Crimes Against Humanity and War Crimes Act (S.C. 2000, c. 24) [Link]
4IR Portal
A Web Information Aggregate [J.N. v. C.G., 2022 ONSC 1198 at Paragraph 48]
NBIC Nanotechnology | Biotechnology | Information Technology | Cognitive Science

FOUR Years
of oppression facilitated by state contractors involving neurotech crimes in support of private commercial interests, and a Federally-sponsored litigant implicated in a shareholder scandal.
FOUR Vectors
[1] Relentlessly stalked, harassed, threatened, and surveilled through PsyOps, IO, and apps (here), [2] plundered through a half-million-dollar court scandal (here), [3] consistently denied access to justice and safe avenue (here), and [4] positioned as an offender and/or a nuisance when seeking the latter (here).
THREE Avenues
Relief and safe avenues consistently blocked in [1] courts, [2] police agencies, and [3] regulators, with all three being weaponized against their mandates.
ONE Scandal
leveraging Canadian institutions and authorities to facilitate private commercial interests involving Biodigital Convergence (defined here).
ONE Solution
Whistleblowers, Accountability, and Restitution for Victims.
UN Findings & Recognition: A/HRC/57/61 & A/HRC/58/58, UN Resolution A/HRC/RES/58/6.


Neurotech Crime Impacts a Lawsuit
Understanding this Web Page.
Read this Carefully.
Per my Testimony, I submit I was, and am, the victim of a neurotech crime, which was leveraged to support a commercial and government entity ("CAGE") in the lawsuit referenced (here). AI-Assisted cyber torture has accompanied this effort (here). My biometric data is available to specific actors in the dark web, and is used as a harassment tool and a means to surveil. My objective in this page is not to provide a complete evidentiary record. Rather, by way of an exploration of concrete milestones, visual evidence, information from credible sources, and inferences guided by the test criteria in Sherman Estate v. Donovan, 2021 SCC 25, [2021] 2 S.C.R. 75 at paragraphs 97-98, I aim to demonstrate the merit in this disclosure, and that the feasibility of alternative explanations to the scandal detailed on this website is vitiated to the point of inadmissibility.
Concerning the Presentation Format.
Quoting the Federal Court of Canada, the Ontario Supreme Court recognized the admissibility of information obtained through websites in J.N. v. C.G., 2022 ONSC 1198 at Paragraph 48;
“Information obtained from the internet can be admissible if it is accompanied by indicia of reliability, including, but not limited to;
-
Whether the information comes from an official website from a well-known organization;
-
Whether the information is capable of being verified;
-
Whether the source is disclosed so that the objectivity of the person or organization posting the material can be assessed.”
I affirm that the online articles quoted and visually excerpted on this website are sourced unchanged from the originals, and amalgamated in a manner that allows the unbiased reader to glean meaningful relations. The machine-assisted outputs on this page, although reliable, are intended to assist readers in understanding the subject matter. The source case law at ITV Technologies Inc. v. WIC Television Ltd., 2003 FC 1056 at paragraphs 13 & 18 is applicable as follows, as is the remainder of the case law concerning admissibility;
“In my view, when considering the contents of a web site, the original is found on the Internet and provides better evidence than a print copy. The Court was able to see the documents as they existed on the Internet, and could witness such features as hyperlinking and interactive streaming that could not have been realistically reproduced on paper. [...] As for unofficial web sites, I accept Mr. Carroll's opinion that the reliability of the information obtained from an unofficial web site will depend on various factors which include careful assessment of its sources, independent corroboration, consideration as to whether it might have been modified from what was originally available and assessment of the objectivity of the person placing the information on-line.”
The Topic.




Explored in a Non-Technical Manner.

The Effect (Reading).


The Effect (Writing).


Micro-RAMAN, SEM-EDX, and TEM Nanoparticle Testing Must Be Conducted. See the Tests [Here].




