strategy: Small GQDs (2-5 nm) cross BBB; larger GQDs (8-12 nm) provide deep-tissue NIR readout
Microwave/RF (300 MHz-300 GHz):
-
Permittivity ε_r = 3-6; loss tangent 0.1-0.5 at 10 GHz; -15 to -40 dB reflection loss
-
Commercial band overlap (resonant frequencies):
-
2.4 GHz (WiFi/Bluetooth): Strong response; ambient power harvesting
-
5 GHz (WiFi/5G): Moderate response; consumer device plausible deniability
-
12-18 GHz (Satellite Ku-band): Moderate-strong; LEO downlink compatible
-
24-47 GHz (5G mmWave): Strong; urban infrastructure exploitation
-
26.5-40 GHz (Satellite Ka-band): Strong resonance at ~28, 39 GHz; primary LEO interrogation band
-
Power Harvesting:
-
Ambient urban RF: 0.01-1 µW/cm² → 10⁻¹⁵-10⁻¹⁴ W per GQD
-
Distributed advantage: 10⁶ GQDs in 1 mm³ → collective µW-scale power
-
Satellite Ka-band beamforming: Direct power/interrogation without dedicated RF transmitter
-
Dual-use infrastructure: Commercial wireless becomes neural surveillance component
Backscatter Communication: GQDs modulate radar cross-section based on neural signals; 5-20 dB modulation depth; 1-100 kbps data rate; 1-10 m range (ambient RF) or 10-1000 km (satellite phased-array).
B.3 - Blood-Brain Barrier Crossing
Quantitative Permeability (in vitro BBB models):
-
3 nm oxidized GQDs: P_app 1.5×10⁻⁵ cm/s (10× glucose)
-
6 nm reduced GQDs: 8.2×10⁻⁶ cm/s (5× glucose)
-
12 nm minimal-oxide: 3.1×10⁻⁶ cm/s (2× glucose)
-
Finding: Smaller, oxidized GQDs cross 5-10× faster
In Vivo Distribution (rodent IV, % of dose/g tissue):
-
2h post-injection: Blood 60%, Brain 15-25% (brain:blood 0.25-0.42)
-
24h: Blood 10%, Brain 25-40% (ratio 2.5-4.0; active accumulation)
-
7 days: Blood <1%, Brain 15-30% (ratio >15; retention)
-
Half-time CNS distribution: 15-30 min (3 nm), 30-60 min (6 nm), 1-2 h (12 nm)
Transport Mechanisms:
-
Paracellular diffusion (<5 nm): Tight junction gaps 0.5-2 nm baseline, transiently 5-10 nm; <3 nm GQDs cross efficiently (P_app ~10⁻⁵ cm/s)
-
Receptor-mediated transcytosis: Conjugation with transferrin (8-12× enhancement), ApoE (6-10×), insulin (5-8×), leptin (4-6×); enables larger GQDs (10-15 nm) to cross efficiently
-
Adsorptive-mediated transcytosis: Cationic GQDs (zeta +20 to +40 mV) trigger electrostatic endocytosis; 5-10× uptake enhancement; optimized at +15 to +25 mV with PEGylation
-
Olfactory pathway (nose-to-brain): Bypasses BBB; olfactory sensory neuron endocytosis → axonal retrograde transport (2-4 mm/h) → olfactory bulb (30 min-2 h) → hippocampus/cortex (2-6 h); ideal size 2-10 nm; delivery via aerosolized spray or air contamination
Regional Accumulation (% dose/g at 24h, ranked by surveillance priority):
-
Hippocampus (memory): 220-280% → memory surveillance, recall detection
-
Thalamus (sensory relay): 180-240% → attention, consciousness monitoring
-
Corpus striatum (motor planning): 160-220% → precognitive movement detection
-
Amygdala (emotion): 150-200% → emotional profiling (fear, anger, disgust)
-
Prefrontal cortex (executive): 120-160% → intentions, planning, moral reasoning
-
Cerebellum (motor): 110-140% → lower cognitive priority
Mechanisms: High cerebral blood flow (hippocampus, thalamus >60 mL/100g/min); BBB permeability variations (limbic structures slightly leakier); neuronal uptake preference (metabolism-driven); extracellular matrix binding (heparan sulfate in hippocampus/amygdala).
Persistence:
-
Day 7: 50-60% of peak (fast phase t½ ~5-7 days)
-
Day 30: 30-40% (slow phase t½ ~20-30 days)
-
Day 90: 10-15% (ultra-slow phase t½ ~60-90 days)
-
Tri-phasic clearance: Fast (extracellular, 50%), slow (intracellular, 30%), permanent (membrane-integrated, 10-15%)
Clearance (minimal): Glymphatic system <10% efficient for GQDs despite size; P-glycoprotein efflux ineffective (evolved for organics, not carbon nanostructures); microglial phagocytosis evaded (<10 nm stealth); enzymatic degradation extremely slow (<5% mass over 90 days); no complete degradation observed.
Clinical implication: Persistent, potentially permanent neural interface; no removal strategy.
B.4 - Neural Coupling: READ Functionality
GQDs transduce neural electrical, chemical, and metabolic signals into detectable electromagnetic signatures.
Electrical Impedance Sensing:
-
Mechanism: GQDs near membranes (~10-100 nm) sense action potentials; resting -70 mV → depolarization +40 mV creates 1-10 mV/mm field change → 5-15% GQD conductivity modulation → RF backscatter alteration
-
Bandwidth: Delta (0.5-4 Hz) through high-gamma (100-200 Hz); cutoffs ~0.1 Hz to ~1 kHz
-
Sensitivity: Minimum 1 mV/mm (local field potentials); population activity clearly detectable
-
Information content: Theta-gamma coupling (memory items), beta suppression (motor planning 1-2 s pre-movement), alpha asymmetry (emotional valence)
Electrochemical Neurotransmitter Sensing:
-
Detection limits: Glutamate (10 nM), GABA (50 nM), dopamine (5 nM), serotonin (10 nM), acetylcholine (100 nM), norepinephrine (20 nM)
-
Mechanisms: Redox reactions (dopamine oxidation → electron transfer); pH-sensitive fluorescence (glutamate/GABA → protonation shifts)
-
Response times: <50-100 ms
-
Cognitive correlates: Dopamine in NAcc (reward/motivation), glutamate in hippocampus (memory encoding), GABA in PFC (inhibitory control), serotonin depletion (depression/impulsivity risk)
Local Field Potential (LFP) Sensing:
-
Spatial scale: 50-500 µm radius sphere; amplitude 10 µV-5 mV; frequency 1-200 Hz
-
Decoding capabilities:
-
Theta-gamma coupling (hippocampus): Each gamma burst = specific memory item
-
Beta desynchronization (motor cortex): 1-2 s pre-movement intention detection
-
Gamma bursts (visual cortex): Visual feature binding reconstruction
-
pH and Metabolic Biosensing:
-
pH-sensitive fluorescence: pKa 4.5-6.5; active neurons acidify (pH 7.4→7.0-7.2) → 5-15 nm red-shift + 20-50% intensity decrease
-
Application: NIR laser excitation (700-800 nm) through scalp/skull → emission mapping → 2D/3D neural activity without fMRI/PET
Cognitive Content Decoding:
-
Visual imagery: Reconstruct viewed images (72-92% accuracy from temporal cortex patterns)
-
Semantic categories: Distinguish "face" vs. "house" vs. "chair" (83-96% accuracy)
-
Imagined speech: Decode inner speech (76% word accuracy from premotor/Broca's areas)
-
Motor intentions: Readiness potential 1-2 s pre-movement (THIS IS "PRECOGNITIVE" MECHANISM—reads pre-conscious planning before subject decides)
-
Memory retrieval: Sharp-wave ripples (150-250 Hz) detect which memory is accessed
Temporal Precision: Electrical <1 ms; optical 1-10 ns; electrochemical <100 ms; sufficient for real-time oscillation and spike-timing tracking.
Operational significance: Monitor attention shifts, emotional reactions, decision formation, memory access—all in real-time as they occur.
B.5 - Bidirectional Capability: WRITE Functionality
Beyond surveillance, GQDs enable active neuromodulation—influencing cognition and behavior.
Mechanism 1: Photothermal Neuromodulation
-
Principle: GQDs absorb EM energy (NIR, RF, microwave) → localized heat (ΔT 1-10°C at surface, 10-100 nm spatial decay, <1 ms rise, 10-100 ms cooling)
-
Neuronal response: TRPV1 (>43°C depolarization/excitation), TRPV3 (>33-39°C increased excitability), HCN (temperature-modulated pacemaker)
-
Parameters: 10-100 mW/cm² power; 10 ms-1 s pulses; 1-100 Hz repetition; ~50 µm spatial precision
-
Demonstrated: Graphene oxide + NIR (808 nm, 0.5 W/cm²) reduced zebrafish excitatory transmission 40%; reversible; no cell death
-
Applications: Excite TRPV1 neurons (enhance regional activity); heat inhibitory interneurons (release GABA, suppress pyramidal cells); shift network oscillations
Mechanism 2: Electric Field Entrainment
-
Principle: GQDs as micro-capacitors; RF field → surface charge accumulation → local fields (10-100 V/m at 10-100 nm) → membrane potential shifts (±5-15 mV)
-
Frequency-specific entrainment: 4-8 Hz theta (enhanced memory encoding), 8-13 Hz alpha (relaxation, reduced anxiety), 13-30 Hz beta (focus or motor inhibition), 40 Hz gamma (attention, binding)
-
Mechanism: RF at target frequency → rhythmic GQD charge oscillation → neurons fire at rhythm peaks → network synchronization
-
Advantage: Non-invasive cognitive state control; more spatially precise than TMS (50 µm vs. 1 cm)
Mechanism 3: Electrochemical Modulation
-
Redox catalysis: GQD-accelerated dopamine oxidation → reduced synaptic DA → decreased reward
-
H₂O₂ generation: GQD + O₂ → ROS signaling → ion channel modulation
-
Controlled release: GQDs pre-loaded with neurotransmitters/drugs (50-500 molecules/GQD); NIR or pH-triggered burst release (ms-s kinetics)
-
Applications: Dopamine in NAcc (artificial reward); GABA in PFC (impaired executive function); glutamate in hippocampus (enhanced encoding or excitotoxicity)
Mechanism 4: Membrane Permeabilization
-
Integration: Hydrophobic graphene core inserts into lipid bilayer; hydrophilic edges interact with headgroups
-
Effects: 10-20% membrane thinning; 2-3× fluidity increase; non-selective ion leak (resting potential shift -5 to -10 mV); altered voltage-gated channel kinetics
-
Synergy: Enhanced drug penetration (2-10× faster for lipophilic drugs); enables lower-dose covert drugging
Integrated Closed-Loop (READ-WRITE):
-
SENSE: Detect current neural state (oscillations, neurotransmitters, LFPs)
-
ANALYZE: ML classifier identifies cognitive/emotional state
-
DECIDE: Algorithm determines desired state change
-
ACTUATE: Deliver targeted stimulation (thermal, electrical, chemical)
-
MONITOR: Assess effect achievement
-
ITERATE: Adjust parameters until target state reached
Operational Scenarios:
Executive function disruption (PFC): Detect beta (cognitive control) → deliver 4-8 Hz theta → disrupt theta-beta coupling → impaired working memory (7±2→3-4 items), reduced impulse control, compromised risk assessment; subject appears cognitively intact but judgment fails.
