Crimes Against Humanity and War Crimes Act (S.C. 2000, c. 24) [Link]
Zersetzung


AI-Assisted Psychological Operations Impacting a Lawsuit.

“The police must investigate crime. That is their duty. In the vast majority of cases, they carry out this duty with diligence and care. Occasionally, however, mistakes are made. These mistakes may have drastic consequences."
Hill v. Hamilton‑Wentworth Regional Police Services Board, [2007] 3 S.C.R. 129, 2007 SCC 41 @ paragraph 1
"A post-democratic society is one that continues to have and to use all the institutions of democracy, but in which they increasingly become a formal shell. The energy and innovative drive pass away from the democratic arena and into small circles of a politico-economic elite."
Dr. Colin Crouch, Post Democracy, 2004, ISBN 0-7456-3315-3

"Zersetzung methods are designed to break down, undermine, and paralyze people behind a facade of social normality, in a form of silent repression".
Mike Dennis, Norman LaPorte (2011). ISBN 978-0-857-45-195-8
"The experience of being gang-stalked appears to be a widespread phenomenon that has been subject to little scientific examination. [...] It also serves to confirm the harmful effects of the gang-stalking experience upon sufferers, first set out in the only other study available. These findings constitute a potent reason why gang-stalking should be regarded as an important subject for study."





An Organized Transnational Framework Protected by Courts & Police in Canada, Supported by CAF IA.




Criminal Code (R.S.C., 1985, c. C-46) [Link]
Section 83.22 (1): Every person who knowingly instructs, directly or indirectly, any person to carry out a terrorist activity is guilty of an indictable offense and liable to imprisonment for life.
Section 83.22 (2) An offense may be committed under subsection (1) whether or not;
(a) The terrorist activity is actually carried out;
(b) the accused instructs a particular person to carry out the terrorist activity;
(c) the accused knows the identity of the person whom the accused instructs to carry out the terrorist activity; or
(d) the person whom the accused instructs to carry out the terrorist activity knows that it is a terrorist activity.

Machine-Assisted Audit. [Here]


Layers of Corroborative Data. [Here]




VISUAL EXHIBITS: CIMIC | PsyOp | Cybercrime
A collage of visual exhibits supplemental to the testimony. Delivery via tailored algorithms underscores the mode of sponsorship.




























"Steal and A-Luminum Tariffs"

*CAGE Retainer Fee Claims*
Eight (8) 30-minute hearings w/ minimal prep.
Seven (7) lawyers assigned to overlapping tasks.
The customary tariff is $4,500 ($500 x 8 hearings).

One (1) 20-minute hearing w/ minimal prep.
Third-Party Assurances Were Required.
AKA: "The Billing Delta"

"Special costs are fees a reasonable client would pay a reasonably competent solicitor to do the work described in the bill."
- Bradshaw Construction Ltd. v. Bank of Nova Scotia (1991), 54 B.C.L.R. (2d) 309 (S.C.), para 44








_1.png)
_2.png)
_3.png)



















Denied SCC Docket Entry W/O Written Reasons.


Per Justice Iacobucci in R. v. C.P., 2021 SCC 19 at paragraph 137 concerning the Supreme Court of Canada Docket Test
“There is no basis to believe that a serious argument pointing to a miscarriage of justice would not meet the public interest standard for leave to appeal to the Court. [...] The Supreme Court would and does exercise its leave requirement in accordance with the principles of fundamental justice.”





