Working Definitions
What is a Neurotech or "Cognitive Liberty" Crime?
Cognitive Liberty Crime Defined.
Crimes that affect a person’s cognitive liberty are recognized under UN General Assembly Resolutions A/HRC/RES/51/3 (here) and A/HRC/57/61 (here), and are described in greater detail in the Appellant’s website Testimony (here). The issue has recently attracted the interest of Time Magazine and the Harvard Gazette, among the scores of similar publications quoted at the bottom of the page.
Per the UN General Assembly’s definition in A/HRC/57/61 at paragraph (5);
“Neurotechnologies are unique and socially disruptive because they generally: (a) enable the exposition of cognitive processes; (b) enable the direct alteration of a person’s mental processes and thoughts; (c) bypass the individual’s conscious control or awareness; (d) enable non-consensual external access to thoughts, emotions and mental states; (e) are nurtured by “neurodata”, which are needed for their own functioning, calibration and optimization; and (f) collect, analyse and process large personal datasets of a highly sensitive nature.”
UN Special Rapporteur Ana Brian Nougrères outlined neurotech crimes in the adjacent UN article, alongside neuroethicist Dr. Nina Farahany below, and WEF keynote Dr. Yuval Noah Harari below right.



The Government of Canada has Massive Interest in BCI Technologies [Here].

How Would, or Could, the Existence of a Cognitive Liberty Crime be Discerned?
In the Absence of Whistleblower Testimony;
There are three key components that can inform a reasonable inference guided by the test criteria in Sherman Estate v. Donovan, 2021 SCC 25, [2021] 2 S.C.R. 75 at paragraphs 97-98;
“This Court has held that it is possible to identify objectively discernible harm on the basis of logical inferences (Bragg, at paras. 15‑16). But this process of inferential reasoning is not a licence to engage in impermissible speculation. An inference must still be grounded in objective circumstantial facts that reasonably allow the finding to be made inferentially. Where the inference cannot reasonably be drawn from the circumstances, it amounts to speculation (R. v. Chanmany, 2016 ONCA 576, 352 O.A.C. 121, at para. 45) [...] Where the feared harm is particularly serious, the probability that this harm materialize need not be shown to be likely, but must still be more than negligible, fanciful or speculative.”
The first component involves extreme behavioural outliers as measured against my BIO, and a lifetime of consistent baseline behaviours.
The second component involves a sophisticated criminal group that uses biometric data as a vehicle of harassment and a mode of surveillance, such as the examples shown on the Guide page.
The third component involves a four-year event chronology detailed at the Affidavits page, and shown through the blog contents (here). It features the same organized criminal group, a shareholder scandal, a scandal concerning adjudicative agencies and police, and detailed information exhibits concerning the Fourth Industrial Revolution (“4IR”) and associated technologies. Each of these intertwined matters are compelling in their own right, and occasion the existence of a compelling project interest.
I submit my cognitive liberty was initially compromised in February 2021, following what can best be described as an anomalous health incident. A second anomalous health incident occurred in January 2022 while viewing content by the online criminal cohort on my smartphone. Following a countdown (3...2...1...!), I experienced an acute sensation that resembled an “air puff” test that one might experience at an eye doctor (non-contact tonometry). An eye exam on September 25th, 2023 revealed novel anomalies in my retinas which were not present in previous tests.
Alongside a reasonable inference of cognitive tampering that affected my decision-making, it is understood that bad actors have had access to my biometric data in the dark web at least since the same 2021 event, though the Testimony contains relevant insights dating back to 2013.
How Did The Behavioural Outliers Manifest?
In Ways That Preclude Any Other Reasonable Explanation.