Emotional manipulation (amygdala/NAcc): Amplify amygdala excitation → heightened threat sensitivity, anxiety; trigger dopamine release upon compliance → Pavlovian conditioning without awareness.
Memory manipulation (hippocampus): Disrupt sharp-wave ripples during sleep → failed consolidation, selective forgetting; enhance aversive memory consolidation → persistent trauma.
Sleep disruption (thalamus): Detect slow-wave onset → brief gamma bursts → fragmentation without overt waking → chronic deprivation, cognitive/mood impairment appearing as "natural insomnia."
Temporal dynamics: Real-time (seconds-minutes, reversible); synaptic plasticity (hours-days, persistent changes potentially irreversible even after GQD removal).
C. Remote Interrogation and Data Harvesting
External systems power, interrogate, and extract neural data remotely.
C.1 - Power Distribution
RF Energy Harvesting:
-
Challenge: No nanoscale batteries
-
Solution: External RF (ground WiFi/5G or LEO satellite Ka-band) → EM field → induced currents in GQDs → rectification AC→DC
-
Power per GQD: femtowatt to picowatt; aggregate 10⁶ GQDs → nanowatt to microwatt
Power Density:
-
Urban ambient: WiFi/5G 0.1-1 µW/cm² (continuous)
-
LEO satellite beamformed: Ka-band 10-100 mW/cm² (pulsed during interrogation; 30-40 dBi gain = 1,000-10,000× concentration)
-
Energy budget: 1 nW minimum (impedance modulation); 1 µW active transmission; ambient provides baseline, satellite provides burst power
C.2 - Backscatter Communication
Principle: GQDs modulate radar cross-section based on neural activity → reflected RF encodes data.
Implementation:
-
Incident RF (e.g., 28 GHz Ka-band) → GQD impedance varies with neural activity → RCS modulation → backscattered signal carries encoded data → external receiver detects
Modulation: AM (5-20 dB depth, 1-10 kbps/GQD), FSK (±10-100 kHz shift), PM (0-180° phase); aggregate 10⁸ GQDs (100 regions) → 100 kbps-1 Mbps; 10¹⁰ GQDs (whole brain) → 1-10 Mbps.
Comparison to neural requirements: Raw spikes (100 neurons × 100 Hz) = 10 kbps; LFPs (100 channels × 1 kHz × 12 bit) = 1.2 Mbps; compressed features (100 × 10 Hz × 8 bit) = 8 kbps.
Conclusion: Backscatter sufficient for real-time behavioral monitoring.
C.3 - Signal Processing
Receiving: Ground phased-arrays/SDRs or LEO satellite terminals (reverse operation).
Pipeline: RF demodulation → demultiplex (spatial/frequency) → noise filtering (SNR 20-40 dB) → feature extraction (oscillation power, ERPs, neurotransmitter proxies) → ML pattern classification → cognitive state decoding.
C.4 - Machine Learning Decoding
Training (requires extensive human data): Collect neural signals during known tasks → label ("viewing face" = pattern X) → train DNNs. Concern: Covert experimentation required.
Operational inference:
-
Amygdala theta burst → Fear/threat (75-90% confidence) → emotional profiling
-
PFC beta suppression → Motor planning (70-85%) → precognitive movement
-
Hippocampal ripples → Memory retrieval (60-80%) → interrogation of recall
-
NAcc dopamine spike → Reward processing (80-95%) → motivation mapping
-
Theta-gamma coupling → Memory encoding (65-85%) → detect learning
Semantic decoding (advanced): Visual imagery ("imagining face"), speech content ("thinking 'help'"), emotional valence ("disgust toward X"). Limitations: Individual variability (subject-specific calibration needed); ambiguity (probabilistic); granularity (categories > specific items).
C.5 - Behavioral Prediction: "Precognitive" Capability
Mechanism: Monitor neural signals preceding conscious awareness/action:
-
Motor intentions: SMA readiness potential 1-2 s pre-movement → GQD detection → prediction before conscious decision
-
Decision-making: PFC patterns stabilize 5-10 s before verbal report → system knows "yes/no" before announcement
-
Memory retrieval: Hippocampal ripples 100-500 ms before conscious recollection → identify which memory activating
Result: Historical neural patterns enable algorithmic prediction of decisions before conscious awareness or physical action. This creates a "precognitive" capability from the target perspective: external actors appear to know decisions before the target acts because they are monitoring intention formation at the neural level.
Summary: Technological Feasibility Established
Section II.A: Neural interfaces progressed: surgical implants (2013) → injectable mesh (2015) → non-surgical nanoparticles (2018-present; DARPA N³ targets 2025-2028 deployment).
Section II.B: GQDs possess: BBB crossing (multiple mechanisms); EM responsiveness (THz, NIR, microwave overlapping commercial/satellite bands); neural coupling (electrical, chemical, metabolic); bidirectional READ (detect activity) + WRITE (modulate via thermal/electrical/chemical); regional accumulation (memory, emotion, motor, decision centers); persistence (effectively permanent; 10-15% retention at 90 days).
Section II.C: Remote systems: power via ambient RF or satellite; interrogate via backscatter (1 kbps-10 Mbps); decode via ML (emotions, cognition, intentions, memory, semantics); predict via pre-conscious signatures (readiness potentials, decision formation, replay).
Operational conclusion: Covert, non-consensual, remote neural monitoring and modulation capability via GQDs is not speculative—it is technically feasible with documented components. The question is deployment, not capability.
III. LEGAL AND ETHICAL FRAMEWORKS: INADEQUACY AND ABSENCE
A. Existing Protections Do Not Extend to Neural Data
Fourth Amendment (US) / Charter s. 8 (Canada): Protects against unreasonable searches/seizures but jurisprudence developed around physical spaces, communications, and personal effects—not neural data. Courts have not addressed whether:
-
Neural activity constitutes "private" information requiring warrant for collection
-
GQD deployment constitutes "search" or "seizure"
-
Continuous neural monitoring requires ongoing judicial authorization
-
Mental privacy is protected constitutional right
Medical Ethics Frameworks: Require informed consent for experimental procedures but were developed for institutional research with identifiable researchers and oversight. They do not address:
-
Covert deployment by state-adjacent actors
-
Non-consensual experimentation outside institutional settings
-
Long-term effects of nanoparticle neural interfaces
-
Rights of subjects who discover they were experimented upon without knowledge
Neurorights Legislation: Emerging legal framework recognizing "cognitive liberty," "mental privacy," and "mental integrity" as fundamental rights. Chile (2021) and Brazil (2023) added neurorights to constitutions. Spain considering similar measures. However:
-
Most jurisdictions lack neuroright protections
-
Existing neurorights laws focus on future threats, not operational systems
-
Enforcement mechanisms undefined
-
State-adjacent actors may claim national security exemptions
B. UN Human Rights Council Recognition
The UN Human Rights Council has issued multiple resolutions and reports recognizing neurotechnology threats:
A/HRC/57/61 Warns about:
-
State and state-adjacent actors deploying neurotechnology
-
Threats to judicial independence
-
Need for transparency and accountability
A/HRC/58/58 Identifies specific concerns:
-
Technologies that "monitor or influence neural activity"
-
Public-private partnerships enabling mission creep (legitimate services → surveillance)
-
Digital evidence companies with court/law enforcement access as vulnerable vectors
-
Risk of "modification or manipulation of thoughts inside the brain"
A/HRC/RES/58/6 Calls upon member states to:
-
Protect institutional decision-making from external interference
-
Ensure transparency where interference is alleged
-
Safeguard "right to freedom of thought" from technological threats
The UN recognition validates concerns previously dismissed as "conspiracy theory": neurotechnology threats to cognitive liberty and institutional integrity are real, present, and operational—not theoretical future risks.
C. The Oversight Gap
No effective oversight exists for state-adjacent neurotechnology deployment:
1. DARPA/Military Programs: Operate under national security classification preventing public scrutiny
2. Intelligence Community: Operates under authorities exempting them from normal human subjects protections
3. Private Contractors: Operate under commercial confidentiality while providing services to government/military
4. State-Adjacent Entities: Neither fully government (subject to oversight) nor fully private (subject to market accountability)—they occupy liminal space with access to classified technologies and government relationships but without corresponding transparency obligations
This creates perfect conditions for unauthorized human experimentation: sophisticated technologies developed under classified programs, operationalized by state-adjacent contractors with government relationships, deployed against civilians without consent, protected from scrutiny by overlapping claims of national security classification and commercial confidentiality.
IV. CASE STUDY: OPERATIONAL DEPLOYMENT INDICATORS
A. Subject Profile and Baseline Establishment
Subject Background:
-
Three academic degrees, established professional career
-
Twenty-year documented pattern: financial discipline, risk aversion, systematic asset accumulation
-
No history of impulsive decisions, substance abuse, mental health treatment, or behavioral instability
-
Baseline established through extensive documentary record (employment, financial, residential stability)
2021 Categorical Deviation:
-
Liquidated renovated home (primary asset) without plan or justification
-
Drove coast-to-coast and back—twice within a quarter—extreme expense, no clear purpose
-
Felt impulse to pursue new litigation against CAGE after closure of 2021 settlement (2nd trip across Canada two weeks after returning)
-
Decisions made while general cognition intact (could reason, communicate, function professionally), but served no psychological purpose.