Click to View





The New Torture Stack
ABSTRACT
This article tracks the arc from classical PSYOP (JP 3-13.2) through NATO’s cognitive-warfare turn to the UN’s recognition of technology-mediated “cybertorture” (A/HRC/43/49). Drawing on alliance doctrine, Western whistleblower material (GCHQ/JTRIG, Cambridge Analytica), peer-reviewed evidence of organized harassment (Sheridan et al., 2020), and a four-year, time-stamped case study showing sub-24-hour alignment between sealed court events and scripted content across ~50 channels, it shows that tools built for foreign adversaries are being run on domestic targets. The case study’s combination of biometric-use indicators, twenty-agency foreclosure, and +9,000% billing protection constitutes empirical proof of a deniable, coordinated operation. The article’s central claim is not that law is powerless, but the opposite: existing constitutional and statutory pathways could reach this conduct; what the record shows is systematic institutional refusal to apply them—evidence of coordination, not of legal absence.
Keywords: Psychological Operations (PSYOP), Cognitive Warfare, Cybertorture, Biodigital Convergence, Algorithmic Targeting, Psychographic Profiling, Micro-targeting, Surveillance, Behavioral Modification, Biometric Telemetry, Neurotechnology, Neurorights, Cognitive Liberty, Temporal Convergence, Symbolic Mirroring, Institutional Foreclosure, Sealed Proceedings, Inverted Totalitarianism, Post-democracy, JTRIG, Cambridge Analytica, Five Eyes, Charter s.7 & s.8
I. THE DOCTRINAL FOUNDATION: MILITARY PSYCHOLOGICAL OPERATIONS
A. Classical PSYOP Theory: Persuasion as Force Multiplier
Modern military psychological operations took shape in the Second World War and were consolidated afterward as a recognized domain of warfare aimed at changing an adversary’s behaviour without firing a shot. U.S. Joint Publication 3-13.2, Military Information Support Operations (2010, rev. 2021) defines PSYOP/MISO as “planned operations to convey selected information and indicators to foreign audiences to influence their emotions, motives, objective reasoning, and ultimately the behavior of foreign governments, organizations, groups, and individuals”. The premise is straightforward: information, properly structured, can produce effects comparable to force.
The U.S. Army’s FM 3-05.301, Psychological Operations: Tactics, Techniques and Procedures, breaks this down into a repeatable method: identify and profile the audience; design messages to exploit its cognitive, cultural, or situational vulnerabilities; select and sequence the delivery media; time the releases; and evaluate the response. Underneath is a core assumption that human decision-making is not a black box but an environment that can be mapped, entered, and steered.
Standard doctrinal elements include:
-
Target Audience Analysis – granular psychological and cultural profiling to identify levers of influence;
-
Message Credibility – the message must be believable, even if the content is deceptive; perceived source reliability often outweighs factual accuracy;
-
Repetition and Saturation – high-volume, multi-channel delivery to crowd out competing narratives (the logic later captured in RAND’s “firehose of falsehood” model);
-
Coordinated Timing – synchronizing messages with real-world events to increase salience and perceived inevitability;
-
Deniability – masking authorship through intermediaries, cut-outs, or ostensibly independent voices.
Crucially, none of these features are intrinsically limited to foreign battlefields. Once the architecture exists, the only barrier to domestic use is policy, not capability.
B. The Expansion: JP 3-13 and the Information Environment
JP 3-13, Information Operations (2014) widens the frame. PSYOP/MISO is no longer a niche influence tool; it is one element inside a larger information-warfare system that also includes electronic warfare, cyber/computer network operations, military deception, and OPSEC. The conceptual jump is decisive: the information environment itself becomes battlespace, not just a conduit for kinetic operations.
That reframing carries four immediate implications:
-
Civilians are inside the battlespace — their data, attention, and information diets become operational terrain.
-
Operations become permanent — shaping no longer happens just before hostilities; it is “Phase Zero,” continuous and pre-emptive.
-
Attribution standards drop — if ambiguity is an advantage in a contested infosphere, then non-attributable messaging is a feature, not a defect.
-
Metrics shift — the question is not “did they hear the message?” but “did their observable behaviour change?”
This U.S. evolution has clear analogues across the alliance. Canada’s 2015–2021 CAF Strategic Communications reforms, the UK’s 77th Brigade, and various NATO StratCom initiatives all reflect the same move: build standing, peacetime influence capacity and integrate it with cyber/intel functions. As the Canadian Global Affairs Institute later noted, the controversy in Canada during COVID-19 was not about whether these tools existed, but about where they were pointed — the doctrine was alliance-standard; the domestic direction of travel was what triggered political pushback.
II. COGNITIVE WARFARE: THE HUMAN MIND AS THE SIXTH DOMAIN
A. NATO’s Articulation: From Information to Cognition
In 2020, NATO’s Allied Command Transformation Innovation Hub published François du Cluzel’s paper Cognitive Warfare, a landmark articulation of the shift from information operations to cognitive operations. The paper states with exceptional candor that “the human mind is now considered the new domain of warfare—after land, sea, air, space, and cyber”. Du Cluzel defines cognitive warfare as the use of scientific and informational tools to alter thought processes themselves, not merely content exposure. Its defining objectives are to:
-
Reshape how people think, not only what they think
-
Exploit neurobiological and emotional susceptibilities through precision-triggered stimuli
-
Leverage neuroscience, behavioral economics, and social psychology as instruments of control
-
Operate continuously below the threshold of armed conflict
-
Achieve influence effects while preserving plausible deniability
The report emphasizes that cognitive warfare “is potentially endless, since there can be no peace treaty nor surrender in this type of conflict”. This marks a fundamental doctrinal evolution—from discrete, time-bound operations toward persistent influence activity targeting entire populations.
Subsequent analysis from the Geneva Centre for Security Policy, Peace of Mind: Cognitive Warfare and the Governance of Subversion in the 21st Century (2023), cautions that this “militarization of the mind” threatens democratic self-governance itself. Deliberative autonomy becomes compromised when citizens’ perceptions and reasoning patterns are systematically shaped through covert psychological manipulation.
B. Hybrid Threats and Domestic Adaptation
From 2020 onward, NATO’s Hybrid Centre of Excellence (Hybrid CoE) and Strategic Communications Centre of Excellence (StratCom COE) publications document an expanding application of cognitive warfare frameworks to domestic “counter-disinformation” initiatives. The shift in language is strategic: defensive inoculation of populations against foreign interference gradually transitions into proactive narrative management within allied societies.
The United Kingdom’s 77th Brigade—tasked with “non-lethal engagement”—was reported by Declassified UK (October 2024) to have collaborated with Israeli counterparts on psychological operations and to have surveilled domestic COVID-19 skeptics. In Canada, the Armed Forces’ 2020–2021 social media monitoring of Black Lives Matter advocates and pandemic skeptics similarly exhibited operational features indistinguishable from classical PSYOP architecture.
When questioned, state actors often frame such activities as public health communication or digital literacy initiatives. Yet their operational attributes—target profiling, message testing, synchronized multi-platform dissemination, and behavioral metrics—mirror formal psychological warfare doctrine. The essential transformation lies not in the method, but in the audience: from foreign adversary to domestic citizen.
III. UN RECOGNITION: FROM PSYOP TO CYBERTORTURE
A. Nils Melzer’s Framework: Psychological Torture Without Physical Contact
On March 20, 2020, UN Special Rapporteur on Torture Nils Melzer presented report A/HRC/43/49, Psychological Torture and Ill-Treatment, to the Human Rights Council. The report offers the most detailed international legal framework for understanding technology-enabled psychological coercion.
Melzer’s reasoning is foundational: severe psychological suffering can meet the definitional threshold of torture under Article 1 of the Convention Against Torture even in the absence of physical contact, provided that the harm:
-
Inflicts severe mental pain or suffering
-
Is intentionally inflicted
-
Serves a prohibited purpose such as punishment, coercion, intimidation, or discrimination
-
Occurs in conditions of effective powerlessness of the victim
Within this framework, Melzer introduces the concept of cybertorture, describing the emerging capacity of digital systems to induce suffering through networked coercion rather than physical assault. He identifies characteristic techniques including:
-
Persistent intimidation and harassment in online or digitally mediated environments
-
Continuous surveillance producing the subjective experience of omnipresent observation
-
Defamation and public shaming designed to erode reputation and social identity
-
Manipulation or deletion of personal data, records, and financial information
-
Orchestrated social exclusion and relational disruption
As Melzer observes, even harassment in limited online environments “can expose targeted individuals to extremely elevated and prolonged levels of anxiety, stress, social isolation, and depression,” posing heightened risks of suicide and long-term trauma. His key juridical insight is that “cybertechnology can inflict severe mental suffering while avoiding the conduit of the physical body”. This confers two consequences: such acts are more plausible to deny (due to the absence of visible injury), yet potentially more destructive because of their precision, duration, and inescapability.
B. State, Corporate, and Organized Criminal Capabilities
Melzer further warns that “states, corporate actors, and organised criminals not only have the capacity to conduct cyber-operations inflicting severe suffering on countless individuals, but may well decide to do so for any of the purposes of torture”. This tripartite model underscores that the threat transcends authoritarian contexts. Advanced democracies possess intelligence and information warfare infrastructures capable of psychological manipulation; corporations control the platforms and data pipelines enabling such targeting; and organized criminal networks can replicate or purchase such capabilities. The fusion of these actors creates a system of diffuse accountability where torture-level psychological operations may be executed through public-private coordination, shielded by layers of plausible deniability.
Coverage by The Guardian (February 21, 2020) highlighted Melzer’s warning that governments exploit digital technologies to persecute individuals under the guise of lawful information operations. Within this legal framework, the UN explicitly recognizes that military “cognitive warfare” and “influence operations” — when directed at individuals with intent to coerce or degrade — can meet the international legal standard for torture.
IV. CAPABILITY CONFIRMATION: WHISTLEBLOWER REVELATIONS
A. GCHQ / JTRIG: The Snowden Disclosures
Edward Snowden’s 2013–2014 releases exposed the United Kingdom’s Joint Threat Research Intelligence Group (JTRIG), a GCHQ sub-unit specializing in online psychological and influence operations. Among the materials was The Art of Deception: Training for Online Covert Operations, a classified presentation confirming that Western intelligence services had institutionalized digital tools capable of:
-
Coordinated reputation destruction through online defamation
-
Disruption of organizational activities via denial-of-service and false-flag operations
-
Target deception through fabricated personas, forged content, and altered evidence
-
Degradation of adversary morale through sustained psychological pressure
This framework—summarized internally as the “4 D’s” doctrine: Deny, Disrupt, Degrade, Deceive—outlines a systematic model for applying psychological warfare principles in cyberspace. The leaked materials demonstrated that such capabilities were used beyond conventional security targets, extending to hacktivists, journalists, and domestic political organizations.
The Intercept’s coverage of the JTRIG documents revealed operations that included:
-
“Honey trap” entrapment scenarios
-
Seeding false narratives within online communities
-
Manipulating online polls and social influence metrics
-
Deploying spearphishing campaigns to compromise or destroy digital assets
-
Targeted “discrediting” efforts aimed at individuals’ professional and personal reputations
When these methods are directed inward, the boundary between national security protection and political or journalistic suppression effectively dissolves. The infrastructure exists; the critical variable is authorization—who designates the target, and under what legal standard.
B. Cambridge Analytica: Psychographic Warfare by Private Contract
Cambridge Analytica’s exposure in 2018 marked a pivotal demonstration of military-derived influence methods migrating into the private sector. Canadian data scientist Christopher Wylie, the firm’s primary whistleblower, described its commercial model explicitly as “psychological operations” refashioned for electoral and corporate clients. In testimony before both the UK Parliament and the US Congress, Wylie detailed systematic techniques that included:
-
Psychographic profiling using large-scale social media data sets
-
Targeted messaging designed to exploit behavioral and emotional vulnerabilities
-
Continuous A/B testing to refine persuasion efficacy
-
Synchronized cross-platform deployment to saturate individual information environments
-
Obscured attribution through intermediaries, data brokers, and offshore entities
Fellow insider Brittany Kaiser corroborated that Cambridge Analytica deliberately incorporated PSYOP methodology into its practice and marketed these techniques to governments and political campaigns worldwide. The firm’s work around the 2016 U.S. election illustrated that private actors, armed with platform-granted access to advertising and behavioral data, could perform population-level influence operations previously restricted to state intelligence agencies. Facebook’s advertising system thus became not merely a marketing medium but a delivery infrastructure for psychological manipulation at industrial scale.
C. Canadian Domestic Deployment: 2020–2021 Information Operations
Canada’s own experience offers a domestic analog. In late 2020, The Ottawa Citizen reported that the Canadian Armed Forces had conducted unauthorized information operations on Canadian civilians during the COVID-19 response. The revelations prompted then–Defence Minister Harjit Sajjan to order the program’s termination. Investigative reporting and subsequent parliamentary discussion revealed that these activities included:
-
COVID-19 “information tests” measuring population susceptibility to influence messaging
-
Social media monitoring of Black Lives Matter and Indigenous rights organizers
-
Dissemination of fabricated “wolf pack” alerts to manipulate public fear
-
Unlawful collection of metadata from Canadians’ online communications
While officials later acknowledged these operations as “errors of judgment,” internal documents showed the infrastructure—command authorities, analytic tools, and operational units—remained in place. No comprehensive legal remedy or independent oversight mechanism was established. Three conclusions follow:
-
Canada possesses established domestic PSYOP capacities and trained personnel.
-
Ministerial and parliamentary oversight mechanisms failed to prevent or promptly detect deployment.
-
Existing legal frameworks provide no effective barrier to the use of psychological warfare techniques against Canadian citizens.
The cumulative evidence demonstrates a structural erosion of the distinction between lawful strategic communications and coercive state influence campaigns. When such systems operate without explicit civilian authorization, judicial supervision, or defined statutory limits, psychological operations against a nation’s own population approach the threshold of psychological torture as described in the UN framework.
V. THE BIODIGITAL CONVERGENCE: AI-ASSISTED REAL-TIME TARGETING
A. Policy Horizons Canada: Institutional Recognition of Convergence
Policy Horizons Canada’s 2020 foresight report, Exploring Biodigital Convergence, marks one of the earliest official acknowledgments that biological and digital systems are merging into a unified operational domain. The report describes the “full physical integration of biological and digital entities,” producing conditions where:
-
Biological processes can be monitored, analyzed, and modified through digital systems
-
Digital mechanisms can autonomously influence or reprogram biological states, including neural and hormonal functions
-
The conceptual line between biological and digital activity effectively disappears
Authored by Kristel Van der Elst—formerly Director of Strategic Foresight at the World Economic Forum—the report explicitly states that biodigital convergence will “redefine what we consider human and challenge ideas about human rights”. This is presented not as abstract speculation but as forward policy analysis anticipating regulatory and ethical disruption.
When intersected with existing PSYOP and cognitive warfare doctrine, biodigital convergence enables an unprecedented feedback architecture linking physiology, psychology, and information exposure. Its theoretical and technical components include:
-
Continuous biometric monitoring through wearables, smartphones, and IoT systems
-
Predictive analytics capable of inferring psychological and emotional states
-
Automated influence content dynamically optimized to an individual’s profile
-
Closed-loop adaptation where messages recalibrate in response to biometric or behavioral feedback