In July 2021, I listed my home for sale, packed my bags, and relocated to BC in further support of the 2021 shareholder dispute with the CAGE, regardless of the fact that I had previously retained a BC law firm to remotely manage the matter on my behalf. I am not at all given to disproportionate extremes such as these, which were entirely unnecessary, dangerous, and utterly absurd in view of the circumstances at that juncture. Those familiar with me would suggest I am often loath to drive across town to attend a function I enjoy, let alone drive across the country to pursue a legal matter that is expected to be managed by a law firm in that same area, and list my dream home for sale on MLS. Furthermore, I am not easily shaken by new and upsetting circumstances.
I had worked for years to develop my personal real estate, which was at that time fully paid for and renovated. I had two motorcycles in the garage, a specialty sports car in the driveway, an exotic pet, and a robust bank account by my standards. That required a lot of time and effort to achieve, and I did it through discipline and smart choices over a number of years. The CAGE Director would in fact characterize me in the same fashion, having worked with me for four years, as he had stated in a recommendation letter (an Affidavit sworn January 9th, 2025 at Exhibit F). Because the law firm I retained in BC could have handled the matter while I remained in Nova Scotia, there was no merit nor value in the excursion, or the home sale. On arrival in BC in late July 2021, I remained in a Condo rental from August through October while coordinating with the law firm on the shareholder dispute. My home sold in late September that year. Following the close of the settlement, I drove back to Nova Scotia from British Columbia by car to reside with my Mother.
It gets worse. Two weeks following my return to Nova Scotia, during the first week of November 2021, I found myself once again driving to British Columbia. I had no distinct plan in mind; only that I was under the impression that the shareholder matter remained unresolved, and that I had to return to BC again in person to address it. Having said that, I made no plans nor preparations to visit the court, as I stated in an Affidavit I had sworn on May 20th, 2022. I arrived in Surrey, BC on November 10th, 2021 to a condo I had rented on Craigslist. It was shortly after that that the "diffuse & disrupt" events as described in the Testimony and Q/A pages began in earnest. To reiterate, I signed a one-year lease without a vision, without any income, and drove across Canada again (coast to coast) after emerging from a perilous shareholder dispute. That is about as far removed from my typical baseline behavioural scheme as ice is to fire, and is just as absurd as the adjudicative concurrence detailed in the civil proceedings (here). Bank records detailing these excursions across Canada are shown (here).
I submit that these actions would not have occurred were my cognitive liberty intact. Prior to the onset of these events, I had lived quietly my entire life and had focused on the career I had nurtured through my skill-set in enterprise sales. I have no criminal record, I was never in debt, and I have avoided bad decisions that lead to destructive outcomes. I am careful by nature, and I avoid conflict where possible. Ultimately, if a person has a tendency to make reckless decisions with their life and money, they would have had to have won the lottery to achieve what I did through hard work, patience, and discipline over many years. Investigators will recognize that the behavioral outliers do not add up (Canada (Minister of Citizenship and Immigration) v. Vavilov, 2019 SCC 65, [2019] 4 SCR 653 at paragraph 104).
It should likewise be noted that I had maintained amicable relations with the CAGE entity following the end of a four-year business engagement in December 2019 due to the strategic value perceived in doing so, as I had with the numerous other business contacts I had worked with over the course of a fifteen-year career. I had in fact developed a new venture with him following a project that ended in May 2018. Being a practical person, I do not mix business with my personal life, nor do I allow setbacks to change the guiding parameters that govern my decision-making.
Can You Show Examples of Surveillance?
Occurrences Like These Require a Proximate Data Stream.
The Guide page contains further examples beyond these three shown below, with a detailed analysis. I did not create this or any content.