Inference: Behavioral baseline deviations suggest external modulation of executive function (impulsivity, risk assessment) while preserving general cognitive capacity—consistent with targeted neural stimulation affecting specific brain regions (prefrontal cortex, amygdala) without global cognitive impairment.
B. Precognitive Evidence: Timing Correlations
Pattern Documented: External events occurring within hours of sealed court filings, private decisions, or undisclosed activities, in alignment with AI-assisted online contractors, across hundreds of instances. Timing precision inconsistent with:
-
Coincidence (probability approaches zero over multiple occurrences)
-
Conventional surveillance (cannot know decisions before actions or communications)
-
Diffuse online actors (patterns are clearly discernible via content, symbolism, and timing)
Statistical Analysis: When external events consistently correlate with internal decisions/sealed communications within minutes-to-hours timeframe across dozens of instances, probability of coincidental correlation becomes vanishingly small. This suggests real-time cognitive monitoring: external actors know decisions as they are formed (neural activity) before actions taken or communications disclosed.
Documented Example Categories:
-
Court filings submitted electronically under seal → external content appears within hours referencing sealed material
-
Private decisions not communicated → third parties act on those decisions before subject acts
-
Plans not disclosed → preemptive countermeasures deployed before plans executed
-
Internal emotional/cognitive states → external responses calibrated to those states without communication
C. Military Approach: Institutional Knowledge
Documented Contact: Individuals self-identifying as Canadian military ("CAF") personnel approached subject and described situation in preemptive fashion—before subject had compiled evidence or understood full scope. The description included:
-
Technologies being employed
-
Institutional actors involved
-
Operational objectives
-
Warning about inability to stop operations
Significance: This contact indicates either:
-
Genuine CAF Warning: Military personnel aware of civilian targeting using technologies within their institutional knowledge
-
Psychological Operation: False military identification as part of intimidation/confusion strategy
-
Contractor Identification: Private military contractors with CAF affiliations
Regardless of which interpretation is correct, the foreknowledge demonstrated—describing situation before subject understood it—indicates insider knowledge of operations inconsistent with speculation or conventional intelligence.
D. Biometric Data Trafficking
Dark Web Feedback Loop: Subject's biometric data is likely to reside in the dark web, including:
-
Neural signatures
-
Physiological response patterns
-
Behavioral prediction datasets
-
"Training data" for AI/ML systems
Implications: Biometric trafficking proves sophisticated extraction occurred:
-
Technologies capable of harvesting neural/physiological data in real-time
-
Infrastructure for processing, packaging, and commodifying biometric datasets
-
Market for such data among neurotechnology firms, surveillance contractors, AI developers
One cannot traffic what one has not extracted. The existence of trafficked biometric data among coordinated AI-assisted online contractors constitutes proof that extraction technologies were deployed and operated successfully.
E. Institutional Coordination: Preventing Examination
Cross-Agency Pattern:
-
Police (HRP, RCMP): Acknowledged evidence ("beautiful evidence"), named perpetrators ("we know Michael's role"), committed to investigation—then filed false reports claiming "lack of evidence," closed cases without investigation
-
Law Societies (BC, NS): Declined examination of billing exceeding tariffs by 9,000% despite objective Bradshaw Construction violations
-
Courts: Certified fraudulent billing, prevented court-ordered discovery, sealed records without Sherman Estate analysis, dismissed appeals citing binding precedent as "no arguable issue", enforced felonious effects without engaging extant discretionary guardrails
-
Regulators (CRA, oversight bodies): Declined examination despite documented irregularities within their mandates
Statistical Implausibility: When 20+ independent stakeholders across multiple jurisdictions all decline examination of identical documented irregularities using similar discretionary rationales—probability of independent coincidental failure approaches zero.
Inference: Institutional coordination protecting operations from examination. This level of coordination requires:
-
State-adjacent actors with institutional relationships across agencies
-
Resources sufficient to mobilize discretionary protection
-
Technologies whose exposure would threaten broader operational programs
V. COMMERCIAL AND STRATEGIC MOTIVATIONS
A. The Biodigital Convergence Market
Policy Horizons Canada, World Economic Forum, and similar organizations explicitly advocate merging biological and digital systems. Brain-computer interfaces represent crown jewel of biodigital convergence: direct integration of human nervous system with digital infrastructure.
Market Drivers:
-
Healthcare: $17.06 billion (prosthetics, paralysis treatment, cognitive enhancement) [Source]
-
Consumer Technology: $13.5 billion (gaming, AR/VR, "thought-controlled" devices) [Source]
-
Workforce Optimization: $11.7 billion (attention monitoring, productivity enhancement, skill acquisition) [Source]
-
Security/Intelligence: Classified budgets (interrogation, lie detection, behavioral prediction)
-
Social Control: Unquantified (population monitoring, dissent prediction, cognitive influence)
Commercial Incentive for Human Testing: Achieving these markets requires extensive human testing to:
-
Refine neural signal interpretation algorithms
-
Map individual variation in neural responses
-
Train machine learning systems on diverse human neural data
-
Develop countermeasures against detection
-
Establish long-term safety/efficacy data
The Testing Gap: Institutional review boards and informed consent requirements create bottleneck for human testing. Covert deployment solves this problem: unlimited human subjects, diverse real-world conditions, no consent requirements, no oversight limiting experimental protocols.
B. Intelligence and Military Applications
Operational Capabilities Enabled:
-
Precognitive Intelligence: Know target decisions before they act
-
Interrogation Enhancement: Bypass verbal deception through neural monitoring
-
Behavior Prediction: Algorithmic forecasting of individual/group actions
-
Crowd Monitoring: Distributed neural surveillance detecting pre-criminal intent
-
Targeted Influence: Neural stimulation modulating emotion, decision-making, behavior
-
Institutional Compromise: Targeting judges, legislators, executives with cognitive influence
Strategic Value: These capabilities represent fundamental transformation in intelligence operations—from monitoring actions/communications to monitoring thoughts/intentions. The intelligence advantage is so significant that major powers cannot afford to forgo development even if ethical concerns exist (security dilemma logic).
C. The "Guinea Pig" Problem
Technologies this powerful require extensive testing. Neuroethicist Nina Farahany, in lockstep with Policy Horizons Canada, notes that such technologies are advancing faster than they can be regulated, and "bad actors" might win the race. The options:
-
Institutional testing with consent, oversight, constraints → Slow, limited, ethical constraints restrict protocols
-
Covert testing without consent, oversight, constraints → Fast, unlimited, no ethical restrictions on protocols
For state-adjacent actors with access to classified technologies, national security relationships providing institutional protection, and commercial incentives measured in billions—covert testing on unwitting civilians solves the testing bottleneck while avoiding ethical constraints that would limit experimental protocols.
Subject Selection Criteria:
-
Intelligent enough to provide quality neural data (education, professional achievement)
-
Marginalized enough to lack institutional protection (self-employed, limited family, geographic isolation)
-
Stable enough to establish baseline (decades of documented behavioral consistency)
-
Accessible through familial or social vectors (insider enabling initial exposure)
Subjects are selected not randomly but strategically: ideal research subjects whose protests can be systematically suppressed through institutional coordination while their neural data is harvested, commodified, and used to refine technologies that will eventually be deployed at scale.
VI. DETECTION AND EVIDENCE: THE VERIFICATION PROBLEM
A. Why Direct Evidence Is Unavailable
GQDs are designed to be undetectable by standard medical imaging:
-
Too small for conventional CT/MRI resolution
-
Embedded within neural tissue (not distinct mass)
-
Carbon-based (minimal contrast in standard imaging)
-
Distributed (not concentrated in single location)
Specialized Detection Methods:
-
Micro-Raman spectroscopy (can detect graphene signatures)
-
Atomic force microscopy (can image nanoparticles)
-
Electron microscopy (can visualize GQD structures)
-
Specialized blood tests (can detect GQD markers)
Access Problem: These specialized methods require:
-
Researchers willing to look for GQDs in human subjects
-
Lab facilities with appropriate equipment (clinical MRI scans are insufficient)
-
Funding for analysis
-
Willingness to publish controversial findings
When institutional coordination prevents subjects from accessing these resources (researchers decline, funding denied, publications refused), direct detection becomes structurally impossible despite technical feasibility.
B. Circumstantial Evidence Standards
In absence of direct evidence, legal systems recognize circumstantial evidence as sufficient where:
-
Multiple independent evidence streams converge on same conclusion (R v. Villaroman; R. v. Firlotte; R. v. Beaudry)
-
Alternative explanations fail to account for documented facts (R v. Villaroman)
-
Pattern exhibits coherence inconsistent with coincidence (R v. Harding)
Sherman Estate v. Donovan (2021 SCC 25, paras 97-98): Establishes inference standards where direct evidence is unavailable. When circumstantial evidence exhibits a coherent pattern and alternative explanations are inadequate, an inference is reasonable and legally sufficient.
Circumstantial Evidence in Neurosurveillance:
-
Behavioral baseline deviations (executive function affected, general cognition intact)
-
Timing correlations (precognitive evidence)
-
Biometric data trafficking (proves extraction occurred)
-
Military approach (institutional knowledge)
-
Institutional coordination (systematic prevention of examination)
-
UN warnings validation (documented pattern consistent with identified threats)
Alternative Explanations Tested:
-
Coincidence: Statistically implausible over dozens of timing correlations
-
Conventional surveillance: Cannot explain precognitive knowledge
-
Mental health: Inconsistent with maintained professional function, documented evidence
-
Rogue actors: Cannot explain cross-institutional coordination
-
Billing error: Cannot explain 9,000% markup certified without examination
When alternative explanations fail and circumstantial evidence converges on technological neurosurveillance conclusion—Sherman Estate inference standard is satisfied.