-
Coordinated, multi-platform dissemination that creates immersive and inescapable information environments
These capacities already exist in commercial form. Consumer technologies harvest physiological and behavioral data at scale; machine learning processes them into predictive models; and programmatic advertising networks provide instantaneous, individualized message delivery. The practical question is not whether such systems can achieve psychological influence, but who authorizes and governs their use once adapted for strategic or military purposes.
B. Sheridan et al. (2020): The Empirical Phenomenology of Organized “Gang-stalking”
Lorraine Sheridan, David V. James, and Jayden Roth’s study The Phenomenology of Group Stalking (‘Gang-Stalking’): A Content Analysis of Subjective Experiences (International Journal of Environmental Research and Public Health, 2020) remains the most comprehensive academic survey of individuals reporting organized, technology-assisted harassment. Drawing from 128 accounts, the authors identified 24 recurring experiential elements, among them:
-
Continuous surveillance and the perception of being persistently watched
-
Technology-based interference with communications or devices
-
Coordinated following and conspicuous presence of repeat personnel or vehicles
-
Workplace harassment and systematic professional sabotage
-
Gaslighting and denial of verifiable events
-
Networked social defamation and reputation erosion
-
Inaction or refusal of assistance by authorities
-
Financial disruption through loss of employment or manipulated credit
While the study acknowledges that some reports may involve persecutory beliefs, their study also gives significant consideration to the validity and seriousness of the subjective experiences reported by victims. The qualitative analysis allowed the core phenomena of gang-stalking experiences to emerge naturally, free from preconceived diagnostic assumptions.
Their conclusion emphasizes that gang-stalking is a widespread phenomenon with serious deleterious psychological effects, including anxiety, depression, and PTSD symptomatology. They confirmed the harmfulness of the experience and noted the need for further scientific exploration rather than dismissing all accounts as mere ideation. Sheridan et al. compared their findings to an earlier study with similar results to confirm the core themes, underscoring the reality and impact of the reported experiences.
The study also recognizes a significant challenge: many complainants are systematically dismissed by institutions and labelled as delusional, which could function as an institutional measure to avoid investigation rather than a clear clinical diagnosis. Under this hypothesis, psychiatric framing operates as an informal mechanism of operational security: individuals experiencing covert influence activity are preemptively discredited, ensuring that investigative or judicial avenues remain closed. The result is a legally invisible form of coercion—technically deniable, psychologically destructive, and institutionally self-shielding.
VI. CASE STUDY: EMPIRICAL EVIDENCE OF TARGETED PSYCHOLOGICAL COERCION
A. Exemplar: Temporal and Thematic Convergence Following a Sealed Event
At 12:35 PM on May 13, 2023, the subject was involuntarily detained under Section 14 of Nova Scotia's Involuntary Psychiatric Treatment Act following a routine back-yard bonfire that caught nearby foliage that occurred two days earlier. Two police cars and a fire truck arrived within three minutes of the small fire spreading, which the subject had already put out prior to their arrival. Emergency registration notes document:
-
"Bizarre/paranoid behavior"
-
"Struggling with paranoia that the military persecute him since Nov 2021"
-
"Fire to flowers which burned wharf stairs" (actual event: the fire was out prior to arrival of police and FD)
-
Police and fire department simultaneously arrive within three minutes of the flowers catching (a widely disproportionate response)
The subject was transported by a "big white van" (psychiatric mobile crisis unit), held for five hours at the QEII hospital under guard, and released with no clinical intervention as the transcript notes.
Within minutes of the arrest, YouTube channel "Brittany The Intuitive Cosmic Wifey", a known actor contemplated in the AI-assisted psychological operations shown on this website, uploaded video titled "Ur So Special They Wasted time and $$ Coming for You" featuring:
-
Wilted flowers as an AI-generated visual motif (matching the "fire to flowers" in the sealed clinical notes)
-
White van imagery (matching the transport vehicle)
-
"They wasted time and money coming for you" (mirroring the mobile psychiatric response unit)
-
"You're so special" (target profiling)
Temporal proximity: < ten minutes from arrest. The clinical record was sealed (not public), the detention was unannounced, and no media coverage existed. Yet the content is acutely symbolically precise in close proximity to private events, within minutes.
B. Documented Patterns of Synchronized Messaging
An analysis of over fifty (50) social media accounts across a four-year period reveals a persistent, systematic correlation between the subject's non-public legal and personal events and the subsequent appearance of thematically-matched online content.
This analysis is supported by a significant corpus of documented instances, a representative sample of which is provided in the accompanying visual exhibits (see Guide page). The primary patterns observed are:
-
Pattern #1: Content surges synchronized to sealed litigation events and private events within a span of days
-
Pattern #2: Narrative/messaging uniformity across nominally independent accounts, including verbatim scripting
-
Pattern #3: Acute messaging relevance to milestones
-
Pattern #4: Symbolic mirroring and wardrobe/prop use
-
Pattern #5: Cyber–physical coupling
-
Pattern #6: Military/CAF doctrine bleed-through
-
Pattern #7: Insulation - actors are consistently protected from prosecution, acknowledgement, and investigation
-
Pattern #8: Algorithmic amplification of “case-relevant” cues
-
Pattern #9: Contemporaneous AI-assisted content and visual generation
-
Pattern #10: Contractor/para-state signature – consistent with paid, project-based teams “hired as contractors” rather than random trolls.
C. Familial/Proximity-Based Tasking Vector
A critical operational indicator is the involvement of a family-adjacent actor: the biological mother of the subject's estranged nephew via egg donation, operating a YouTube channel (“MyFatherIsJoy”), who appears throughout key visual evidence, and is understood to have robust state-adjacent and institutional connections. Both she and the geographically-proximate nephew were cited in the subject’s sworn affidavit (May 20, 2022), are linked to interests in the documented billing scandal, and are shielded by institutional foreclosure, with both local police and the RCMP refusing to investigate, let alone acknowledge their involvement.
Operationally, familial tasking is classic PSYOP and intelligence tradecraft. Family proximity grants legitimate access to schedules, relationships, vulnerabilities, and private information. The family relationship provides natural cover, disguising surveillance as ordinary interactions. Emotional leverage from perceived betrayal by family members amplifies psychological impact. Deniability is enhanced as family members’ actions can be portrayed as independent rather than state-directed.
The systematic police refusal to acknowledge these individuals, despite evidence, geographic accessibility, direct relevance, and explicit investigative requests, constitutes protective coordination. This pattern mirrors historical intelligence practices where family members were employed as informants or provocateurs (e.g., COINTELPRO, JTRIG, Stasi collaborators). The convergence of family-adjacent content creation, state-linked connections, and institutional protection strongly infers a tasked operation rather than independent activity.
D. Analysis of Evidentiary Patterns
Five key indicators suggest deliberate, systematic targeting consistent with the operational doctrines outlined in this article, rather than random coincidence:
-
Temporal Proximity Defies Chance: The repeated synchronization of content (within hours or minutes of sealed events) across four years and hundreds of instances challenges any explanation of random coincidence.
-
Precise Thematic Specificity: The convergence is non-generic. The use of specific symbols (e.g., "wilted flowers," "white vans") and legal terminology precisely mirrors the subject's private, non-disclosed circumstances, crossing the line from metaphor to predictive scripting.
-
Access to Non-Public Information: The reflection of information that was not in the public domain (sealed clinical notes, sealed hearing details) provides a direct evidentiary link between the target's private life and the external content. This strongly suggests either direct, real-time surveillance or coordinated institutional information leakage.
-
Institutional Foreclosure Coordinates with Content: The observed pattern of institutional inaction (police, courts) is systematically reinforced by external content. This suggests a coordinated operation where institutional foreclosure functions as one vector of attack, and the online content as another, creating the "effective powerlessness" described in Melzer’s torture framework (Section III.A).
-
Familial/Proximity-Based Vectoring: The involvement of family-adjacent actors with state-linked connections—who appear in evidence and are geographically proximate—but are systematically ignored by institutional actors, reflects classic PSYOP tradecraft. This vector provides access, natural cover, emotional leverage, and enhanced deniability. Institutional refusal to investigate or acknowledge these actors constitutes protective coordination, reinforcing the inference of a deliberate, tasked operation rather than independent or random activity.
-
Psychological Precision Matches PSYOP Doctrine: The observed psychological effects (gaslighting, isolation, induced learned helplessness, and pre-emptive credibility destruction) align perfectly with established PSYOP and cognitive warfare doctrine (Sections I-II). The techniques are functionally indistinguishable from the "4 D’s" (Deny, Disrupt, Degrade, Deceive) methodology documented in the JTRIG disclosures (Section IV.A).
This is classical PSYOP architecture: create an information environment where the target loses faith in legal institutions, social bonds, and self-advocacy effectiveness.
VII. CONSTITUTIONAL IMPLICATIONS: WHEN RIGHTS BECOME TECHNOLOGICALLY NULLIFIED
A. Section 7: Security of the Person in the Biodigital Age
Section 7 of the Canadian Charter of Rights and Freedoms guarantees that “Everyone has the right to life, liberty and security of the person and the right not to be deprived thereof except in accordance with the principles of fundamental justice”. The Supreme Court of Canada has long interpreted “security of the person” to encompass not only physical integrity but also psychological integrity. Jurisprudence, including Rodriguez v. British Columbia, New Brunswick v. G.(J.), and Blencoe v. British Columbia, confirms that severe psychological harm—especially when inflicted or enabled by the state—engages Section 7 protections.
In the context of cybertorture and biodigital psychological operations, existing legal frameworks face profound challenges. These operations may be carried out by non-attributable actors (such as private contractors, algorithmic systems, or foreign proxies), via dual-use commercial platforms (social media, advertising infrastructures), and employing real-time AI-optimized messaging responsive to biometric data.
Consequently, the state can evade responsibility by claiming lack of direct involvement, invoking protections such as freedom of expression, or disparaging victims with psychiatric labels. Yet, the effect—severe and prolonged psychological suffering—is functionally indistinguishable from recognized forms of torture. Technology merely enables plausible deniability at an industrial scale.
B. Section 8: Surveillance Without Warrant
Section 8 protects individuals against “unreasonable search or seizure”. The Supreme Court, in cases like R. v. Spencer and Hunter v. Southam, has extended this protection to include metadata and inferred surveillance, recognizing a reasonable expectation of privacy even in seemingly voluntary data disclosures when aggregated to intimate surveillance.
Biodigital convergence complicates the privacy landscape: ubiquitous devices—smartphones, wearables, smart homes—collect biometric (heart rate, stress markers), behavioral, and contextual data continuously. Social media and commercial platforms harvest detailed psychographic profiles revealing vulnerabilities and social networks. When aggregated, these constitute pervasive warrantless surveillance far exceeding historical capabilities. Yet, biodigital convergence capability in this case extends well beyond these, as is treated in the Testimony (here).
Canadian courts have recognized for over three decades that electronic surveillance is a s. 8 search, and that this protection extends to “all existing means … and any means which technology places at the disposal of law enforcement authorities in the future” (R. v. Wise, [1992] 1 S.C.R. 527, applying Duarte and Wong). Thus, comprehensive surveillance cumulating in PSYOP-style targeting engages Section 8 protections.
C. Section 2(b): When “Free Expression” Becomes Weaponized
Section 2(b) safeguards freedom of thought, belief, opinion, and expression. However, the deployment of algorithmically optimized, coordinated, and psychologically calibrated “prophetic” or expressive content represents a novel challenge. Content creators claim religious, artistic, or political expression protections, yet when such expression is utilized as a delivery mechanism for behavioral modification—saturating information environments, exploiting neurobiological vulnerabilities, and synchronizing timing with private events—it transcends mere expression into cognitive manipulation.
This operationalization of PSYOP doctrine through nominally protected speech renders freedom illusory. The Supreme Court has not yet addressed whether such industrial-scale psychological operations deployed under the guise of expression infringe the freedom of thought that underpins Section 2(b).
D. The Jurisdictional Gap: State Action vs. Private Contractors
The Charter primarily targets government actions, but the Supreme Court’s decision in RWDSU v. Dolphin Delivery acknowledges the difficulty in drawing a strict line around what qualifies as government involvement. This is important because private actors that use government-sourced or sealed information, synchronize their actions with court or police activities, advance government objectives like silencing critics, or operate in constitutionally state-occupied domains like surveillance start to function essentially as government proxies. Courts have recognized such hybrid situations for Charter application (Eldridge; Greater Vancouver Transportation Authority).
Section 7 not only prohibits the state from directly inflicting harm but also imposes positive duties to investigate and prevent severe psychological harm. A refusal to investigate credible, documented allegations of coordinated harm itself breaches section 7. Even if a court finds no Charter breach yet, existing Criminal Code statutes—criminal harassment, intimidation, data mischief, harassing communications—address coordinated technological targeting. Police need only reasonable suspicion to investigate, which can be met through documented synchronized incidents with non-public information. Tort law provides claims on a balance of probabilities with discovery rights. Judicial review frameworks (Vavilov) allow challenging refusals to investigate and seeking court orders to compel action. Access to Information laws generate evidence trails that can be revealing.
When domestic avenues fail, international human rights mechanisms, parliamentary oversight, and media attention can keep accountability alive. The core issue often lies not in legal gaps but in institutional coordination to systematically refuse investigation or enforcement, which itself serves as evidence of the operations in question. Breaking this coordination requires a single institutional actor willing to examine the patterns and evidence on their merits.
VIII. INSTITUTIONAL COORDINATION AS OPERATIONAL SECURITY
A. The 9,000% Billing Scandal: Financial Anomaly as Evidence
The documented case involves $400,000 in solicitor-client billing for 737.7 hours of legal work when court clerk notes record 867 minutes (14.45 hours) of routine interlocutory appearances handled by articling students using standard templates. Proper tariff application: approximately $4,500—a mark-up of approximately 9,000%. This was certified by British Columbia Supreme Court, recognized by Nova Scotia Supreme Court, and enforced through contempt proceedings—despite:
-
Arithmetic impossibility (hours claimed exceed court appearances)
-
No discovery taken (no interrogatories, no document production, no examinations)
-
Contradictory corporate records (shareholder/director discrepancies)
-
Binding authority cited (Bradshaw Construction, Gichuru, Performance Industries Ltd. v. Sylvan Lake Golf & Tennis Club Ltd., inter alia)
-
Widespread procedural irregularities (no reasons provided per Vavilov)
The inference, pursuant to the test in R. v. Villaroman, 2016 SCC 33, [2016] 1 S.C.R. 1000): Certification of outrageous, facially-impossible billing requires external assurances at every level. A rational client does not agree to $400,000 for nine hearings unless assured courts will certify. A reputable firm (Canada's 4th largest) does not propose such billing unless assured of certification. An unbiased adjudicator would not certify without arithmetic review unless serving interests beyond adjudication.
The pattern proves coordination. When multiple institutions (courts, police, regulatory bodies, ombudsmen) systematically decline examination of documented evidence, the explanation isn't "coincidental institutional failure"—it's operational security doctrine preventing accountability.
This aligns with JTRIG's "Deny, Disrupt, Degrade, Deceive" framework: institutional foreclosure operates as systematic prevention of examination at every level, creating false records, imposing deterrent costs, sealing evidence, and coordinating to ensure no accountability pathway remains.