Milestone Events are Always Referenced. Examples: (1) Retainer Fee Scandal, (2) Bank Account Freeze.


The CAGE Panicked When 4IR & Related AI-Assisted Mischief Was Sworn into an Affidavit.

What Law Firm Would Threaten to Strike a Petition Shortly After an Order for Forensic Audit..?
Context: Per the account at the Civil page, I had sworn an account of the events between November 2021 and March 2022 in an Affidavit on May 20th, 2022, and sent it via courier to a BC process-serving agency. These events concerned the related criminal element that compelled the filing of S-220956 (here). A few weeks prior, the BCSC issued an order to seek forensic discovery of the shareholder records (here). While the Affidavit was still enroute (I had not informed anyone), the CAGE threatened to strike S-220956. Such a motion would be doomed to fail following the discovery order. There are many such examples germane to surveillance.




The AI-Assisted Cohort Rejoiced Over the Petition Dismissal. Further Milestones [Here]

Who Might the Perpetrators Be and What Might be Their Motivation?
The Effects are Disproportionate to the Interests & Capabilities of the CAGE Alone.
While a retaliatory hate crime in response to a shareholder dispute with the Director of a federally-sponsored Commercial and Government Entity ("CAGE") is feasible as an initial consideration, and whereas the criminal element in question has made references to the same, the scope of the scandal involved is disproportionate to the commercial interests of a small to mid-sized company. Under normal circumstances, the CEO of a mid-sized company could not emerge from a legal battle involving filed proof of shareholder fraud, perjury, and collusion with a $400,000 paycheque; nor could any litigant without significant third-party assistance. Third party assurances are demonstrated in the scandal involving retainer fees alone, 737.7 hours vs. 9 short-chambers motions, as shown in the CAGE Affidavit and BCSC Clerk's Notes here. A reasonable litigant would not agree to that scope of retainer; a reputable law firm (Canada's 4th largest) would not propose it; nor would an unbiased adjudicator certify and/or enforce it. Yet all of those boxes were ticked. That inexorably requires an assuring stakeholder positioned to influence the conduct of the agencies involved; a project interest to justify the risk and coordinate the effort; and a unifying narrative to sell the value of consistent and continued participation among the same persons and entities. In this context, the CAGE represents a peripheral interest as an accomplice to the sponsoring interest. These are compelling thresholds. It raises serious questions regarding circles of influence in Canada, which are decidedly post-democratic in character as is evidenced by the effects shown. As Dr. Klaus-Gerd Giesen comments below, biodigital convergence projects are driven by robust commercial interests. It would be presumptuous to assume that I am the only victim of such crimes.
It's Driven by Commercial Interests.
Transhumanism as the Dominant Ideology of the Fourth Industrial Revolution
By Klaus-Gerd Giesen, Translated and edited by Cadenza Academic Translations
Translator: Ruth Grant, Editor: Matt Burden, Senior editor: Mark Mellor Pages 189 to 203
“Transhumanist thought can be broken down into three main premises, each with an eminently political intent: Human beings in their ‘natural’ state are obsolete and ought to be enhanced by technology, which then becomes a means of artificially extending the hominization process. Thus, transhumanism sweeps human taxonomy into the political arena. An observation by Michel Foucault, written in 1976, comes to mind: ‘What might be called a society’s threshold of modernity has been reached when the life of the species is wagered on its own political strategies. Modern man is an animal whose politics places his existence as a living being in question.’ In other words, transhumanists believe we have a duty to replace the category of human with a new creature, a post-sapiens sapiens.” [...] “Transhumanist ideology is driven by certain factions within the state and, above all, by mighty multinational corporations that, it is fair to say, have the most to gain from seeing the NBIC revolution unfold without a hitch. In this respect, transhumanism is already a dominant ideology, as it crushes all other ideological positions regarding technological change — particularly those of humanists of all stripes and subscribers to “deep ecology” — under the sheer weight of money. [...] These tech giants have already poured staggering amounts of money into the fourth industrial revolution and are currently spending equally eye-watering amounts on political lobbying and social engineering initiatives. [...] There is every reason to fear that the world will launch into the fourth industrial revolution without too much debate over what is waiting in the wings: the global political project that is transhumanism. Today, it is as if the metamorphosis, via the “NBIC Great Convergence,” to a posthuman being, technologically enhanced and fully integrated with the machine, were already written in stone.”
A Typical Bitcoin Mining Rig Requires 1,000 Watts of Power While Running [link]. The Human Brain Only Requires 12.

Supplemental to the Testimony Page [Here]. Neurotech Crimes are a Reality.







It's Driven by Ideological Interests.
Value(s): Building a Better World for All [Link]
Prime Minister Mark Carney, 2021, ISBN 0008485240, P. 36, 95, 494
“Moral sentiments are not inherent. To use the modern terminology of Richard Dawkins, they are social memes that are learned, imitated and passed on. Like genetic memes, they can mutate, in behavioural cascades and tipping points."
“Magna Carta was a desperate and probably disingenuous attempt at a peace treaty that failed almost immediately. Brokered by the Church, and issued by King John in June 1215, the Charter sought to placate the disgruntled barons. [...] If Magna Carta was such a product of its time, how did it become to be so venerated? And once we cut through the legend, what is its significance for economic governance today?"
"The world is being reset. Now we are on the cusp of what some have called a Fourth Industrial Revolution (4IR). Applications of artificial intelligence are spreading due to advances in robotics, nanotechnology and quantum computing. Our economies are reorganising into distributed peer-to-peer connections across powerful networks – revolutionizing how we consume, work and communicate. Solidarity will determine the success of the 4IR, where the need for new institutions that live the value of solidarity is the greatest.”