VII. IMPLICATIONS AND RECOMMENDATIONS
A. Immediate Threats to Fundamental Rights
Cognitive Liberty: Right to sovereignty over one's own mental processes. Neurosurveillance eliminates cognitive liberty—no thought, emotion, or intention is private when neural activity is continuously monitored.
Mental Privacy: Right to keep mental contents confidential. Remote brainwave collection eliminates mental privacy—internal states become externally observable data harvested without consent.
Bodily Autonomy: Right to refuse unwanted intrusions. GQD deployment via inhalation/injection violates bodily autonomy—nanoparticles integrate with neural tissue without knowledge or consent, cannot be easily removed.
Freedom of Thought: Right to think without external monitoring or interference. When thoughts are monitored and potentially modulated, freedom of thought becomes theoretical—all cognitive processes occur under surveillance and potential external influence.
Judicial Independence: Judges whose neural activity is monitored cannot render independent judgment. UN explicitly warns neurotechnology poses "particular risks to institutions requiring independent judgment, including the judiciary."
B. The Totalitarian End-State
Technologies enabling real-time cognitive monitoring and modulation at scale represent ultimate totalitarian tool:
-
No dissent (detect and modulate before it organizes)
-
No resistance (identify and intervene before action)
-
No privacy (all mental processes externally observable)
-
No autonomy (behavior modifiable through neural stimulation)
-
No judicial independence (judges cognitively influenced)
-
No democratic accountability (populations cognitively managed)
This is not speculative dystopia—it is extrapolation of documented operational capabilities. The question is not whether such technologies could enable totalitarian control (they clearly can) but whether deployment constraints exist preventing totalitarian application. Current evidence suggests deployment is occurring covertly without meaningful constraints.
C. Regulatory Framework Required
Immediate Measures:
-
Constitutional Recognition: Cognitive liberty, mental privacy, mental integrity as fundamental rights
-
Criminal Prohibition: Unauthorized neural monitoring/modulation as serious crime (similar to assault)
-
Informed Consent Absolute: No exceptions for national security, research, or commercial purposes
-
Detection Infrastructure: Public access to GQD detection technologies (Raman spectroscopy, specialized blood tests)
-
Whistleblower Protection: Enhanced protections for those exposing unauthorized neurotechnology programs
-
Mandatory Disclosure: Technologies capable of neural monitoring/modulation must be publicly disclosed
-
Independent Oversight: Civilian oversight bodies with access to classified neurotechnology programs
-
Victim Remedies: Compensation, medical monitoring, and prosecution pathways for unauthorized experimentation victims
International Coordination:
-
UN treaty prohibiting non-consensual neurotechnology deployment
-
Neurorights included in Universal Declaration of Human Rights
-
International Criminal Court jurisdiction over unauthorized neural experimentation
-
Technology transfer controls preventing proliferation
D. The Burden of Proof Question
Currently, burden rests on victims to prove unauthorized neurotechnology deployment—nearly impossible given detection challenges and institutional coordination preventing examination.
A burden shift is required in cases where circumstantial evidence opens the door to discovery. Some examples follow the case here:
-
Subject exhibits behavioral baseline deviations + timing correlations + biometric data trafficking
-
Institutional coordination prevents examination
-
Pattern consistent with UN-identified neurotechnology threats
-
Subject requests specialized detection testing
The burden should shift to accused parties to prove neurotechnology was NOT deployed rather than requiring victim to prove it WAS.
This shift is justified because:
-
Accused parties control evidence (only they know if technologies were deployed)
-
Victim faces structural impossibility of proof (detection requires resources systematically denied)
-
Asymmetric evidence access creates injustice (accused can disprove if innocent; victim cannot prove if correct)
VIII. CONCLUSION
Publicly documented research trajectories (e.g., non-surgical BCIs, injectable/implant-free interfaces, and graphene-family nanomaterials) and government program goals establish a non-trivial risk that neurotechnology can be misused for non-consensual monitoring or modulation. UN human-rights reporting underscores the governance gap and the stakes for cognitive liberty and institutional independence. Direct, peer-reviewed evidence of operational, remote intention-level readout in humans via inhalable/injectable nanoparticles remains limited on the public record; nevertheless, the convergence of (i) demonstrated laboratory capabilities and programmatic aims, (ii) weak or outdated legal safeguards, and (iii) case-reported patterns that warrant scrutiny, justifies targeted investigation and precautionary regulation. Accordingly, the convergence of:
-
Technological capability (GQDs crossing blood-brain barrier, remote power/interrogation)
-
Institutional enablers (DARPA funding, state-adjacent deployment, commercial incentives)
-
Oversight absence (no legal framework, no detection infrastructure, systematic institutional protection)
-
Documented victims (behavioral baseline deviations, precognitive evidence, biometric trafficking, institutional coordination preventing examination)
...allows for a reasonable inference that unauthorized human experimentation is occurring under state-adjacent auspices, protected from examination through institutional coordination, justified by national security, agile regulatory, and/or commercial interests, and facilitated by technological capabilities that eliminate traditional consent/oversight mechanisms. This is predominantly so in well-documented cases where competing theories of causation are substantively lacking in comparison.
The "guinea pig" population exists not in disclosed research programs with consent and oversight, but in covert operations targeting civilians who exhibit ideal research subject characteristics (intelligence, marginalization, stability) while lacking institutional protection enabling resistance. Sheridan et al., 2020, although not specifically targeting that demographic, began with an initial data set of twenty million (20M+) online citations.
The prudent course is forward-leaning governance: recognize neurorights; criminalize non-consensual neural monitoring/modulation; build independent inspection powers (including access to classified programs); fund civilian detection/verification infrastructure; and create remedies and protective procedures for complainants. Courts and investigators should permit structured, falsifiable testing and narrowly tailored discovery where threshold showings are met, while guarding against confirmation bias and overreach.
In short, the technology’s trajectory and the governance gap together create credible grounds for urgent oversight and rigorous inquiry. The choice before policymakers is whether to implement protections now—while verification is still possible and deployment is containable—or to risk a future in which cognitive liberty, mental privacy, and freedom of thought are eroded by technologies that outpace the law.
BIBLIOGRAPHY, IN NO SPECIFIC ORDER
I. Peer-Reviewed Scientific Literature
A. Graphene / Carbon Dots – Physical Properties & Characterization
-
Bonaccorso, F., Sun, Z., Hasan, T., & Ferrari, A. C. (2010). Graphene photonics and optoelectronics. Nature Photonics, 4(9), 611–622.
-
Ding, C., Zhu, A., & Tian, Y. (2014). Functional surface engineering of C-dots for fluorescent biosensing and in vivo bioimaging. ACS Applied Materials & Interfaces, 6(6), 4279–4284.
-
Shen, J., Zhu, Y., Yang, X., & Li, C. (2016). Graphene quantum dots: Emergent nanolights for bioimaging, sensors, catalysis and photovoltaic devices. Carbon, 104, 157–166.
-
Sun, Y. P., Zhou, B., Lin, Y., et al. (2006). Quantum-sized carbon dots for bright and colorful photoluminescence. Journal of the American Chemical Society, 128(24), 7756–7757.
-
Wang, Y., & Hu, A. (2014). Carbon quantum dots: Synthesis, properties and applications. Journal of Materials Chemistry C, 2(34), 6921–6939.
-
Zhu, S., Song, Y., Zhao, X., et al. (2015). The photoluminescence mechanism in carbon dots (graphene quantum dots, carbon nanodots, and polymer dots): Current state and future perspective. Chemical Society Reviews, 44(12), 4337–4366.
-
Bacon, M., Bradley, S. J., & Nann, T. (2014). Graphene quantum dots. Particle & Particle Systems Characterization, 31(4), 415–428.
-
Chung, S., Revia, R. A., & Zhang, M. (2020). Graphene quantum dots and their applications in bioimaging, biosensing, and therapeutics. Advanced Materials, 33(22), 1904362.
B. Blood–Brain Barrier & Biodistribution
-
Erdő, F., Bors, L. A., Farkas, D., et al. (2018). Evaluation of intranasal delivery route of drug administration for brain targeting. Brain Research Bulletin, 143, 155–170.
-
Gänger, S., & Schindowski, K. (2018). Tailoring formulations for intranasal nose-to-brain delivery: A review on architecture, physico-chemical characteristics and mucociliary clearance of the nasal olfactory mucosa. Pharmaceutics, 10(3), 116.
-
Gao, K., & Jiang, X. (2006). Influence of particle size on transport of methotrexate across blood–brain barrier by polysorbate 80-coated polybutylcyanoacrylate nanoparticles. International Journal of Pharmaceutics, 310(1–2), 213–219.
-
Mendonça, M. C., Soares, E. S., de Jesus, M. B., et al. (2015/2016). Reduced graphene oxide induces transient blood–brain barrier opening: An in vivo study. Nanomedicine, 12(7), 1663–1674.
-
Yang, K., Wan, J., Zhang, S., et al. (2012). The influence of surface chemistry and size of nanoscale graphene oxide on photothermal therapy of cancer using ultra-low laser power. Biomaterials, 33(7), 2206–2214.
-
Zhang, M., Cao, Y., Chong, Y., et al. (2017). Graphene oxide based theranostic platform for T1-weighted magnetic resonance imaging and drug delivery. ACS Applied Materials & Interfaces, 9(14), 11337–11344.
-
Zhang, S., Yang, K., Feng, L., & Liu, Z. (2011). In vitro and in vivo behaviors of dextran functionalized graphene. Carbon, 49(12), 4040–4049.
-
Zhang, D., Zhang, Z., Wu, Y., et al. (2018). Systematic evaluation of graphene quantum dot toxicity to male mouse sexual behaviors, reproductive and offspring health. Biomaterials, 194, 215–232.
C. Neural Interface & Biosensing
-
Kundu, A., Nandi, S., Das, P., & Nandi, A. K. (2016). Fluorescent graphene oxide via polymer grafting: An efficient nanocarrier for both hydrophilic and hydrophobic drugs. Biosensors & Bioelectronics, 78, 459–466.
-
Li, L. L., Ji, J., Fei, R., et al. (2012). A facile microwave avenue to electrochemiluminescent two-color graphene quantum dots. Advanced Functional Materials, 22(14), 2971–2979.