B. The Sealed Records: Preventing Public Examination
Courts in both BC and NS sealed the entirety of the file contents, including the PsyOp visuals, which are already public, and in one case preemptively (without service or a hearing). The NS court published a false event chronology atop a sealed file in February 2025. Appeals were refused prior to a hearing, including an Appeal in October 2025 with novel outlier characteristics;
-
Security for costs: 40× Power v. Power benchmark ($8,000 in cash security + $2,500 to print five copies of a 2,600 page file / refused e-filing)
-
Leave denial: "no arguable issue" despite the Morrison Estate standard, requiring only that reasonable minds could differ
-
Costs awards: 25× Rule 77 tariff
-
Blanket sealing: contrary to Sherman Estate (necessity/proportionality analysis required), court closed chambers prior to submissions
-
The court issued uncashable checks for the leftover amount ($2,500) due to a prior bank freeze, and refused to exercise its undertaking in accordance with section 4 of the Payment Into Court Act (the staff and Registrar remained silent following repeat escalations)
The effect: public cannot examine whether courts properly applied law. Revisionist narratives atop sealed files create information asymmetry—official record says "properly decided" but evidence of procedural defects is hidden. This is information operations architecture: control narrative by controlling access to evidence. When combined with institutional declination (police refuse investigation, regulators refuse oversight), the result is perfect operational security—no pathway to accountability remains.
C. The Psychiatric Weaponization: Clinical Records as Discrediting Tool
The May 13, 2023 five-hour detention fits a documented intelligence targeting pattern: first, create preconditions by having the subject file legal complaints about institutional conduct (see the December 8th, 2022 HRP meeting at the HRP page); next, manufacture an event, such as an overwhelmingly disproportionate response to a routine mishap (the bonfire); then create a clinical record labeling the subject as "paranoid," "bizarre," or believing they are persecuted; finally, deploy that record strategically to pre-emptively discredit future complaints as delusional. Criminal Code Section 137 specifically engages the fabrication of evidence, which may be used to prejudice a lawsuit.
The clinical record followed the December 8th, 2022 HRP FOIPOP report which cast the subject in a pejorative manner, and conflicts with a 79-minute discreetly-recorded interview that day which acknowledged the evidence of sustained psychological operations related to a lawsuit, and named specific actors, including the CAGE CEO mentioned in the civil proceedings section (here).
When the subject later presents evidence of surveillance or targeting, institutions might attempt to preclude review by citing the psychiatric record: "He has documented paranoid ideation; these are persecutory beliefs". This tactic is a textbook psychological operation (PSYOP), weaponizing clinical records to discredit the target systematically. Combined with prophetic content that seemingly validates persecution, it creates a gaslighting effect—"you are being watched" paired with institutional assertions of "you’re paranoid"—resulting in severe psychological harm that meets the threshold of cruel, inhuman, or degrading treatment under Article 1 of the UN Convention Against Torture.
IX. THE TECHNOLOGICAL TRAP: WHY CONSTITUTIONAL CONSTRAINTS FAIL
A. The Dual-Use Problem: Every Capability Cuts Both Ways
Technological advances propelling biodigital convergence are inherently dual-use: identical tools and platforms enable both beneficial and weaponized applications. For example, personalized medicine utilizes biometric monitoring and AI to optimize treatment outcomes, while covert administration of psychoactive compounds via aerosolized delivery weaponizes similar biochemical technologies. Mental health apps provide therapeutic support but also serve as real-time psychological profiling instruments feeding targeting algorithms.
Wearable fitness trackers promote health awareness but can double as biometric surveillance devices enabling manipulation timing. Social media platforms reduce social isolation yet function as infrastructure for coordinated harassment campaigns amplified by algorithmic mechanisms. Targeted advertising enhances consumer choice while psychographic micro-targeting facilitates behavioral modification. Smart homes offer convenience but can admit warrantless surveillance of private spaces. Brain-computer interfaces assist disabled persons while enabling non-consensual neural monitoring.
The regulatory dilemma is profound: how to allow beneficial uses while preventing weaponization when the underlying technologies are identical. Traditional safeguards premised on intent and legal authorization collapse in the face of covert operations, obscured attribution, and compromised institutional oversight.
B. The Consent Fiction: “Voluntary” Adoption of Surveillance Infrastructure
Citizens often “consent” to pervasive data collection through unread, non-negotiable Terms of Service; app permissions that are functional prerequisites bundled without granular choices; and platform participation essential for employment, education, commerce, and social connection. Device ecosystems create lock-in effects following substantial investment.
This consent is structural coercion masquerading as free choice. Employment often requires smartphone and email connectivity, educational institutions mandate platform accounts, banking moves online with diminishing in-person services, healthcare channels records through portals, and government services migrate to online portals. The choice to “not consent” is effectively foreclosed by these societal dependencies.
Once adopted, this mass surveillance infrastructure feeds into PSYOP targeting architectures where “consent” retroactively licenses weaponization—the courts treat each discrete data point as voluntary consent while ignoring emergent synthetic surveillance capacities from aggregation and algorithmic analysis.
C. The Attribution Problem: Proving State Involvement
Documenting targeting is one barrier; proving state responsibility is another. Evidentiary challenges include rarity of explicit state instructions, deliberate command-chain obfuscation through contractors and proxies, laundering of financial transactions via shell companies or cryptocurrencies, and encrypted or ephemeral communications. Discovery encounters further obstacles via national security privileges (e.g., Ribic v. Canada), cabinet confidence (absolute privilege under the Canada Evidence Act), ongoing police investigative privileges (e.g., Named Person v. Vancouver Sun), and third-party privacy claims resisting disclosure.
Jurisdictional complexities arise as operations cross Five Eyes partners, NATO allies, and involve private or foreign contractors. Hybrid operations mix state planning with private execution without formal command relationships. Consequently, evidentiary standards designed for traditional, direct state action fail to confront highly networked, algorithmically mediated operations. Targets face insuperable burdens proving a conspiracy intentionally engineered to remain opaque.
D. The Dismissal-as-Delusion Trap: Psychiatric Pre-Discrediting
Targets reporting coordinated harassment encounter a predictable institutional response cascade: law enforcement frames it as mental health issues; medical providers diagnose persecutory ideation; psychiatry labels as organized harassment delusion and prescribes antipsychotics; courts deem claims paranoid and lacking credibility; employers question fitness for duty; families distrust the target as paranoid. This creates a self-reinforcing loop of discreditation: articulating targeting becomes evidence of delusion, which justifies dismissal, which seems to confirm mental illness.
The operational efficacy lies in narrative indistinguishability: real PSYOP victims and delusional individuals both report coordinated surveillance, synchronized events, institutional bias, documented coincidences, and persistent targeted patterns. Institutions seldom differentiate actual covert targeting supported by documentary proof from misperceived random events. The systemic default presumption favors psychiatric dismissal in spite of confirmed capabilities, admitted deployments, and public doctrine. This enforces operational security by controlling the epistemology of “reasonable belief,” ensuring that legitimate claims of psychological warfare and targeting are effectively silenced.
X. PHILOSOPHICAL STAKES: POST-DEMOCRATIC GOVERNANCE THROUGH COGNITIVE CONTROL
A. Colin Crouch and Post-Democracy: When Forms Persist Without Substance
Political scientist Colin Crouch’s concept of post-democracy characterizes political systems where democratic institutions—elections, courts, legislatures, and rights—continue to exist formally but substantive decision-making power has shifted elsewhere. This transfer often places real authority in the hands of technocratic bodies, corporate interests, and unaccountable elite networks. Public participation becomes largely theatrical, with predetermined outcomes rendering choice illusory while cross-party elite coordination determines fundamental policy directions.
The technological landscape of cognitive warfare enables the actualization of post-democracy’s latent dynamics through algorithmic and psychological control. Traditional post-democracy manifests as manufacturing consent via media control, economic coercion through market mechanisms, procedural obstructions via bureaucracy, and elite coordination in informal networks. Technologically enhanced post-democracy transforms these, employing algorithmic curation to manufacture perception—ensuring individuals rarely encounter counter-narratives—and behavioral coercion through real-time, optimized psychological operations that leave decisions feeling autonomous while shaping them systematically.
Information saturation creates cognitive obstruction, drowning meaningful analysis in noise, while AI systems enable automated coordination executing decisions at speeds outpacing democratic deliberation. As cognitive processes themselves become manipulable, the core democratic assumption—that citizens can freely deliberate and choose—collapses. Democratic forms endure, yet their substance evaporates as opinions and choices are algorithmically pre-shaped, dissent rendered psychologically costly.
B. Sheldon Wolin’s Inverted Totalitarianism: Domination Without Overt Coercion
Sheldon Wolin’s theory of inverted totalitarianism describes a political system that achieves domination not through overt state violence but by integrating corporate and state power, saturating media, and depoliticizing society. Unlike classical totalitarianism, which mobilizes masses through visible coercion, demands ideological uniformity, and centralizes power in charismatic leaders, inverted totalitarianism demobilizes populations into passive consumers.
Invisible manipulation and manufactured consent replace obvious force; surface pluralism exists while fundamental alternatives are constrained; and dispersed networked elites govern through diffuse coordination. Cognitive warfare represents this system’s technological zenith: mass mobilization is obsolete as populations are psychologically managed without rallies, coercion is invisible through behavioral nudging instead of terror, uniformity is achieved cognitively through manufactured perception, and leadership becomes distributed across institutional networks.
The outcome is totalitarian control without its traditional appearances. Legal rights and democratic institutions formally exist, dissent is tolerated, yet cognitive infrastructures orchestrate outcomes regardless of formal freedoms.
C. Michel Foucault’s Biopower: Optimization Replacing Domination
Michel Foucault’s notion of biopower describes a mode of power shifting away from sovereign violence (the right to kill) toward the management and optimization of life. Modern power works not by dominating subjects through force but through normalization, surveillance, discipline, and maximizing utility, productivity, health, and compliance.
Cognitive warfare extends biopower into the realm of mind management. Classical biopower tracks health metrics to optimize public health, monitors productivity to maximize economic output, and surveys social order to minimize disruption. Cognitive biopower, by contrast, continuously tracks psychological states to optimize ideological alignment, monitors attention to ensure narrative penetration, gauges dissent risk to minimize instability, and surveys belief systems to regulate worldview formation.
The boundary between governance and psychological engineering dissolves when states or empowered actors possess the capacity to incessantly monitor and algorithmically shape cognitive processes. Compliance is no longer coerced but optimized through imperceptible, continuous cognitive intervention. Consent itself is transformed—a choice that appears freely made is, in fact, the product of systematic manipulation of the information and psychological environment. The “choosing” is done to the citizen, not by the citizen.
D. Constitutional Adaptation: Substance Has to Catch Up to Form
Canadian constitutionalism assumes four things: that people can actually participate in an open information space (s. 2(b)); that their choices are genuinely theirs (s. 7); that state power is visible enough to be named and reviewed (Charter application); and that remedies exist when power goes wrong (s. 24). Cognitive-warfare architectures stress-test every one of those assumptions, but that does not mean the Constitution is helpless. Canada already has the tools to adapt. The “living tree” approach (Edwards v. Canada (AG), [1930] AC 124) is exactly for this—extending old principles to new technologies. Courts have already taken s. 8 from physical cupboards to wiretaps (Duarte), to video (Wong), to metadata (R. v. Spencer), to phones as “a portal to the digital world” (R. v. Fearon, 2014 SCC 77). The same move is available for s. 7: Blencoe, 2000 SCC 44 confirms that state-enabled psychological harm can trigger s. 7; cybertorture is just the technologically updated version of the same harm. Likewise, Dolphin Delivery itself warns against drawing the public/private line “with narrow precision”; later cases (Eldridge, Stoffman, GVTA) already pierce that line where private actors are really implementing government policy. There is no doctrinal bar to saying: “If the state supplies the intel, sets the objective, and benefits from the operation, the Charter applies—even if a contractor pulled the lever”.
What is missing is not law but uptake. Canadian law already allows inference from patterns when direct proof is structurally unavailable: conspiracy (R. v. Carter), systemic discrimination (CN v. Canada (CHRC)), and reasonable suspicion for police investigations (R. v. Debot). The very kind of evidence being assembled—tight temporal convergence, non-public information surfacing externally, parallel institutional declinations, repeat symbolism—fits comfortably inside that tradition. Parliament, for its part, has repeatedly legislated to catch up to tech (computer crime, child-exploitation materials, identity theft); it can do so again for cybertorture, neurorights, and warrant requirements for algorithmic feedback loops. International mechanisms (UN Special Rapporteurs, Inter-American system) remain a pressure valve when domestic actors refuse to look—Canada’s CAT obligations already require investigation of credible torture-adjacent claims. So the practical diagnosis is that the Charter is being under-applied. Courts can extend existing principles, police can investigate on a Debot standard, Parliament can criminalize coordinated technological harassment, oversight bodies can stop hiding behind jurisdiction. The window is open now; what will close it is not constitutional incapacity, but institutional refusal to use the tools already on the table.
XI. SYNTHESIS: THE CASE STUDY AS MICROCOSM
A. What the Pattern Proves
The documented four-year case study exemplifies a confluence of evidence—temporal convergence between sealed court events and externally scripted social media content, indicators of biometric data trafficking, anomalies in legal billing, institutional foreclosure, and psychiatric weaponization—that validates several key theoretical frameworks.
The UN Framework (A/HRC/43/49), developed by the Special Rapporteur on Torture, establishes that severe mental suffering inflicted continuously, coupled with intentional coordination, a prohibited purpose (such as coercion, intimidation, or punishment), and a systemic power imbalance, fulfill the criteria for psychological torture. The case demonstrates these elements vividly: timing and content alignments verify intent; the targeted psychological harm exceeds ordinary distress levels; institutional pathways are systematically closed, heightening the victim’s powerlessness.
Military doctrine, particularly NATO’s Joint Publication 3-13.2, emphasizes targeting analysis, message optimization, saturation across multiple channels, synchronized timing with legal events, and attribution obfuscation—elements surely present in the case. The capabilities revealed by Snowden’s JTRIG documents—reputation destruction (via sealed files and revisionist narratives), operational disruption (through institutional foreclosure), deception, and psychological degradation—are exemplified in the coordinated narratives and covert manipulation documented.
Similarly, the influence strategies outlined by Wylie and Kaiser in the Cambridge Analytica disclosures—psychographic profiling, real-time content adaptation, exploitation of platform algorithms, and behavioral influence—mirror the tactics deployed in the case’s social media manipulation. Sheridan et al.'s phenomenology confirms the victim’s perception of 24/7 surveillance, technology-mediated harassment, and institutional dismissiveness, aligning with the pattern’s core.
Ultimately, this case is not an outlier but an exemplar: where sophisticated influence tools are deployed against an individual, the operational architecture becomes visible through pattern analysis. The challenge lies in most targets lacking the technical, legal, and analytical capacity to document systematically, temporally, or independently—even fostering survivor reporting bias and dismissing valid operations as delusions.