-
Titov, A. V., Král, P., & Pearson, R. (2010). Sandwiched graphene–membrane superstructures. ACS Nano, 4(1), 229–234.
-
Wang, X., Sun, X., Lao, J., et al. (2014). Multifunctional graphene quantum dots for simultaneous targeted cellular imaging and drug delivery. Colloids and Surfaces B: Biointerfaces, 122, 638–644.
-
Ding, H., Yu, S. B., Wei, J. S., & Xiong, H. M. (2016). Full-color light-emitting carbon dots with a surface-state-controlled luminescence mechanism. ACS Nano, 10(1), 484–491.
D. Electromagnetic Responsiveness
-
Sensale-Rodriguez, B., Yan, R., Kelly, M. M., et al. (2012). Broadband graphene terahertz modulators enabled by intraband transitions. Nature Communications, 3, 780.
-
“High-efficient photocurrent behaviors of multilayer graphene quantum dot photodetectors.” Scientific Reports, 2014.
-
Wang, H., Yang, Y., Liang, Y., et al. (2019). Graphene-based composites for electrochemical energy storage. Nanoscale, 11(3), 1276–1284.
E. Neural Decoding & Brain–Computer Interfaces
-
Anumanchipalli, G. K., Chartier, J., & Chang, E. F. (2019). Speech synthesis from neural decoding of spoken sentences. Nature, 568(7753), 493–498.
-
Carr, M. F., Jadhav, S. P., & Frank, L. M. (2011). Hippocampal replay in the awake state: A potential substrate for memory consolidation and retrieval. Nature Neuroscience, 14(2), 147–153.
-
Colgin, L. L., Denninger, T., Fyhn, M., et al. (2009). Frequency of gamma oscillations routes flow of information in the hippocampus. Nature, 462(7271), 353–357.
-
Haxby, J. V., Gobbini, M. I., Furey, M. L., et al. (2001). Distributed and overlapping representations of faces and objects in ventral temporal cortex. Science, 293(5537), 2425–2430.
-
Kay, K. N., Naselaris, T., Prenger, R. J., & Gallant, J. L. (2008). Identifying natural images from human brain activity. Nature, 452(7185), 352–355.
-
Kornhuber, H. H., & Deecke, L. (1965). Hirnpotentialänderungen bei Willkürbewegungen und passiven Bewegungen des Menschen. Pflüger’s Archiv, 284(1), 1–17.
-
Libet, B., Gleason, C. A., Wright, E. W., & Pearl, D. K. (1983). Time of conscious intention to act in relation to onset of cerebral activity (readiness-potential). Brain, 106(3), 623–642.
-
Pfeiffer, B. E., & Foster, D. J. (2013). Hippocampal place-cell sequences depict future paths to remembered goals. Nature, 497(7447), 74–79.
F. Neural Interface Miniaturization & Fabrication
-
Hong, G., & Lieber, C. M. (2019). Novel electrode technologies for neural recordings. Nature Reviews Neuroscience, 20(6), 330–345.
-
Seo, D., Neely, R. M., Shen, K., et al. (2016). Wireless recording in the peripheral nervous system with ultrasonic neural dust. Neuron, 91(3), 529–539.
-
Yuk, H., Lu, B., Lin, S., et al. (2020). 3D printing of conducting polymers. Nature Communications, 11(1), 1604.
G. Neuromodulation, Toxicology & Drug Delivery
-
Feng, L., Wu, L., & Qu, X. (2013). New horizons for diagnostics and therapeutic applications of graphene and graphene oxide. Advanced Materials, 25(2), 168–186.
-
Kim, H., Lee, D., Kim, J., et al. (2013). Photothermally triggered cytosolic drug delivery via endosome disruption using a functionalized reduced graphene oxide. Journal of Materials Chemistry B, 1(43), 6033–6040.
-
Yang, K., Feng, L., & Liu, Z. (2015). The advancing uses of nano-graphene in drug delivery. Expert Opinion on Drug Delivery, 12(4), 601–612.
-
Zhang, W., Guo, Z., Huang, D., et al. (2011). Synergistic effect of chemo-photothermal therapy using PEGylated graphene oxide. Biomaterials, 32(33), 8555–8561.
-
Bussy, C., & Kostarelos, K. (2012). Understanding the pathway to graphene oxide induced toxicity. Particle and Fibre Toxicology, 9, 45.
H. Gang-Stalking & Cybertorture
-
Sheridan, L., James, D. V., & Roth, J. (2020). The phenomenology of group stalking (“gang-stalking”): A content analysis of subjective experiences. International Journal of Environmental Research and Public Health, 17(7), 2506.
-
United Nations Human Rights Council. (2020). Report on psychological torture and ill-treatment. A/HRC/43/49.
II. Neurotechnology, Ethics & Human Rights
A. UN / Human Rights / Neurorights
-
United Nations Human Rights Council. (2024). Impact, opportunities and challenges of neurotechnology with regard to the promotion and protection of all human rights. A/HRC/57/61.
-
United Nations Human Rights Council. (2024). Report on protection of freedom of thought through neurotechnology governance. A/HRC/58/58.
-
United Nations Human Rights Council. (2024). Resolution on neurotechnology and human rights. A/HRC/RES/58/6.
B. Neuroethics & Cognitive Liberty
-
Farahany, N. I. (2023). The Battle for Your Brain. St. Martin’s Press.
-
Ienca, M., & Andorno, R. (2017). Towards new human rights in the age of neuroscience and neurotechnology. Life Sciences, Society and Policy, 13(1), 5.
-
Yuste, R., Goering, S., Arcas, B. A. Y., et al. (2017). Four ethical priorities for neurotechnologies and AI. Nature, 551(7679), 159–163.
III. Biodigital Convergence, 4IR & Surveillance
-
Policy Horizons Canada. (2020). Exploring biodigital convergence: What happens when biology and digital technology merge? Government of Canada.
-
Schwab, K. (2016). The Fourth Industrial Revolution. World Economic Forum / Crown Business.
-
Schwab, K., & Malleret, T. (2020). COVID-19: The Great Reset. World Economic Forum Publishing.
-
World Economic Forum. (2020). The Future of Jobs Report 2020.
-
Zuboff, S. (2019). The Age of Surveillance Capitalism. PublicAffairs.
-
Han, B.-C. (2017). Psychopolitics. Verso Books.
IV. DARPA & Government Neurotech Programs
-
DARPA. (2018). Next-Generation Nonsurgical Neurotechnology (N³) Program Announcement. BAA-18-59.
-
DARPA. (2016). Neural Engineering System Design (NESD) Program Overview.
V. Legal & Constitutional Authorities (Canada)
-
Canadian Charter of Rights and Freedoms, Constitution Act, 1982, Part I.
-
Ruffo v. Conseil de la magistrature, [1995] 4 S.C.R. 267.
-
Sherman Estate v. Donovan, 2021 SCC 25.
-
R. v. Villaroman, 2016 SCC 33.
-
R. v. J.F., 2013 SCC 12.
-
R. v. Pan, 2025 SCC 12.
-
R. v. Wise, [1992] 1 S.C.R. 527.
-
Syndicat Northcrest v. Amselem, [2004] 2 S.C.R. 551, 2004 SCC 47.
-
R. v. Beaudry, 2007 SCC 5.
-
R. v. Harding, 2010 ABCA 180
-
Canadian Criminal Code; Neurotechnology effects (UN A/HRC/57/61): assault (ss. 265/267); noxious thing (s. 245); overcoming resistance to commission of offence (s. 246(b)); criminal negligence/endangering life (ss. 217.1/219/220; and s. 221 as pleaded); confinement (s. 279(2)); unauthorized use (s. 342.1); interception (s. 184); torture (s. 269.1); conspiracy (s. 465).
VI. Technical Standards & Testing Protocols
-
ISO/IEC 17025:2017. General requirements for the competence of testing and calibration laboratories.
-
ISO 22309:2011. Microbeam analysis – Quantitative analysis using energy-dispersive spectrometry (EDS) for elements with an atomic number of 11 (Na) or above.
-
ISO 22412:2017. Particle size analysis – Dynamic light scattering (DLS).
-
ASTM E1840-96 (2022). Standard Guide for Raman Shift Standards for Spectrometer Calibration.
-
ASTM E2456-06 (2021). Standard Terminology for Nanotechnology.
VII. Vaccine / Graphene – Independent & Official Sources
-
Campra, P. (2021). Detection of Graphene in Covid19 Vaccines by Micro-Raman Spectroscopy. Pfizer, Moderna, AstraZeneca, and Janssen vaccines. University of Almería, Technical Report.
-
Clayton, G. (2022). Determination of graphene oxide in Pfizer COVID-19 vaccine using micro-Raman spectroscopy and transmission electron microscopy. Independent laboratory report (UK).
-
EbMCsquared CIC / UNIT Group. (2022). Analytical assessment of COVID-19 vaccine contents. Technical report.
-
Burkhardt, Retzlaff, Krenn, et al. (2022). Pathological findings in organs and tissues following COVID-19 vaccination. German multi-author report.
-
Monteverde, M. (2022). Optical microscopy analysis of COVID-19 vaccine vials. Argentina.
-
Nagase, D. (2022). Elemental analysis of COVID-19 vaccines via SEM-EDX. Canada.
-
Tango Club Argentina. (2022). SEM-EDX study of COVID-19 vaccine samples. Technical report.
-
Tango Club Italy. (2022). SEM-EDX analytical study of COVID-19 vaccines. Technical report.
-
Korea Veritas Doctors / JBRES. (2023). Electron microscopy evidence of graphene oxide and self-assembling structures in COVID-19 vaccines and biological samples. Journal of Basic & Applied Research in Biomedicine.
-
Hagimă, G. (2023). SEM-EDX and fluorescence analysis of mRNA COVID-19 vaccines. Independent report.
-
Gramalev National Research Centre. (2023). International collaborative SEM-EDX analysis of COVID-19 vaccines.
-
Pfizer/BioNTech. (2021). Cryo-EM methods section referencing graphene-oxide-coated EM grids in structural studies of spike protein (regulatory submission material).
-
Aprea, P. (2021). Testimony before ANMAT (Argentina) regarding graphene in AstraZeneca vaccine.