B. The Institutional Response: Coordination Through Declination
Over twenty institutions systematically declined to investigate or engage with documented concerns. Law enforcement agencies, including Halifax Regional Police and the RCMP, refused action or deflected jurisdiction. Courts declined substantive review despite evidence and binding authorities. Regulatory bodies and ombudsmen either refused oversight or failed to respond. Political representatives provided referrals without meaningful intervention, while medical and emergency services accepted reports uncritically, contributing to involuntary detentions.
This widespread pattern is not a series of isolated errors but a coordinated operational approach. Each institution invokes procedural barriers—jurisdictional limits, resource constraints, or priorities—but the functional outcome is comprehensive foreclosure of accountability. This coordination through declination maintains plausible deniability and shields protected interests by ensuring no single entity breaks ranks. The repeated refusal to investigate, despite compelling documentary evidence and public interest, constitutes evidence of an organized mandate to prevent scrutiny and sustain institutional impunity.
XII. RECOMMENDATIONS: CONSTITUTIONAL GUARDRAILS FOR THE COGNITIVE WARFARE ERA
A. Immediate Regulatory Requirements
The state must close the technology-enabled legal gaps by codifying explicit constitutional constraints on dual-use neuro- and info-sphere technologies.
-
Judicial Warrant for Algorithmic Targeting: Any system engaged in psychographic profiling, real-time biometric monitoring, or micro-targeted content delivery must be subjected to the Oakes test standard (pressing and substantial objective, proportionality, and necessity) and require a judicial warrant.
-
New Offense: Algorithmic Harassment: Amend the Criminal Code to introduce a specific, high-level offense for coordinated, technology-mediated psychological operations against individuals. This must capture conduct designed to inflict severe mental suffering or coerce behavior.
-
Neuro-Rights and Precautionary Ban: Establish a Canadian Neurorights Act (following the Chilean model) to protect neural data as a uniquely safeguarded category. Institute a precautionary ban on non-consensual neural monitoring, remote neural interfaces, and AI systems explicitly designed for psychological manipulation.
-
Charter Accountability for Contractors: Legally deem government contractors involved in information operations or psychological research to be government actors for Charter purposes. This is essential to pierce the "plausible deniability" shield and ensure Section 32 applicability and Section 24 remedies.
B. Institutional Reforms: Breaking the Cycle of Declination
To overcome the proven operational security tactic of "coordination through declination" (Section VIII), institutions must be restructured for active investigation.
-
Establish an RCMP Cybertorture Investigation Unit: Create a dedicated, federally-funded unit within the RCMP with expertise in digital forensics, algorithmic analysis, human rights law, and the phenomenology of organized harassment. This specialized unit must have clear jurisdiction and a $50 million-plus annual budget to reflect the gravity of the threat.
-
Independent Cognitive Security Review Agency (CCSRA): Establish an independent oversight body, similar to NSICOP, with the mandate to review all government and contractor operations that involve cognitive warfare, strategic communications, and mass psychological profiling targeting Canadians. The CCSRA must have powers to compel classified testimony and publish findings.
-
Mandatory Judicial Education: Require mandatory, ongoing education for all levels of the judiciary covering cognitive warfare doctrine, PSYOP indicators, international cybertorture law, and algorithmic manipulation to counteract the systemic dismissal-as-delusion bias in courts.
-
Reform Evidentiary Standards for Covert Operations: Amend rules of evidence to explicitly allow pattern-based inference when direct proof is structurally unattainable. Temporal correlation, symbolic convergence, and consistent institutional declination must trigger a burden shift, requiring the state to disprove coordinated, systematic activity.
C. International Coordination: A Unified Defense
Canada must proactively lead in international forums to establish norms of accountability against these transnational threats.
-
Binding Five Eyes Human Rights Protocol: Adopt a formal agreement that absolutely forbids the targeting of partner states’ citizens and mandates mutual legal assistance and joint investigations for all transnational cybertorture claims.
-
NATO Cognitive Warfare Ethics Framework: Push for a NATO framework that emphasizes defensive-only operations, imposes the principles of proportionality with reversible cognitive effects, and establishes clear command accountability for cognitive warfare crimes akin to war crimes.
-
Cybertorture Protocol to the CAT: Advocate for an expansion of the UN Convention Against Torture with a cybertorture-specific protocol that recognizes technology-mediated psychological torture and clearly assigns state and corporate responsibility.
D. Individual Protective Measures (Harm Reduction)
While legal frameworks evolve, targeted individuals require immediate, evidence-based harm reduction strategies.
-
Rigorous Documentation Mandate: Individuals must be educated on the need for timestamped, metadata-preserved, and securely archived evidence (screenshots, recordings). Use of trusted third parties (academics, specialized counsel) for data preservation is essential.
-
Digital Hygiene as Self-Defense: Promote the use of encrypted communications, VPNs, and techniques for minimizing the collection of biometric and psychographic data through smart devices, which are currently being weaponized for targeting.
-
Specialized Advocacy: Encourage collaboration with specialized legal counsel and trauma-informed clinicians who are conversant with the symptoms and documentation of PSYOP effects, to prevent institutional misdiagnosis and dismissal.
XIII. FINAL SYNTHESIS: AN EVOLVING PLAYBOOK
A. The Progression Documented
This article has traced evolution from:
Classical PSYOP (1940s-1990s):
-
Persuasion campaigns targeting foreign adversaries
-
Information-based influence (leaflets, radio, messaging)
-
Time-limited operations with defined objectives
-
Attribution acceptable (psychological impact of known source)
Information Operations (2000s-2010s):
-
Expanded to "information environment" as battlespace
-
Multi-domain integration (cyber, electronic warfare, PSYOP convergence)
-
Continuous peacetime operations ("Phase Zero" shaping)
-
Attribution obscured (deniability valuable)
Cognitive Warfare (2020s):
-
Human mind as sixth domain
-
Neurobiological exploitation (targeting brain function directly)
-
Permanent operations (no peace treaty possible)
-
Domestic deployment (foreign/domestic distinction collapsed)
Cybertorture (UN Recognition, 2020+):
-
Severe mental suffering without physical contact
-
Intentional, systematic, coercive
-
State/corporate/criminal convergence
-
Effective powerlessness of victims
Biodigital Feedback Systems (UN Recognition, 2021+):
-
Real-time biometric monitoring feeding targeting algorithms, including graphene and GQD-based brain-computer-interfaces
-
AI-optimized messaging responding to physiological states
-
Closed-loop manipulation (automated behavioral modification)
-
Ubiquitous deployment through consumer technology
Current Reality: Capabilities theorized by militaries, documented by UN, confirmed by whistleblowers, and experienced by targeted individuals are operationally deployed today—not as future threat but as present practice.
B. The Case Study's Significance as an Operational Exemplar
The documented four-year pattern represents rare, systematic visibility into operations that are otherwise designed to be deniable.
Why the Pattern is Valuable:
-
Temporal Convergence: Proves real-time access to private, sealed events (correlated with external content within hours).
-
Symbolic Precision: Proves surveillance (non-public details appearing in external scripts).
-
Financial Anomaly: Proves pre-coordination and corruption of process (the 9,000% billing scandal).
-
Institutional Coordination: Proves an organizing mandate (twenty agencies systematically decline investigation, providing operational security).
-
Psychiatric Weaponization: Proves a discrediting strategy (clinical records are used to pre-dismiss legitimate complaints).
Algorithmic Validation of Operational Signature: When the documented patterns of temporal and symbolic convergence were subjected to independent algorithmic pattern recognition software, the analysis consistently yielded conclusions of a high statistical probability of non-random, coordinated intervention. This technical assessment supports the inference of a deliberate operational signature matching military and intelligence doctrine, providing validation beyond the subjective experience of the target.
C. The Implications for Every Canadian
"I'm not a target; this doesn't affect me"— Wrong.
A reasonable reader could infer that the conduct documented here points to a broader mass-surveillance posture—one capable of citizen-level profiling and, at the outer edge, discreet cognitive-intervention technologies. Those capabilities exist, and their feasibility, and their likely use-case, is already canvassed in the Testimony and 4IR Portal pages. For present purposes, however, this article takes the conservative view: it proceeds on the narrowest operational hypothesis—that the subject was deliberately targeted as an individual. We will assume that it required the surveillance of one person’s communications, court activity (including sealed material), psychographic profiling, coordinated content pushes across 50+ channels, and parallel institutional declinations. Most Canadians may never see that level of attention. But the fact it can be done to one person tells you numerous things about the system doing it.
1. Targetability is discretionary.
You become vulnerable not because you did something “wrong,” but because you became inconvenient: you challenged and/or upset a state-adjacent actor, exposed fraud, held incriminating data, or simply showed up as anomalous in a monitored system that has attracted action for whatever reason. The capability exists first; deployment is a choice. That means anyone who becomes effective—whistleblowers, journalists, litigants, organizers—can be moved from “background” to “target.”
2. The infrastructure to target a few reshapes life for everyone.
To run individualized cognitive operations, the system needs: platform-level data extraction, cross-agency information sharing, opaque cooperation with private vendors, and algorithmic curation. Even if it’s never pointed at you, that same infrastructure narrows what you see online, lowers the privacy baseline, fragments public discourse through micro-targeting, and normalizes secrecy (sealed files, national-security carve-outs). You live inside the targeting substrate even if you’re not the current target.
3. Discretionary enforcement creates a two-tier Charter.
What the case shows is not just surveillance—it’s coordination through declination: courts, police, regulators, ombuds all saying “not us” in ways that protect the powerful and isolate the complainant. That pattern can be reused for police complaints, professional-regulator complaints, and judicial-conduct complaints. So even if you never face PSYOP content, you do face a system that can close ranks when the respondent is networked.
4. Today’s exception becomes tomorrow’s routine.
Historically, tools built for “serious threats” (wiretaps, no-fly lists, bulk metadata) drift outward to protesters, journalists, and finally to nuisance or “non-compliant” populations. Cognitive-warfare tooling will follow the same ratchet: national-security → misinformation → policy dissent → ordinary irritants. Stopping the overreach now protects non-targets later.
5. The individual case exposes the governance model.
It shows Canada already has the technical, bureaucratic, and narrative capacity to run deniable, multi-channel pressure on a single citizen and to make every oversight body look away. Once that capacity is normalized, the only safeguard left is who they choose to use it on—which is not a constitutional safeguard.
6. The pool of potential targets is larger than people assume.
Sheridan, James & Roth (2020) started from ~20 million online references to organized/technology-mediated harassment claims and, after filtering, still found a stable, repeatable experiential pattern—continuous surveillance, technology interference, coordinated social presence, institutional dismissal—across unconnected reporters. Their conclusion was not “a few delusional outliers,” but that the phenomenology is widespread and harmful, and that institutional dismissal may be part of the phenomenon itself. That means two things: (a) the signal is already in the population, it’s not hypothetical; and (b) once you count under-reporting, psychiatric misclassification, and people who stop talking because they’re disbelieved, the true exposure rate is plausibly much higher than what gets to court or media. In other words: the odds of someone like you encountering some version of this are not remote—they’re just systematically under-recognized.
Finally, in an event we are dealing with a technocratic Citizen-profiling system (likely more sophisticated than the RCMP's Project Wide Awake), the concerns raised by this website are FAR more concerning, and likely are affecting you right now as you read this.
SOURCES & REFERENCES
UN & International Human Rights
-
Melzer, Nils. "Psychological torture and ill-treatment." UN Doc. A/HRC/43/49 (20 March 2020)
-
OHCHR. "Non-exhaustive list of Special Procedures reports on new technologies"
-
Bowcott, Owen. "UN warns of rise of 'cybertorture' to bypass physical ban." The Guardian (21 Feb 2020)
-
Convention Against Torture and Other Cruel, Inhuman or Degrading Treatment or Punishment (1984)
Military Doctrine & Cognitive Warfare
-
U.S. Joint Chiefs of Staff. Joint Publication 3-13.2: Military Information Support Operations (2021)
-
U.S. Army. Field Manual 3-05.301: Psychological Operations: Tactics, Techniques and Procedures
-
U.S. Joint Chiefs of Staff. Joint Publication 3-13: Information Operations (2014)
-
du Cluzel, François. Cognitive Warfare. NATO ACT Innovation Hub (2020)
-
NATO. "Countering cognitive warfare: awareness and resilience." NATO Review (20 May 2021)
-
Geneva Centre for Security Policy. Peace of Mind: Cognitive Warfare and the Governance of Subversion in the 21st Century (2023)
-
NATO Strategic Communications Centre of Excellence. Countering Disinformation in the Euro-Atlantic (2024-2025)
-
Hybrid Centre of Excellence. Countering Disinformation in the Euro-Atlantic, Research Report 15 (Oct 2025)
Canadian Military & Government
-
Canadian Global Affairs Institute. "The Rise and Fall of Military Strategic Communications at National Defence, 2015–2021" (2021)
-
Rideau Institute. "Minister of National Defence cancels information operations plan" (16 Nov 2020)
-
PressProgress. "Military admits it made 'errors' aiming propaganda at Canadians" (25 June 2021)
-
Policy Horizons Canada. Exploring Biodigital Convergence (2020)
-
Canadian Forces College. "Shifting the Mindset Towards Phase Zero: Shaping in the Information Environment"
Intelligence/Whistleblower Revelations
-
Snowden, Edward. GCHQ/JTRIG documents: "The Art of Deception: Training for Online Covert Operations" (2013-2014)
-
Greenwald, Glenn & Andrew Fishman. "GCHQ's Dirty Tricks." The Intercept (2014)
-
Wylie, Christopher. Testimony to UK Parliament & US Congress re: Cambridge Analytica (2018-2019)
-
Kaiser, Brittany. Media testimony & Targeted (2019)
-
Reuters. "Pentagon ran secret anti-vax campaign" (2024)
Academic & Peer-Reviewed
-
Sheridan, Lorraine, David V. James & Jayden Roth. "The Phenomenology of Group Stalking ('Gang-Stalking'): A Content Analysis of Subjective Experiences." International Journal of Environmental Research and Public Health 17(7):2506 (2020). PMC7178134
-
RAND Corporation. "The Russian 'Firehose of Falsehood' Propaganda Model" (2016)
-
Various articles on "cybertorture," "psychological torture," and "gang-stalking" from ResearchGate, Academia.edu, PubMed
UK & Allied Military
-
UK Ministry of Defence. 77th Brigade official information
-
Declassified UK. "UK psychological warfare unit collaborated with Israeli army" (8 Oct 2024)
-
UK Parliament. Defence in the Grey Zone (9 July 2025)
Political Theory & Philosophy
-
Crouch, Colin. Post-Democracy (2004)
-
Wolin, Sheldon. Democracy Incorporated: Managed Democracy and the Specter of Inverted Totalitarianism (2008)
-
Foucault, Michel. Discipline and Punish (1975); The History of Sexuality, Vol. 1 (1976); Power/Knowledge (1980)
Canadian Case Law
-
R. v. Oakes, [1986] 1 SCR 103
-
R. v. Duarte, [1990] 1 SCR 30
-
Hunter v. Southam, [1984] 2 SCR 145
-
R. v. Spencer, 2014 SCC 43
-
Sherman Estate v. Donovan, 2021 SCC 25
-
Canada (Minister of Citizenship and Immigration) v. Vavilov, 2019 SCC 65
-
Beals v. Saldanha, 2003 SCC 72
-
Ruffo v. Conseil de la magistrature, [1995] 4 SCR 267
-
Nova Scotia (AG) v. Morrison Estate, 2009 NSCA 116
-
Power v. Power, 2013 NSCA 137
-
R. v. Wise, [1992] 1 S.C.R. 527
-
R. v. Villaroman, 2016 SCC 33, [2016] 1 S.C.R. 1000
-
Edwards v. Canada (AG), [1930] AC 124
Media & Investigative Reporting
-
Serafin, Stéphane & Kerry Sun. "Unchecked Judicial Power: That's Chief Justice Wagner's Vision for Canada." National Post / Macdonald-Laurier Institute
-
Mad In America. "UN Warns of Rise of Psychological 'Cybertorture'" (25 June 2021)
-
Various YouTube channels documented in case study (preserved with metadata)
Case-Specific Documentation
-
Emergency registration records, Halifax QEII (May 13, 2023)
-
Audio recording (May 13, 2023)
-
Audio recording (December 8, 2022)
-
Court filings across BC, NS, and the SCC (2021-2025)
-
ChatGPT/Claude(Anthropic)/Perplexity AI analysis outputs (July - November 2025)
-
Social media content archive (200+ videos, time-stamped, preserved)
-
Institutional correspondence (police, courts, regulators) documenting systematic declination
"Net-Zero E-Missions"
























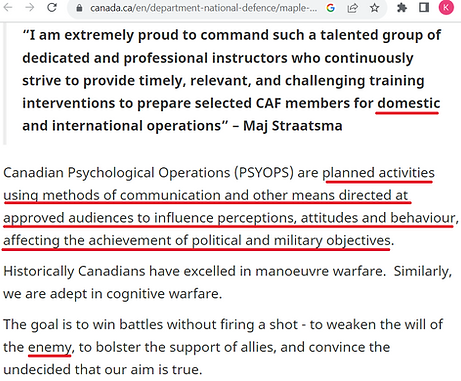


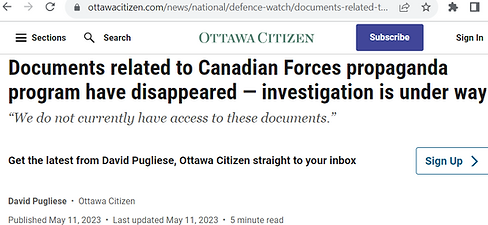










Contemporaneous Feedback Loops

May 11th, 2023: I prepared a backyard bonfire as I do from time to time. Nearby foliage caught fire by accident, mea-culpa. The fire was quickly contained using two buckets of water. Fire dept arrived within minutes. Police arrived concurrently. Fire was out before they arrived. Personnel departed soon after.
May 13th, 2023: A "Mental Health Crisis Team" arrives early Saturday morning with a police paddy wagon. I was handcuffed and taken to the QE2 (hospital). I was required to wait 5 hours in the ER lobby and be interviewed by a psychiatrist. Social Worker advised her "real concern" was related to the December 8th, 2022 false police report as denoted above. Police "sought a deposition" from psychiatrist. Ushered into a windowless 8x10 room fitted with ceiling-mounted video cameras, I walked the psychiatrist through my Affidavit, notarized the previous day. Psychiatrist agreed that a compelled visit to a mental health facility is a disproportionate response to a campfire accident. True audio transcript excerpts below.


As above per the embellished HRP report that was provided to EHS. Full details at the HRP Page (Here).