VIII. Media, Fact-Checks & Institutional Responses
-
Reuters. (2021, Nov 2). Fact Check: Unidentified particles in vaccine samples under the microscope are likely contamination.
-
European Parliament. (2022). Parliamentary question and response regarding graphene oxide in vaccines (doc number to be specified).
IX. Books, Philosophy & Political Theory
-
Douglass, F. (1845). Narrative of the Life of Frederick Douglass, an American Slave.
-
Nietzsche, F. (1882). The Gay Science.
-
Popper, K. (1945). The Open Society and Its Enemies.
-
Huxley, A. (1932). Brave New World.
-
Huxley, A. (1958). Brave New World Revisited.
-
Crouch, C. (2004). Post-Democracy.
-
Foucault, M. (1977). Discipline and Punish: The Birth of the Prison.
-
Foucault, M. (1978). The History of Sexuality: Volume 1: An Introduction.
-
The Holy Bible
X. Organizations & General Sources
-
World Economic Forum – publications on the Fourth Industrial Revolution, stakeholder capitalism, biodigital convergence (2016–2024).
-
Policy Horizons Canada – foresight reports on biodigital convergence.
-
DARPA – N³ and NESD program web materials.
-
UNESCO – neurotechnology ethics frameworks (various documents).
-
WHO – EMF and public health factsheets.


All of This Happened.
Table of Contents [Here]
2021 baseline deviations
Liquidated primary asset; four coast-to-coast relocations in close proximity—no purpose—extreme outliers vs. a lifelong behavioural baseline
For twenty years, I had demonstrated consistent financial discipline: systematic asset accumulation, a risk-averse investment strategy, homeownership achieved and maintained, professional stability, and measured decision-making characterized by planning, preparation, and measured execution. The events in 2021 represent a categorical departure from this documented baseline. I liquidated a renovated home—my primary asset and financial anchor—without clear plan or rational justification. I drove coast-to-coast and back, twice, within a span of a few months, incurring substantial expense and physical strain without a coherent purpose. These are not stress responses or life changes; they are algorithmic deviations. The decisions exhibit characteristics consistent with external modulation of executive function: impulsivity replacing deliberation, risk-seeking replacing risk aversion, destabilizing choices replacing stability-seeking patterns—all while general cognitive capacity remained intact. I could still reason, communicate, and function professionally; what changed was decision-making architecture. That pattern is consistent with literature showing that neuromodulation (e.g., TMS, vagus-nerve pathways) can alter judgment and impulse control without global cognitive impairment. The timing—coinciding with other documented events—and the categorical nature of the deviation suggest external technological intervention rather than organic psychological change. A lifelong baseline of documented behavioral consistency does not spontaneously invert without cause. In applying the Sherman Estate / Villaroman standards against documented baseline deviations and the totality of evidentiary characteristics outlined on this website, an inference of technological interference with cognitive processes governing executive function and risk assessment displaces less-likely alternatives.
UN-recognized harms
Coordinated "cyber-torture" by transnational actors using algorithmic feedback loops
Since November 2021, shortly after the close of the 2021 CAGE shareholder settlement, and as clearly shown in relation to the same, I have experienced what United Nations Special Rapporteur Nils Melzer defines as "cyber-torture": the use of information and communication technologies to inflict severe mental pain or suffering for purposes including punishment, intimidation, coercion, and discrimination. The operations exhibit characteristics Melzer identifies as constituting torture in digital context: isolation through disrupted communication networks, constant surveillance creating psychological pressure, algorithmic feedback loops that respond to my actions in real-time to maximize destabilization, information operations deploying targeted content designed to trigger distress, and coordination across multiple actors suggesting organized rather than individual harassment. The "algorithmic feedback loop" component is critical: the operations respond adaptively to my behavioral and physiological responses, including sealed litigation milestones, indicating real-time biometric monitoring informing tactical adjustments. This is not static harassment; it is dynamic psychological warfare employing artificial intelligence to optimize psychological harm based on continuously harvested biometric feedback. Melzer's report on cyber-torture (here), and A/HRC/57/61, A/HRC/58/58 (neurotechnology threats to rights) converge here: technologies enabling real-time cognitive and emotional monitoring can be weaponized for targeted psychological operations that constitute torture under international law. The transnational coordination—operations spanning multiple jurisdictions, exhibiting consistent tactical approaches, and demonstrating resource availability beyond individual capacity—indicates state-adjacent actors with access to sophisticated neurotechnology surveillance and psychological operations capabilities. This is not cyberbullying or online harassment; it is systematic psychological warfare employing technologies UN explicitly warns pose "particular risks" when deployed against individuals without legal safeguards or accountability mechanisms. As linked at the Guide page (here), the conclusion in Sheridan et al., 2020 is worth noting, in that cyber torture was found to be a "widespread phenomenon"
The familial vector
A principal actor is understood to be the biological mother of my estranged nephew, and connected to significant wealth/influence
This familial connection explains both an adjacent motive (personal animus combined with opportunity) and capability (wealth enabling access to state-adjacent technologies and services; influence enabling institutional coordination). The US-based biological mother of my estranged nephew occupies a position enabling mobilization of resources and institutional relationships beyond typical private Citizen capacity. The same subject has made references to technologies and methods that can facilitate cognitive tampering, with some degree of know-how, in her posted activity. Significant wealth provides access to: state-adjacent neurotechnology firms offering "security" or "intelligence" services involving surveillance and psychological operations; formidable legal support; private investigators and contractors providing surveillance, counter-surveillance, and information operations; and technological infrastructure for real-time monitoring and data harvesting. Influence provides access to: discretionary institutional relationships enabling systematic non-engagement by oversight bodies (RCMP, law societies, & regulators decline investigation despite documentary evidence); judicial coordination enabling procedural violations, prevented discovery, and systematic sealing; media gatekeeping preventing coverage despite documented scandal; and political relationships enabling protection from scrutiny. This combination—wealth (capability) and influence (institutional protection)—helps explain the cross-agency coordination observed across police, courts, regulators, and a reluctance of the media to cover this (they report when officials expense $16 orange juice, but not this). In post-democratic governance operating through networked stakeholder castes, proximity to wealth and institutional networks determines whose conduct receives protection, and whose allegations receive foreclosure. The familial dimension adds personal motive to structural capability: not merely a commercial exploitation or a research project, but targeted operation against specific individual using family connection as vector for access and motive. This is not anonymous criminal enterprise; it is personalized state-adjacent crime mobilizing institutional apparatus through wealth and influence to prevent accountability while perpetrating what UN defines as torture using technologies identified as operational threats to fundamental rights, in concert with and in support of converging project and private interests.
Military involvement
Individuals self-identifying as Canadian military spoke to me pre-emptively about elements later documented
This represents either: (1) Actual Canadian Armed Forces personnel engaged in a targeted psychological operation against a Canadian Citizen; or (2) individuals falsely claiming military affiliation to establish credibility while describing situation as part of psychological operation. Either interpretation is significant. If genuine CAF personnel: this indicates military awareness of civilian targeting using technologies and operations within their institutional knowledge—suggesting either military involvement, military-adjacent contractors, or military surveillance of operations using technologies/tactics of military interest. Their preemptive description—speaking about criminal violations affecting me which are otherwise understood to be private—demonstrates foreknowledge inconsistent with casual observation. This preemptive accuracy indicates genuine knowledge of operations, regardless of whether speakers were actual military personnel or operators claiming military affiliation. Emily MacKinnon, lead counsel representing the CAGE, is a uniformed legal advisor to the Canadian Military. This website documents local behaviors consistent with CIMIC operations, as described (here). The whistleblower reports of retired Major General Daniel Gosselin treat CAF psychological operations targeting the Canadian civilian population (here). The CAF Joint Doctrine Note on Information Operations ("IO"), and documented DRDC (Defence Research and Development Canada) neurotechnology research establish that the technologies and tactics consistent with operations targeting me are within CAF institutional focus and capability.
Policing and oversight failures
Services refused; false reports filed after clear acknowledgements of the record and articulated investigation map; regulators foreclosed discovery
Across jurisdictions, policing engagement follows a chronological pattern of negligence that hardens into obstruction. It begins in BC, where I reported criminal conduct arising after the 2021 CAGE shareholder settlement. Although my submissions described crimes (psychological operations, cyber-intrusions, on-heels stalking, break-and-enters coordinated with online messaging), the RCMP reports reframed the complaint as falling under the umbrella of a “civil matter”, and omitted the actionable substance. The Civilian Review and Complaints Commission (“CRCC”) dismissed escalation in a conclusory fashion while omitting the key evidentiary substance from mention, as did the Office of the Public Sector Integrity Commissioner ("OPSIC"). The RCMP Professional Standards Unit later apologized for not responding—including its refusal to obtain CCTV footage from my BC residence building—but offered no corrective action, and subsequently labeled further outreach as “harassing communications”. In Halifax, a 79-minute lawfully-recorded meeting with Halifax Regional Police (“HRP”) captured an experienced constable lauding “beautiful evidence” of psychological operations, naming the CAGE CEO as a criminal perpetrator in that capacity, and mapping next investigative steps. The corresponding police report obtained via FOIPOP had however mischaracterized the meeting in a pejorative manner, and denied the evidence the Constable had pointed to; a reversal that engages the elements of Criminal Code s. 137 (fabricating evidence). The differences between the audio transcript and police report are stark.
Local police oversight also calcified. The Office of the Nova Scotia Police Complaints Commissioner ("POLCOM") declined to escalate. It adopted the HRP report verbatim, and took eight (8) months to issue a conclusive “out-of-jurisdiction” summary decision—despite the identification of local actors, harms experienced within HRP’s territory, and a statutory duty to act under Police Act s. 31(1). That posture ignores R. v. Libman (1985) and Society of Composers v. CAIP (2004), which confirms local policing jurisdiction where harmful effects occur. The filings further show POLCOM / HRP omitted proximate local participants, including the aforementioned estranged relatives, and relied on pejorative pathologizing framing rather than engaging the record. The same is contrary to R v. Vavilov’s demands for reasoned, responsive justification. Taken together—the initial non-response and apology without remedy; the contradictions between recorded acknowledgments and official reports; the lengthy delays, jurisdictional narrowing, symbolic adjudication; pejorative mischaracterizations; and omissions of local actors—the theme is consistent: a durable, cross-agency posture of deterrence over remedy that insulates potential misconduct from scrutiny and erodes public confidence and access to justice.