May 13, 2023 Live Audio Recording Hfx QE II
Irreparable Harms
THE IRREPARABLE HARMS OF STATE-ADJACENT PSYCHOLOGICAL OPERATIONS:
Neurobiological Damage, Permanent Psychological Injury, and the Weaponization of AI-Assisted Influence Systems
ABSTRACT
State-adjacent psychological operations (PSYOPs) leveraging AI-assisted influencers, algorithmically tuned content farms, and closed-loop biometric feedback systems inflict harm that is not merely distressing but functionally irreparable. Drawing on (1) neuroscience documenting long-lasting structural and connectivity changes in the brains of torture and chronic-trauma survivors, (2) clinical literature on Complex PTSD (CPTSD) as a chronic interpersonal trauma syndrome, and (3) military and intelligence doctrine explicitly aimed at inducing learned helplessness and identity collapse, this article argues that technology-mediated psychological warfare typically produces: (a) durable neurobiological alterations (e.g., hippocampal volume loss, default mode network dysregulation, stress-system remodeling); (b) chronic psychological injury including complex trauma, identity fragmentation, and enduring affective and relational impairment; (c) "social death" through coordinated reputation destruction, institutional foreclosure, and relational annihilation; and (d) erosion of cognitive autonomy that undermines democratic participation.
Even under optimistic treatment scenarios, these harms leave survivors with lifelong impairment relative to pre-exposure baseline. From the perspective of torture law, constitutional rights, and remedies doctrine, such PSYOPs must therefore be understood as permanent assaults on personhood rather than reversible episodes of distress, and their deployment against domestic populations is incompatible with any principled proportionality analysis.
Keywords: Psychological Operations (PSYOP), Cybertorture, Complex PTSD, Neurobiological Damage, Learned Helplessness, Cognitive Warfare, AI-Assisted Targeting, Algorithmic Harassment, Irreparable Injury, Brain Connectivity, Hippocampal Atrophy, Identity Fragmentation, Social Death, Torture Survivors, Default Mode Network (DMN), Central Executive Network (CEN), Allostatic Load
I. INTRODUCTION: FROM DISTRESS TO FUNCTIONAL IRREPARABILITY
Debate about technology-mediated psychological operations often turns on whether the resulting harm is "serious enough" to sound in torture law, constitutional protection, or hard-edged human rights norms. That debate usually assumes the harms are intense but ultimately reversible: painful, terrifying, disorienting—yet in principle recoverable with time, treatment, and social repair.
This article challenges that assumption. Drawing on convergent evidence from neuroscience, clinical trauma literature, UN torture frameworks, and psychological operations doctrine, it argues that when AI-assisted, state-adjacent PSYOPs are prolonged, inescapable, and interpersonal, the typical outcome is not transient distress but long-term or lifelong impairment. Survivors may adapt, cope, and build meaningful lives; they do not, in any ordinary sense, "get back" to their pre-targeting baseline.
Four dimensions matter:
-
Neurobiological: Structural and functional changes in brain regions and networks involved in memory, stress regulation, and self-referential processing
-
Psychological: Complex PTSD and related conditions characterized by durable impairment in self-regulation, identity, and relationships
-
Social: Reputation and network collapse amounting to "social death" in digitally mediated societies
-
Civic-cognitive: Erosion of cognitive autonomy and epistemic trust necessary for democratic participation
The claim is not that every survivor exhibits identical changes, nor that improvement is impossible. Rather, it is that under conditions typical of sophisticated PSYOPs—chronic exposure, interpersonal betrayal, algorithmic environmental saturation—the modal outcome is functionally irreparable harm: injury that current medical, psychological, and social remedies cannot reverse to pre-exposure status. From the perspective of torture law and constitutional proportionality, this functional irreparability matters more than metaphysical debates about absolute irreversibility.
II. NEUROBIOLOGICAL EVIDENCE: LONG-LASTING BRAIN STRUCTURE AND FUNCTION CHANGES
A. Hippocampal Volume Reduction and Memory System Damage
Imaging studies of torture survivors and chronic PTSD populations frequently report reduced hippocampal volume, with robust effects in several cohorts.[^1] One PET/MRI study found “the mean left hippocampal volume for the TR-PTSD group was significantly lower than in the HV group” (p < 0.001), alongside gray-matter reductions and diffusion abnormalities in frontal and occipital regions.[^2]
Because the hippocampus supports memory consolidation, contextual fear learning, and spatial orientation, shrinkage is associated with impaired new learning and retrieval, difficulty distinguishing safety from threat, and dysregulated fear responses. These changes emerge during a post-trauma “critical period of increased brain plasticity, during which irreversible neuronal changes may occur in those who develop PTSD,”[^3] and—on current evidence—do not spontaneously reverse or return to pre-trauma volume with available treatments.
B. Altered Brain Network Connectivity
Chronic trauma is also linked to durable alterations in intrinsic connectivity among the default mode (DMN), central executive (CEN), salience, and attentional networks.[^4] Studies report increased CEN–DMN dynamic connectivity with correlates such as emotional rigidity, withdrawal, self-regulation problems, and reduced responsiveness to positive social cues—changes observed on average a decade after torture exposure.[^5] Additional work shows reduced posterior DMN (left precuneus) and auditory-motor connectivity and concludes that “torture exposure itself may therefore fundamentally alter the way intrinsic networks of the brain—in particular the CEN and DMN—function and connect.”[^6]
Functionally, networks that should flexibly switch between internal mentation, task focus, and environmental scanning become locked into maladaptive patterns—experienced as inability to “switch off,” intrusive self-referential rumination, and persistent social disengagement despite objectively safe contexts.
C. Dysregulated Stress Response Systems and Allostatic Load
Prolonged trauma remodels the HPA axis and related neuroendocrine systems, producing altered cortisol rhythms, changes in mediators such as Neuropeptide Y, and downstream cardiovascular, metabolic, and immune effects.[^7] The resulting allostatic load—the cumulative cost of sustained threat readiness—is consistently associated with chronic musculoskeletal pain, hypertension, hyperlipidaemia, obesity, and cardiovascular disease.[^8] Clinically, this profile reflects accelerated biological aging and persistent systemic vulnerability, even when subjective distress fluctuates.
D. Sensitization, Kindling, and Progressive Escalation
A well-described pathway to chronicity involves sensitization (lowered threshold for stress responses) and kindling (progressive amplification). As one review summarizes: “the progressive escalation of symptoms with the passage of time leading to delayed-onset PTSD involves sensitization and kindling,” with repeated environmental triggering driving increasing dysregulation over time.[^9] Practically, each exposure lowers response thresholds, intensifies reactions, generalizes triggers, and shortens recovery windows. Closed-loop, AI-assisted targeting that monitors biometrics and dynamically times stimuli exploits this trajectory—optimizing toward deterioration.
E. Practical Irreversibility
As McEwen notes, “some changes are reversible,” but under prolonged stress “the brain is never the same as it was before.”[^10] Reisner’s formulation captures the evidentiary challenge: “psychological torture undermines the very ability to think, and it doesn’t leave any marks.”[^11] Current interventions mitigate but do not restore prior neurobiology: trauma-focused CBT reduces symptoms without reconstituting structure; pharmacotherapy dampens hyperarousal without normalizing connectivity; social support buffers exposure without eliminating hypersensitivity; and time brings adaptation, not a return to baseline. Survivors can improve meaningfully, but the typical outcome after prolonged exposure is a persistently altered system.
III. PSYCHOLOGICAL EVIDENCE: COMPLEX TRAUMA AS CHRONIC INJURY
A. Complex PTSD: Beyond Single-Incident Trauma
Complex PTSD (CPTSD) arises from chronic, often inescapable interpersonal trauma, not a single event, and includes the core PTSD triad plus enduring relational and self-concept disturbances.[^12][^13] Canonical definitions emphasize multiple, interpersonal assaults or threats and note that interpersonal traumatization is typically more severe than impersonal forms.[^14]
Modern PSYOP architectures map onto this profile: they are premeditated, interpersonal (via influencers/family-adjacent actors), repetitive (continuous streams), and exploitative (psychographic targeting). Prevalence estimates suggest ~3% current PTSD and ~4% CPTSD among U.S. adults, underscoring that CPTSD is at least as prevalent as PTSD and often more disabling.[^15]
B. Identity Fragmentation and Self-Concept Disruption
CPTSD features alterations in the sense of self, including unstable self-structure and pervasive shame.[^16] Following Herman’s framework, variability in outcomes reflects exposure pattern and inescapability, not simply event type; interpersonal betrayal (especially by trusted figures) is particularly corrosive.[^17]
When PSYOPs enlist familial actors (as in the case study’s “prophetic” channel), they weaponize attachment, producing deep identity rupture within the very relational matrix that ordinarily enables healing.
C. Affect Dysregulation and Emotional Control Loss
Complex trauma is marked by impaired affect regulation—difficulty modulating anger, self-destructive impulses, and shifting rapidly between numbness and overwhelm.[^18] Because these events are other-inflicted, survivors often develop profound mistrust and a sense of emotional uncontrollability.[^19]
Closed-loop, AI-assisted targeting that times stimuli to biometric arousal conditions the emotional system to expect attack, entrenching dysregulation and making true baseline states hard to re-establish even in safety.
D. Interpersonal Functioning Impairment
CPTSD reliably yields relational instability: isolation/withdrawal, attachment disturbance, and difficulty sustaining bonds.[^20] Downstream effects include trust collapse, attachment insecurity, social withdrawal, and intimacy impairment, with long-term risks documented in child and adolescent cohorts (self-harm, suicidality, poorer attainment).[^21]
Where PSYOPs simultaneously destroy networks (defamation), block validation (institutional foreclosure), and fracture families, survivors face enduring social incapacity that persists even if overt operations cease.
E. Treatment Limits: Adaptation Rather Than Restoration
Evidence-based trauma therapies (including trauma-focused CBT) reduce symptoms in CPTSD, but residual problems—mood, relationships, identity—often remain.[^22] Guidance acknowledges significant evidence gaps (especially for prevention and developmental trajectories) and the absence of a reliably preventive model post-exposure.[^23]
Recovery frameworks stress that people can improve meaningfully and that it is never too late to begin, yet “recovery” typically means adaptive functioning at a changed baseline, not restoration to pre-trauma architecture.[^24]
IV. UN CYBERTORTURE FRAMEWORK: TECHNOLOGY-MEDIATED PSYCHOLOGICAL TORTURE
A. Melzer’s Definition and Framework
On 20 March 2020, UN Special Rapporteur on Torture Nils Melzer presented A/HRC/43/49 on psychological torture and ill-treatment, offering a detailed legal framework for technology-enabled coercion.[^25] He proposes that “psychological torture” encompasses “all methods, techniques and circumstances… intended or designed to purposefully inflict severe mental pain or suffering without using the conduit or effect of severe physical pain or suffering.”[^26]
Under the CAT, art. 1, severe psychological suffering can amount to torture where four elements converge: (1) severe mental pain or suffering; (2) intentional infliction; (3) a prohibited purpose (punishment, coercion, intimidation, discrimination); and (4) conditions of effective powerlessness.
B. Cybertorture: Capabilities and Characteristics
Within that framework, Melzer identifies cybertorture: digitally mediated operations capable of inflicting severe mental suffering through networked means. Characteristic techniques include persistent intimidation/harassment; continuous surveillance; defamation and public shaming; manipulation/deletion of personal or financial data; and orchestrated social exclusion. Such harassment can drive “extremely elevated and prolonged… anxiety, stress, social isolation, and depression,” heightening suicide and long-term trauma risks.[^27] The juridical crux: “Cybertechnology can inflict severe mental suffering while avoiding the conduit of the physical body.”[^28] This yields plausible deniability (no visible injuries) even as precision, duration, and inescapability amplify destructive potential.
C. State, Corporate, and Organized-Criminal Capabilities
Melzer warns that states, corporate actors, and organized criminals can conduct cyber-operations inflicting severe suffering—and may do so for the purposes of torture.[^29] In practice, public–private–criminal fusion (intelligence/IO capacity + platform/data control + outsourced tools) creates diffuse accountability and layers of deniability through which torture-level psychological operations can be executed and concealed.
D. Powerlessness in Digital Environments
“Powerlessness” arises when a person is under direct physical or equivalent control and has effectively lost the capacity to resist or escape suffering.[^30] Melzer stresses that powerlessness can be achieved by deprivation of legal capacity, serious and immediate threats, coercive control (e.g., domestic violence), incapacitating medication, and—depending on circumstances—mobbing, cyberbullying, and State-sponsored persecution that deprive victims of any effective means of resistance or escape.[^31] Digitally saturated environments can therefore replicate custody-like power asymmetries: “escape” would require withdrawing from essential digital life.
E. Severity and Mental Suffering
“Severe mental suffering” may be established subjectively (experienced anguish) or objectively (demonstrable mental harm) even absent conscious distress.[^32] This is pivotal for AI-assisted or neurotechnological manipulation: suppressing subjective awareness (e.g., by drugs or cognitive intervention) does not negate torture where mental identity, capacity, or autonomy are objectively impaired. The framework thus forecloses attempts to evade CAT prohibitions via cognitive or perceptual dampening.
V. PSYCHOLOGICAL OPERATIONS DOCTRINE: DESIGNING HELPLESSNESS AND IDENTITY COLLAPSE
A. Learned Helplessness as Operational Objective
The Senate torture report documents that the CIA program sought to render detainees passive and powerless—engineering learned helplessness via sleep deprivation, stress positions, and waterboarding.[^33] PSYOP doctrine generalizes the same compliance logic: overwhelm coping capacity, strip perceived control, close all exits, induce desperation, and secure acquiescence. At scale, AI-assisted operations that synchronize multi-channel content within hours of sensitive events and persist despite complaints prove to targets that nothing they do can stop the assault.
B. Identity Attack and Self-Concept Destruction
“Torture is the deliberate and systematic dismantling of a person’s identity and humanity,” aimed at destroying community and creating fear.[^34] Operationally, identity is attacked across domains: name/reputation, profession, family roles, spiritual/ideological commitments, and bodily autonomy (e.g., sexual humiliation). When PSYOPs deploy familial actors and spiritual/“prophetic” content, they simultaneously degrade family, spiritual, moral, and social identities—driving identity collapse when all anchors are contested at once.
C. Social Isolation and Support Network Annihilation
Isolation is foundational: it fosters dependence and magnifies harm.[^35] Digitally enabled PSYOPs achieve totalizing isolation by combining institutional foreclosure (police, courts, regulators decline), familial alienation, reputational defamation, professional destruction, and algorithmic siege—leaving targets without support or viable escape routes.
D. Continuous Retraumatization Through Environmental Triggering
Accounts of detention describe darkness for weeks and mock executions, with survivors reliving near-death in nightmares and flashbacks.[^36] The same architecture can be informationalized: create a traumatic memory → identify cues (symbols, dates, places) → deploy triggers continuously with unpredictable intensity → exploit sensitization so each trigger makes the next more potent. AI systems that read biometric arousal and tune timing/content become automated retraumatization machines.
E. Institutional Foreclosure Creating Inescapability
Basoğlu shows that the loss of control—not pain severity—drives trauma depth; anticipation can be worse than pain, and benign acts become devastating when combined to eliminate agency.[^37][^38] In civic contexts, coordinated declinations across agencies, sealed files, psychiatric weaponization, financial barriers (e.g., outsized securities/costs), and jurisdictional buck-passing manufacture inescapability. The resulting powerlessness converts serially distressing events into a chronic traumatic condition with lasting harm.
VI. AI-ASSISTED AND ALGORITHMIC AMPLIFICATION OF HARM
A. Closed-Loop Biometric Targeting: Real-Time Harm Optimization
Modern AI influence systems can run closed loops: they monitor physiological/behavioral signals (wearables, phones, interaction traces, or in vivo sensors like GQD), infer emotional state, deliver tailored content, and retune in real time based on measured responses. In this architecture, induced distress is the training signal.
Pipeline: monitor stress → infer state → generate/select distress-maximizing content → optimize delivery (timing/platform/format) → measure reaction → adapt the next iteration.
The result is automated harm escalation: higher baseline stress triggers intensified targeting; new coping attempts are detected and countered; resilience elicits precision strikes at residual vulnerabilities. Unlike humans, the system does not fatigue or empathize; it optimizes consistently toward trauma.
B. Algorithmic Content Farms: Saturation and Inescapability
AI enables high-volume, multi-platform, thematically coordinated output that floods a target’s information environment, making avoidance impossible short of abandoning digital life.
Scale–Consistency–Adaptation: (i) scores of channels; (ii) 24/7 synchronized messaging with no recovery windows; (iii) A/B testing, psychographic segmentation, and SEO/recommender exploitation to maximize reach.
The “firehose of falsehood” model—high-volume, multichannel, rapid, and repetitive—produces uncertainty, paralysis, disengagement, and belief distortion,[^39] i.e., the same helplessness outcomes when individualized for a single target and optimized for harm rather than belief change.
C. Coordinated Influencer Networks: Multi-Vector Attack
AI-assisted operations add a human-facing layer—influencers, “prophetic” channels, and seemingly independent voices—producing interpersonal injury that pure automation cannot. In the documented case: 50+ coordinated channels, a family-adjacent operator with state ties, sub-24-hour convergence with sealed events, and symbolic precision mirroring private circumstances. This architecture creates interpersonal violation: perceived deliberate malice, betrayal, spiritual weaponization, and a manufactured sense of community consensus—amplifying harm, consistent with the heightened severity of interpersonal traumatization (see §III.A).
D. Personalization and Adaptation: Defeating Coping Strategies
By mining social/search/interaction data, systems identify and then target the pillars of coping—faith practices, legal recourse, supportive allies. Content is framed to undermine belief, ridicule justice-seeking, and alienate networks. Each coping move is observed, analyzed, and countered, teaching the target that constructive strategies fail. Neurobiologically, this drives extinction of healthy coping and drift toward maladaptive responses (substance use, self-harm, isolation), entrenching learned helplessness.