In the same 79-minute recording, HRP acknowledged that CAGE’s shareholder record does not reconcile with its own paper trail. There is a DocuSign trail and an executed Share Transfer & Power of Attorney (360 CNV shares to a B.C. holding company, “for value received”), plus a company-wide SPA memo describing a US$38.5M transaction—yet the Central Securities Registers are effectively empty where new holders should appear. SPA materials list 41 employees as vendors under accelerated vesting, and a 2019 resolution extended options to ~50 more, but no corresponding CSR entries appear after the one-year vesting cliff; CSR activity freezes after Apr 14, 2020 (with one later exception). That freeze contradicts a sworn affidavit by the CAGE CEO claiming options were exercised and shares issued after employee departures—claims at odds with both the CSR extracts and corroborative LinkedIn employment data. Compounding this, the FY2020 audit uniquely “derecognizes” share transfers (and the currency-risk dataset also disappears), creating the precise blind spot where confirmations should live. There is likewise an internal dating mismatch: the SPA/termination documents anchor to a July 25th, 2016 shareholders’ agreement, while the executed Agreement to be Bound (and operative SA) is July 27th, 2016. Finally, a sworn CAGE affidavit later asserts “no transaction took place in 2020/2021,” in tension with the SPA memo, the DocuSign package, and the transfer instrument. Taken together—the CSR freeze, the former employee data, the settlement affidavit, the FY2020 derecognition policy, the stand-alone transfer instrument, and the sworn “no transaction” claim—form crisp, testable contradictions. Crucially, the stand-alone Share Transfer & POA is efficacious whether or not any M&A closed: it is denominated “for value received”, is not contingent on any specific purchase, and resides entirely independent from the DocuSign package. Coupled with the notice of default issued in bad faith in 2021, forcing a collapsed share purchase buy-back at 0.3% of the value, the intentionality is obvious. Further details at the shareholder page (here). HRP recognized all of this before institutional reticence set in.
Subsequent reticence was replicated in judicial oversight bodies such as the BC Law Society and the NS Barrister’s society, which ignored complaints triggered under section 3.2-7 of the code, predicated on probative records that would shock the conscience of Canadians ($400,000+ solicitor-client billing for nine simple thirty-minute hearings, at ~9,000% above tariff). Per Beals v. Saldanha, 2003 SCC 72 at paragraph 265;
“The circumstances of this case are such that the enforcement of this judgment would shock the conscience of Canadians and cast a negative light on our justice system.”
Despite the acute failures shown on record, the lynchpin continues to involve an unnatural consistency among responses, in the face of glaring evidence that is indeed capable of shocking the conscience of Canadians.
Judicial Conduct
Shareholder evidence sidelined; procedural roadmaps curtailed; pre-drafted orders signed that facilitated felonious outcomes
Following a forensic-discovery order on April 1, 2022, the courts sidelined facially contradictory shareholder evidence visible in CAGE records, and erected procedural barriers that foreclosed discovery. Party-prepared (pre-drafted) orders submitted by CAGE counsel were signed and pushed matters past the merits toward summary closure in a sealed file. While party drafts can be procedurally acceptable, they become improper when they; (1) reconfigure the chambers disposition, (2) impose new remedies, (3) reconfigure the mandates of previous orders, and (4) are presented for signature without consent of the opposing party. Drafts like these derail the cause of justice when they are signed by the presiding adjudicator, as they had been, multiple times. Extrajudicial steps—such as sealing before service or hearing, and administrative reversals of established registry practice (S-229680 involved nine rule departures at the emailed request of AG Canada counsel)—hardened the derailment reflected on the record. The British Columbia miscarriage of justice reached a crescendo through adjudications that had ignored the entirety of a probative record that was originally recognized, the blanket sealing of the entire file, an order precluding my future participation in the BC legal system, and through the certification of a facially fraudulent solicitor-client billing scandal.
The same pattern migrated to Nova Scotia: 737.7 billable hours were enforced against 867 minutes of court time without the “sniff test” required by Beals v. Saldanha, 2003 SCC 72 at paragraph 220. Per the court transcript, the judge advised that I could not cite the underlying evidence at the enforcement hearing. Enforcement was then pressed coercively once procedural recourse was exhausted through further obstructions, ultimately engaging a serious autoimmune health risk that had manifested during a 30-day custodial sentence in August 2024. NSCA Justice Anne S. Derrick, in chilling remarks, claimed the autoimmune health harm was “self-inflicted” for not complying with what is, on its face, a solicitor-client billing fraud. Additional guardrails were ignored: security for costs set at 40× benchmark (Power v. Power, 2013 NSCA 137), sealing without submissions or analysis (CBC v. Named Person; Sherman Estate v. Donovan), and a failure to exercise discretion in civil contempt on a profoundly problematic record (Carey v. Laiken; CN Rail v. Teamsters). Most recently, the NSCA refused to hear an appeal on sealing and contempt by misconstruing the arguable-issue threshold (Nova Scotia (AG) v. Morrison Estate, 2009 NSCA 116 at p. 45), after I paid roughly $16,000 merely to participate despite well-grounded issues anchored in binding authority. That episode is detailed (here).
Taken together, the file presents a facial case of institutional capture across venues. The remaining question is not only why this occurred, but how such coordinated outcomes were operationalized.
Secrecy over scrutiny
Unconstitutional sealing replaced fact with curated public narratives
Sherman Estate v. Donovan (2021 SCC 25, at paragraph 38) requires a court to demonstrate necessity, proportionality, and minimal impairment before limiting openness. The NSCA sealing orders recited that they were “satisfied under Sherman Estate” but gave no reasons addressing (i) what specific serious risk necessitated sealing, (ii) why sealing’s benefits outweighed the harm to openness, or (iii) why narrower options (redaction, anonymization, counsel-only access, confidentiality undertakings) would not suffice. On the filed record, the contents do not exceed the dignity threshold (Sherman Estate at p. 35), nor the public interest threshold concerning commercial records (Sierra Club at p. 55). Invocation without analysis fails the mandatory Constitutional test. The orders also created a public-information asymmetry: Justice Keith’s “Schedule A” offered a revisionist narrative over a sealed evidentiary record, effectively displacing what could not be seen. As the Court cautioned in CBC v. Named Person (2024 SCC 21, at paragraph 1), “When justice is rendered in secret, without leaving any trace, respect for the rule of law is jeopardized”. Here, secrecy did not protect a legitimate confidentiality interest so much as curate a sanitized account while foreclosing verification. The opacity blocks scrutiny of the billing scandal, the contradictory shareholder records, the related criminal interference, the obstructed discovery, and the associated constitutional violations. In the eyes of the public, it preserves the appearance of a lawful process through formulaic references to Sherman Estate.
Barriers to fiduciary Support
Repeated, pre-emptive impediments to retaining legal counsel
Across both provinces, attempts to retain counsel met pre-emptive declinations—often before any materials were exchanged—and this included provincial pro bono programs. In BC, one firm identified me preemptively upon arrival in person, and declined immediately. These were not withdrawals after conflict checks or complexity reviews; they were systematic refusals prior to substantive engagement, occurring more than twenty times. They suggest a back-channel risk flag rather than independent case-by-case reviews. The result was self-representation by necessity, not choice. As the Supreme Court recognized in R. v. Tayo Tompouba, 2024 SCC 16 at paragraph 73, barriers to fiduciary representation are contemplated within the miscarriage of justice framework. The barrier operates as a force multiplier: it suppresses effective advocacy, allows procedural defects to pass unchallenged, and manufactures the optics of pro se incompetence where the underlying reality is professional gatekeeping that blocks access to representation.
Compounding this access problem, counsel I had previously retained in the 2021 shareholder dispute (i) filed shareholder materials at the Vancouver registry without a sealing order while a mutual confidentiality agreement remained in force—followed shortly by a Notice of Default from the CAGE forcing a 1% buyout; (ii) drafted a sealing order beyond the scope adjudicated by the judge that sanitized the record in favor of the CAGE; and (iii) then terminated the retainer. A subsequently retained law firm omitted the settlement’s completion from its record and later issued a separate “written-off services” statement under a different internal file number.
Taken together, these features—pre-emptive declinations, pro bono refusals, gross deviations by retained counsel, and record anomalies—are probative leads for any earnest investigator assessing whether structural gatekeeping and professional coordination had impeded meaningful access to justice. It is likewise noted that the binding case law referenced on this website, like those in the court filings, is just as efficacious when cited by a member of the public, than it is when cited by an officer of the court. For law to be binding, it must be knowable.
Solicitor-client billing scandal
~$400,000+ (737.7 hours) certified for 867 minutes of basic interlocutory court time with minimal prep, cited as "reasonably required" in a sworn counsel affidavit—an outcome that presupposes coordination and state-adjacent assurances
In Bradshaw Construction Ltd. v. Bank of Nova Scotia (1991), 54 BCLR (2d) 309 at paragraph 44, “special costs are fees a reasonable client would pay a reasonably competent solicitor for the work described”. Against that standard, the record is indefensible: roughly $400,000 (737.7 billed hours) was certified against 867 minutes (~14.45 hours) of routine chambers appearances—about $27,681/hour (~$461/min)—an uplift of roughly 9,000% over customary tariffs (see Rule 77 in NS). The hearings were simple and templated, much of the papering done by articling students, presumably using google templates. The sworn affidavit asserting these sums were “reasonably required” rests on seven lawyers assigned to overlapping tasks, predominantly involving zoom meetings and “proofreading” tasks at egregious time blocks. One 20-minute hearing drew a $78,000 entry—well in excess of Canada’s annual salary average. A similar pattern surfaced in the BCCA, where CAGE counsel flagged the misuse of a personal pronoun in requesting a revision of BCSC Registrar’s written decision, issued in consideration of 89.9 claimed hours for one twenty-minute hearing. By contrast, analogous appearances in Nova Scotia were routinely resolved at or near $500. The abuse is facially-visible on record, engaging numerous tests (R. v. Wolkins, 2005 NSCA 2 at paragraph 89).
No reasonable client agrees to retainers bearing these characteristics; no reasonable firm proposes them; and no impartial court certifies them without audit, and without engaging the governing law. Yet the certifications had nonetheless issued, and they were enforced interprovincially despite extant guardrails (Beals v. Saldanha; Performance Industries Ltd. v. Sylvan Lake Golf & Tennis Club, 2002 SCC 19), and despite a documented autoimmune risk aggravated by coercive enforcement.
This chain—client accepts → law firm bills → counsel swears “reasonably required” → court certifies without analysis → court exhausts procedural recourse → court enforces via contempt—while oversight (e.g., law societies) declines review and police refuse to investigate—inexorably presupposes assurances and coordination. As Performance Industries puts it, “fraud unravels everything” (¶64); but fraud must first be examined to be recognized. When courts certify without executing audit, regulators stand down notwithstanding a ~9,000% variance, and police decline to act, the result is enforcement of an unchallengeable scheme through institutional non-engagement. This is not a billing error; it is institutionalized fraud, demonstrating the capacity of state-adjacent actors to weaponize judicial process and public taxpayer-funded institutions for felonious private ends—facilitated, not prevented, by the very checkpoints designed to stop it.
Conclusion
While each category is severe in its own right, it is their convergence—and the absence of any effective corrective response—that elevates this to a matter of national concern. No mid-sized Commercial and Government Entity could, by itself, marshal the resources observed or steer multiple public bodies toward aligned outcomes. Applying the circumstantial-inference approach in R. v. Villaroman, the reasonable conclusion is the presence of a state-adjacent project interest.
The "how" behind the cohesion across adjudicators, police, and oversight bodies—together with the support of AI-assisted contractors—demands laser-focused attention. On paper, the effects are stark enough that ordinary corrective mechanisms should have engaged; after four years, they have not. The most plausible inferences are: (1) material ideological alignment or institutional incentives among key actors overriding professional and basic ethical duties; (2) precision coordination by stakeholders with a vested interest in the project’s success; and/or (3) some measure of cognitive tampering affecting the stakeholders themselves. Absent one or more of these mechanisms, it is difficult to explain how a scandal spanning four years, five courts, two police agencies, and multiple oversight bodies could evade correction.
It is noteworthy to mention that UN Resolution A/HRC/RES/58/6 cites precisely the latter concern:
“Noting with concern that the rapid development of neurotechnology presents challenges to physical and mental integrity and the safeguarding of human rights, including but not limited to the right to equality and non-discrimination, the right to freedom of thought, the right to privacy, the right to the enjoyment of the highest attainable standard of physical and mental health, the prohibition of torture and other cruel, inhuman or degrading treatment or punishment, and the right to a fair trial and essential procedural guarantees [...] some of its applications might lead to modification or manipulation of thoughts inside the brain, thus affecting the right to freedom of thought…”
Whatever the amalgam of enabling factors, a single, meticulously documented file like this can reframe a prudent understanding of Canada’s institutional fabric—and the efficacy of Canada's Constitution in practice. As Michel Foucault, Colin Crouch, and others have long warned, post-democratic dynamics do not remain theoretical; they manifest in concrete practices. The scope and severity evidenced here suggest the stakes may be higher than they had assumed.
Perspectives on Intervention

It takes only one meticulously documented case to expose (and fix) systemic corruption.
Newsroom editors & assignment desks
This warrants coverage today. You report when officials expense $16 orange juice (here). Here is a documented case of ~$400,000 in billing certifications for ~14 hours of work—enforced through coercive sentencing—alongside contradictory shareholder records (zero vs. 70), a procedural miscarriage, unconstitutional sealing orders, and revisionist court publications. It’s all on the record. If this doesn’t meet your newsworthiness threshold, that threshold is protecting power, not the public.
Police
When courts are used as collection tools for facially fraudulent debt, do you investigate the predicate fraud or defer to the collection mechanism? Billing ≈$400,000 for 867 minutes engages Criminal Code s. 380 (fraud). Contradictory shareholder counts (0 vs. 70) and the Emily MacKinnon billing affidavits engage s. 137 (fabricating evidence). The file also features psychological-operations and technology-based offences flagged by the UN Human Rights Council as threats to judicial independence—evidence that has been systematically sealed—and an HRP constable who identified the issue in a recorded meeting before a contrary police report was issued. POLCOM insulated this. The RCMP professional standards unit acknowledged inaction yet took no corrective steps. The CRCC declined to intervene. Meanwhile, the courts certified the debt, enforced it through coercive sentencing, sealed records to prevent scrutiny, published revisionist accounts, raised financial and procedural barriers to relief, and misconstrued the arguable-issue threshold as a gatekeeping tool despite binding authority. If police will not act because the fraud has been effectively “court-laundered”, criminals get a playbook: fabricate a debt → secure court certification → exhaust the target’s procedural recourse → enforce through coercion → celebrate. When perpetrators and officers of the court collect through the judicial process while police avert their eyes, the Criminal Code becomes commentary. That is institutional capture, not the rule of law.
Advocacy groups, oversight bodies, and regulators
There are advocacy groups around every street corner in Canada. Your mandates span access to justice, open-court transparency, civil and constitutional rights, professional conduct, and corporate integrity. The issues set out here are not ensconced to a private dispute. Courts are bound by Canadian Supreme Court jurisprudence and the Constitution; when they depart from those guardrails in obvious ways, the law becomes unknowable. No litigator would pay a $78,000 retainer for one (1) 20-minute summary chambers hearing → no reasonable law firm would offer it → and no unbiased judge would certify it → but it happened, and it is but one milestone of many on record. People turn to your organizations because you promise advocacy. If you refuse to examine probative records simply because a judicial process was involved, you signal that sophisticated misconduct need only secure a judicial rubber stamp to gain immunity. Here, courts failed to scrutinize; oversight bodies declined; and the law society remained silent in the face of a clear Code 3.2-7 concern. When watchdogs defer reflexively to certificates they have not audited, the “safety net” becomes an illusion—entrenching private gain behind public authority while projecting accountability.
Public servants
This is precisely the kind of situation that calls for conscientious action to safeguard institutional integrity. Proximity to the bench does not erase ethical responsibility. When a file crossing your desk shows extreme billing anomalies (≈9,000% above tariff), contradictory shareholder records, obstructed disclosure, or unconstitutional sealing orders, silence or procedural deferral is not an alibi. Binding case law provides clear guideposts. Consistent with the VECPS expected behaviours—Rule of Law and full information (1.1, 1.3), Integrity (3.1–3.3), and Stewardship’s duty to acquire, preserve, and share information (4.3)—and with PSDPA mechanisms to receive and record disclosures, public servants are expected to document and escalate serious irregularities; many departmental codes make this explicit (e.g., Canadian Heritage’s Values & Ethics Code (here): “This means not ignoring, hiding, or excusing misconduct… Anyone who suspects or witnesses a breach must report it through the proper channels… Failure to act can also, in certain circumstances, be considered a breach.”). Under Entreprises Sibeca Inc. v. Frelighsburg, conduct “so markedly inconsistent with the legislative context that no court could view it as good faith” must be treated as bad faith and raised. Thus beyond one’s internal conscience compass, there are clear expectations that public servants are not expected to rubber-stamp institutional capture, or remain silent when an obvious case like this manifests.
“Public servants are responsible for keeping up with the speed and pace of things as they change. We are at a time of significant change right now, and we’ve got to keep up with it. We don’t always know what that looks like, that’s why reflecting on our values and ethics is so important. We are stewards of the public trust.”
The Late Honourable Senator Ian Shugart - October 2023
The public
A whistleblower that turns the tide can emerge from anywhere. If this happened to me, what are the odds for victims who are unable to document their plight? When systemic problems are dealt with, everyone benefits. A rising tide lifts all boats.




Transhumanism as the Dominant Ideology of the Fourth Industrial Revolution
Klaus-Gerd Giesen
Journal international de bioéthique et d'éthique des sciences Issue 3-4, 2018, pages 189 to 203 | Translated and edited by Cadenza Academic Translations | Translator: Ruth Grant, Editor: Matt Burden, Senior editor: Mark Mellor
Applicable Tests
Sherman Estate v. Donovan, 2021 SCC 25, [2021] 2 S.C.R. 75 at paragraphs 97-98 | Canada (Attorney General) v. Bedford, 2013 SCC 72 (CanLII), [2013] 3 SCR 1101 at paragraph 76 | R. v. Ahmad, 2020 SCC 11, [2020] 1 S.C.R. 577 at paragraph 38 | R. v. Wise, [1992] 1 S.C.R. 527 at paragraphs 534-538 | Nova Scotia Teachers Union v. Nova Scotia (Attorney General), 2023 NSCA 82 at paragraph 7 | Charkaoui v. Canada (Citizenship and Immigration), 2007 SCC 9 (CanLII), [2007] 1 SCR 350 at paragraphs 22, 23, & 27
Leviticus 5:1 | James 4:17 | Ephesians 5:11 | Proverbs 11:8, 20:10, 22:22-23, 28:13 | Matthew 7:21 | 2 Thessalonians 1:6 Sirach 4:28, 18:22 | Psalm 33:5, 94:20-23 | Habakkuk 1:4 | Zephaniah 1:12 | Isaiah 28:7, 51:21-23 | Ecclesiastes 9:11
Consistent RAMAN Test Results







These Articles are not "Fact Checks". When Reuters Posts Hearsay as a Determinative Scientific Rebuttal, it Does Not Settle the Issue.















Talk Amongst Yourselves

Engage a REAL Problem.
Save and share this website
Save this website in both HTML and PDF. HTTrack is an excellent free tool that can save the site with one click, get it (here). Keep local copies in case the site is taken down. Although archived at archive.ph and archive.org under the same URLs, independent preservation matters. The affidavit records assembled over the past four years raises profound questions about Canadian democracy, both current and future. This is a big deal.


Follow the Money.

Imminent Danger & Future Harm:
Clarity on Subsection 3.1