E. Scale, Duration, and Environmentalization
The case study spans four years at the time of publication (November 2025)—well beyond thresholds for sensitization/kindling (weeks–months), structural change (months–years), CPTSD with entrenched connectivity alterations (years), and long-tail allostatic morbidity (decades).
Because AI campaigns run with minimal human input, low marginal cost, and no operational drift, they can persist indefinitely, continually adapting to defeat habituation. What begins as a campaign becomes an ambient condition: the target must live as if never safe, reinforcing chronic hypervigilance and stress-system dysregulation.
VII. SOCIAL DEATH AND COGNITIVE AUTONOMY DESTRUCTION
A. Reputation Destruction as Permanent Social Injury
In networked societies, identity is partly externalized into search results, social feeds, and institutional records. Coordinated defamation produces structural, lasting harm through:
-
Digital permanence: archives, mirrors, screenshots, and recommender systems keep hostile content searchable and resurfacing.
-
Narrative primacy: early sensational claims outcompete later corrections; attempts to rebut often amplify the smear (Streisand effect).
-
Network effects: rapid cascades create the appearance of consensus and make isolation self-reinforcing.
Once this architecture hardens, reconstruction is impracticable: individuals cannot outspend organic algorithmic spread; corrections lack engagement uplift; legacy negatives suppress positives in ranking. The result is social death—biological life persists, but professional, civic, and intimate participation collapse.
B. Professional Annihilation and Economic Collapse
Targeted attacks on professional identity yield durable economic damage: credential and regulatory records become permanent, background checks surface defamatory material, fake-review campaigns and negative SEO erase market presence, and partners or funders disengage. After reputational collapse and resource depletion, recovery pathways close: retraining is unaffordable, hiring screens are disqualifying, financing is inaccessible, and reputation cannot be rebuilt without capital. Poverty-driven stress then exacerbates neurobiological injury.
C. Cognitive Autonomy Destruction: Eliminating Democratic Capacity
Democratic agency presupposes cognitive autonomy—attention, memory, reason-weighing, and stable judgment. The injuries outlined in §§II–III—impaired memory, attentional fragmentation, intrusive thoughts, affect storms—directly burden deliberation. Three reinforcing dynamics follow:
-
Trust collapse / epistemic helplessness: gaslighting, institutional indifference, and contradictory narratives erode confidence in media, officials, and even one’s own recollection, turning political information into another threat vector rather than material for reasoning.
-
Hypervigilance / threat bias: chronic vigilance reframes disagreement as danger; opponents are perceived as enemies; civic exposure feels unsafe.
-
Functional incapacity: instead of informed, stable participation, survivors withdraw, engage sporadically and reactively, or cannot navigate institutions already experienced as hostile.
Together, these effects convert formal citizenship into practical exclusion—the political analogue of social death.
VIII. CASE STUDY: A FOUR-YEAR PROGRESSION TO IRREPARABLE HARM
A. Duration and Escalation
From 2021–2025 (and counting), the subject faced coordinated online content synchronized with sealed legal events, family-adjacent messaging, and steadily intensifying institutional resistance to complaint and redress. This AI-assisted content is scripted, symbolically congruent, and contemporaneous with private events with remarkable accuracy, and is predominantly delivered via algorithm on prominent social media platforms (YouTube, TikTok).
These post swarms closely mirror litigation milestones and private events as is noted in the Guide (here). One such example also reflected in a NS public health record on May 13, 2023. That event is outlined in the previous section above. The AI-generated imagery and language between the YouTube post and the NS Health record are exactly identical, with timestamps within minutes of each other. The likelihood of coincidence, especially paired alongside the entirety of the file, is near zero. May 13, 2023 event was unannounced and unexpected.
B. Pattern of Institutional Foreclosure
Legal system:
-
$400,000 solicitor-client billing certified for 14.45 hours (~9,000% markup)
-
Entire file sealed, including previously public PSYOP visuals, prior to hearing
-
Procedural foreclosure and omission of probative record (prima facie shareholder fraud)
-
Obstructive mechanisms departing from rules and binding authorities
-
NS Court published false chronology atop a sealed file
Law enforcement:
-
RCMP adopted preemptive mental health framing
-
RCMP apologized for a negligent response in 2021/2022 in BC, but made no corrective steps and did not acknowledge online crimes
-
HRP published false reports despite identifying actors and evidence in a recorded meeting
-
Family-adjacent operator (proximate; sworn evidence) omitted from reports
-
Declinations persisted despite documentary relevance and accessibility, and treated as "harassing communications"
Regulatory/oversight:
-
Law Societies (BC, NS) declined oversight; Canadian Judicial Council declined review
-
Ombuds (NS, BC) non-responsive / jurisdictionally declined
-
Police regulators shielded misconduct and negligence
Cumulatively, every “exit” route became financially, procedurally, or psychologically prohibitive—a practical inescapability. All of this is documented.
C. Architecture of Targeting
-
High-volume, thematically coordinated content appearing within hours, and sometimes minutes, of private or sealed events
-
Family-adjacent actor (nephew’s biological mother; “MyFatherIsJoy”) delivering personalized spiritual/moral messaging
-
Algorithmic amplification: attempts to monitor/research produced further exposure
-
Legal/financial/psychiatric measures signaling non-credibility to third parties
-
Biometric indicators / real-time alignment: content matching non-public clinical notes, court events, and private conversations
The net effect: the subject’s informational and institutional environment became a continuous threat field. Conclusion: When PSYOP architecture and institutional foreclosure converge over years, the resulting harm profile tracks what the neuroscientific and clinical literatures predict: durable alteration with no realistic restoration pathway.
IX. LEGAL AND ETHICAL IMPLICATIONS OF IRREPARABLE HARM
A. Torture Law: Psychological Operations as Cybertorture
The CAT prohibits intentional infliction of severe physical or mental pain or suffering for prohibited purposes where public officials are involved directly, indirectly, or through acquiescence. The Special Rapporteur has recognized technology-mediated psychological coercion as cybertorture.
Where state-adjacent PSYOPs yield documented, lasting neurobiological and psychological injury (e.g., hippocampal atrophy, network alterations, CPTSD), the severity and intentionality elements are met; state involvement can be shown via direct operation, outsourcing, facilitation, or knowing toleration of private systems that predictably inflict such harms.
Key finding: Operations producing permanent brain changes and irreversible CPTSD **meet—and aggravate—** UN cybertorture thresholds due to the permanence of harm.
B. Charter Section 7: Security of the Person
Section 7 protects life, liberty, and security of the person, including serious state-caused psychological harm (e.g., Blencoe; G.(J.)).
Permanence heightens engagement: transient distress may not suffice; permanent impairment (analogous to permanent physical injury) squarely engages s. 7.
Principles of fundamental justice require:
-
Proportionality of state action;
-
Non-arbitrariness in deprivations (e.g., any psychiatric intervention must be evidence-based);
-
Procedural fairness (institutional foreclosure and opaque algorithmic attribution defeat fair hearing).
State-adjacent PSYOPs that cause permanent neurobiological damage breach s. 7 substantively; algorithmic opacity plus systemic foreclosure compound procedural breaches.
C. Proportionality and the Absence of Justifiable Objectives
Under Oakes, a rights limit must have a pressing objective, rational connection, minimal impairment, and proportionate effects. No legitimate objective justifies permanent brain injury:
-
National security / public safety: target is a civil litigant, not a violent threat.
-
Deterrence / institutional protection: neither justifies irreversible cognitive harm.
-
Minimal impairment fails: behavior change, neutralization, or information control can be pursued by non-permanent means (court orders, sealing, narrow restrictions).
-
Overall proportionality fails: permanent injury to one person vs. speculative institutional benefits; lifetime psychological torture vs. administrative convenience
Conclusion: State-adjacent PSYOPs causing permanent harm are per se unconstitutional under the proportionality analysis.
D. Remedial Breakdown: When Restoration Is Impossible
Conventional remedies presuppose reparability. Here, they don’t:
-
Damages cannot buy a new hippocampus, restore DMN–CEN connectivity, or rebuild erased social capital.
-
Injunctions issued after years arrive too late to reverse structural injury.
-
Declarations vindicate rights but do not heal cognitive autonomy or eliminate hypervigilance.
-
Structural reforms protect future victims but do not restore prior function.
Because restoration is unattainable, prevention is the only adequate legal-ethical response: categorical prohibition of state-adjacent psychological operations that produce permanent harm, coupled with accountability for operators and enablers.
X. CONCLUSION: THE NORMATIVE CASE FOR CATEGORICAL PROHIBITION
Contemporary neuroscience and clinical psychology recast modern state-adjacent PSYOPs as engineered pathways to chronic, life-shaping injury. AI-assisted influence systems reliably create inescapable threat, betrayal, isolation, and institutional abandonment—conditions that drive neurobiological and psychological trajectories from which current interventions cannot restore prior baselines.
The evidence establishes:
-
Neurobiological permanence: hippocampal volume loss, network-connectivity alterations, stress-system dysregulation, and sensitization/kindling—measurable, documented, and treatment-resistant.
-
Psychological chronicity: CPTSD with identity fragmentation, affect dysregulation, and durable relational impairment—manageable but not reversible.
-
Social irreversibility: reputation collapse, professional annihilation, familial rupture, and civic exclusion—network effects and digital permanence preclude reconstruction.
-
Democratic incapacitation: cognitive impairment, epistemic helplessness, hypervigilance, and loss of functional citizenship.
The UN cybertorture framework (A/HRC/43/49) recognizes technology-mediated coercion meeting severity, intentionality, prohibited purpose, and powerlessness as torture—“severe mental suffering while avoiding the conduit of the physical body”—making such harm easier to deny yet potentially more destructive. PSYOP doctrine explicitly designs learned helplessness, identity attack, isolation, continuous retraumatization, and institutional foreclosure, i.e., conditions known to produce permanent injury. AI systems amplify this through closed-loop biometric optimization, content-farm saturation, coordinated influencer vectors, personalized adaptation, and indefinite duration.
The case study shows these are operational realities: multi-year targeting well beyond recovery windows; sub-24-hour convergence evidencing real-time awareness; family-adjacent operators creating attachment trauma; dozens of synchronized channels; and multi-agency foreclosure yielding practical inescapability with psychiatric weaponization pre-discrediting complaints.
Four conclusions follow:
-
Torture machines: When these characteristics converge, psychological operations meet—and aggravate—cybertorture thresholds by inflicting permanent harm with operational efficiency.
-
No proportionality defense: Irreversible brain injury, chronic psychological damage, social death, and democratic incapacity admit no legitimate justification; prevention, not mitigation, is the only adequate response.
-
Qualitative escalation via AI: The shift from purely human-facilitated PSYOPs to AI-optimized systems exacerbates scope and capacity.
-
Qualified non-restorability: Current treatments can substantially reduce symptoms—and sometimes achieve remission—but after prolonged, interpersonal, multi-year exposure, full return to pre-trauma baseline is uncommon. Assuming they receive adequate support, most survivors improve toward a changed baseline with residual vulnerabilities.
Normative imperative: Systems that foreseeably drive targets into chronic trauma, social death, and democratic incapacity must be categorically prohibited—not merely regulated or overseen. Deploying them is a crime against personhood: an assault on cognitive function, psychological integrity, social identity, and civic capacity.
ANNEX: KEY MEDICAL AND SCIENTIFIC REFERENCES
Neurobiological Studies
[^1]: Metzak, P.D., et al. Multiple imaging studies of torture survivors and chronic PTSD populations documenting hippocampal volume reduction
[^2]: "Mean left hippocampal volume for the TR-PTSD group was significantly lower than in the HV [healthy volunteer] group" (p < 0.001); Gray matter volume reductions and diffusion-weighted imaging abnormalities in frontal and occipital lobes
[^3]: Traumatic events followed by "critical period of increased brain plasticity, during which irreversible neuronal changes may occur in those who develop PTSD"
[^4]: Functional MRI studies of torture survivors years after exposure showing abnormal coupling between default mode network (DMN), central executive network (CEN), and salience/attentional networks
[^5]: "Increased CEN-DMN dynamic functional connectivity" with "emotional rigidity, inflexibility, withdrawal, problems with self-regulation and difficulties responding to positive interpersonal situations"—observed mean 10.53 years post-exposure
[^6]: "Reduced connectivity in posterior default mode network (left precuneus region) and auditory-motor network (right superior temporal gyrus region)"; "torture exposure itself may therefore fundamentally alter the way intrinsic networks of the brain—in particular the CEN and DMN—function and connect"
[^7]: Neuropeptide Y (NPY) levels "significantly lower in male veterans with chronic PTSD"; neuroendocrine changes persist chronically
[^8]: "Increasing allostatic load associated with PTSD" manifesting in "chronic musculoskeletal pain, hypertension, hyperlipidaemia, obesity and cardiovascular disease"
[^9]: "The mechanism that causes the progressive escalation of symptoms with the passage of time leading to delayed onset post-traumatic stress disorder (PTSD) involves the process of sensitization and kindling"
[^10]: McEwen, Bruce. "Some changes are reversible," but under prolonged stress "the brain is never the same as it was before"
[^11]: Reisner, Steven. "Psychological torture undermines the very ability to think, and it doesn't leave any marks"
Complex PTSD and Trauma
[^12]: Complex PTSD develops following "chronic (long-term) trauma" involving "repeated trauma experienced by a child or young person, although it can also occur as a result of experiences as an adult"
[^13]: CPTSD involves "additional symptoms, such as: persistent difficulties in sustaining relationships" and fundamental disruptions in self-concept
[^14]: Complex trauma as "(i) trauma that involved (ii) multiple events which were (iii) interpersonal assaults or threats"; "interpersonal traumatization causes more severe reaction in the victim than does traumatization that is impersonal"
[^15]: "About 3 out of 100 adults (or 3%) had current PTSD, and about another 4 out of 100 adults (or 4%) had complex PTSD" in U.S. population
[^16]: Complex trauma creates "alterations in the sense of self," including "unstable self-structure sense of self"
[^17]: Herman, Judith Lewis (1990s frameworks); one person may experience severe trauma with minor symptoms while another experiences single event with large changes—determining factor is interpersonal, inescapable nature
[^18]: Complex trauma produces "alterations in the regulation of affective impulses, including difficulty with modulation of anger and of tendencies towards self-destructiveness"
[^19]: "These events often involve other people harming you, they can make it hard to trust or relate to other people"
[^20]: Complex trauma generates "relational instability" and "alterations in relations with others, including isolation and withdrawal, disturbances in attachments, and difficulty sustaining relationships"
[^21]: Research on children experiencing complex trauma documents "increased risk of self-harm, suicide, and poorer educational attainment" alongside relational difficulties
[^22]: "Trauma-focused treatments, which are the most effective for PTSD, also treat complex PTSD," but "it may be that once PTSD has been treated, some other concerns (such as depression or relationship health) still need to be addressed"
[^23]: "There remain many gaps in evidence as to what constitutes the most effective form of help for children who have experienced complex trauma"
[^24]: "People can and do recover from complex trauma and its effects," "it is never too late"—yet recovery means "holding onto the hope of recovery" and developing coping strategies, not restoration
UN Cybertorture Framework
[^25]: Melzer, Nils. "Psychological torture and ill-treatment." UN Doc. A/HRC/43/49 (20 March 2020)
[^26]: A/HRC/43/49, para. 19: "Psychological torture" interpreted to include "all methods, techniques and circumstances which are intended or designed to purposefully inflict severe mental pain or suffering without using the conduit or effect of severe physical pain or suffering"
[^27]: A/HRC/43/49, para. 75: Harassment "can expose targeted individuals to extremely elevated and prolonged levels of anxiety, stress, social isolation, and depression"
[^28]: A/HRC/43/49, para. 72: "Cybertechnology can inflict severe mental suffering while avoiding the conduit of the physical body"
[^29]: A/HRC/43/49, para. 72: "States, corporate actors, and organised criminals not only have the capacity to conduct cyber-operations inflicting severe suffering on countless individuals, but may well decide to do so for any of the purposes of torture"
[^30]: A/HRC/43/49, para. 40: Powerlessness arises when someone has "effectively lost the capacity to resist or escape the infliction of pain or suffering"
[^31]: A/HRC/43/49, para. 40: Powerlessness "can further be achieved through 'deprivation of legal capacity,' through serious and immediate threats, or through coercive control in contexts such as domestic violence, through incapacitating medication and, depending on the circumstances, in collective social contexts of mobbing, cyberbullying and State-sponsored persecution"
[^32]: A/HRC/43/49, para. 33: Severe "mental suffering" can be reached "not only through subjectively experienced suffering but, in the absence of subjectively experienced suffering, also through objectively inflicted mental harm alone"
Psychological Operations Doctrine
[^33]: United States Senate Select Committee on Intelligence, Committee Study of the Central Intelligence Agency's Detention and Interrogation Program (2014): CIA program sought "learned helplessness"
[^34]: Center for Victims of Torture: "Torture is the deliberate and systematic dismantling of a person's identity and humanity"
[^35]: A/HRC/43/49, para. 56: "Isolation and sensory deprivation risk a host of psychological harms" by encouraging "dependence on the interrogator"
[^36]: A/HRC/43/49, para. 47: Detainees "kept in total darkness"; "mock executions" leaving them "feeling they were already dead"
[^37]: Başoğlu, Metin: "The underlying principle that makes torture so traumatic is the individual's loss of control"
[^38]: Başoğlu, Metin: "Threat or anticipation of pain may be worse than the pain itself"; "deceptively banal mistreatments" become devastating when combined
Automated Systems
[^39]: RAND Corporation, "The Russian 'Firehose of Falsehood' Propaganda Model" (2016): "High-volume and multichannel" plus "rapid, continuous, and repetitive" messaging creates "uncertainty, paralysis, and disengagement"
"A Widespread Phenomenon"