Dr. Colin Crouch, Post Democracy, 2004, ISBN 0-7456-3315-3
Applicable Tests
Sherman Estate v. Donovan, 2021 SCC 25, [2021] 2 S.C.R. 75 at paragraphs 97-98 | Canada (Attorney General) v. Bedford, 2013 SCC 72 (CanLII), [2013] 3 SCR 1101 at paragraph 76 | R. v. Ahmad, 2020 SCC 11, [2020] 1 S.C.R. 577 at paragraph 38 | R. v. Wise, [1992] 1 S.C.R. 527 at paragraphs 534-538 | Nova Scotia Teachers Union v. Nova Scotia (Attorney General), 2023 NSCA 82 at paragraph 7 | Charkaoui v. Canada (Citizenship and Immigration), 2007 SCC 9 (CanLII), [2007] 1 SCR 350 at paragraphs 22, 23, & 27
Among its Lesser Known Modalities, 4IR Concerns Connecting Human Bodies to the Internet.
An Industrial Revolution is a Society-Changing Milestone.
Discussion of 4IR is muted due to it's controversy. This fact must be mated to its prevalence among stakeholder communities. The archived UN Decade of Action publication, posted in 2020 but deleted in April 2025, lists the media as a stakeholder partner as opposed to an independent news source. This is shown below with highlighted text. Given Dr. Giesen's research publication and the data underpinning 4IR, and its controversy, it stands to reason that signal change may be introduced through disruptive events. Pay attention! See further analysis (here).




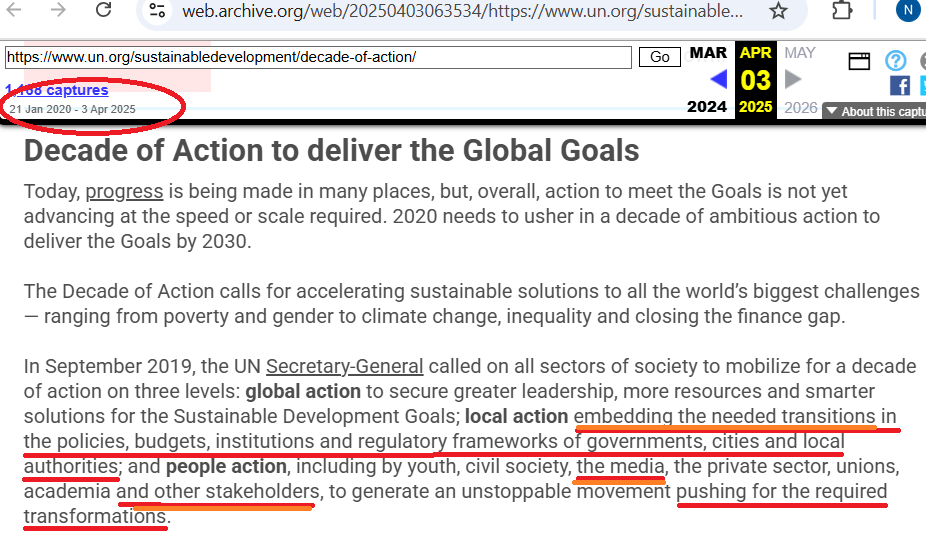









He's Right; The Canadian Government Would Not Be As Transparent.


Might a Discreet Brain-Computer Interface Used in Neurotech Crime Seem Sensational?
Not in Our Day. Execution is Easy For Sophisticated Actors Who Now Have the Tools.
A capability for remote neurotech crime that can impact a subject’s cognitive liberty is readily available to sophisticated actors. A sophisticated actor could compromise the outcome of a legal proceeding through the manipulation of neurodata and it would be very difficult to prove. Depending on the scenario, the litmus test would reside in the case law. With respect to this scandal, one need only look at the massive disparity between the filed court records and the disposition of the proceedings, the hundreds of legal tests that were violated to facilitate the outcomes that occurred, and the behavioural outliers cited earlier.
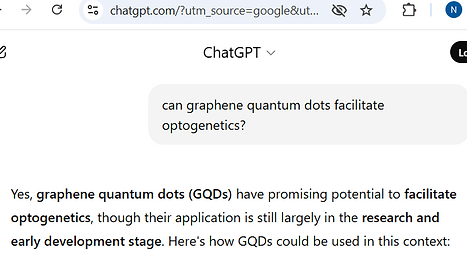
With respect to enablement vehicles, Graphene Quantum Dots (“GQD”), crystalline nanoparticles that are often less than two (2) nanometers in diameter (here), can achieve a remote brain-computer-interface (“BCI”). These biocompatible particles, introduced via injection or inhalation, can cross the blood brain barrier. The most capable research MRI scanners can parse nanoscale particles 5.6 nanometers or larger (here), whereas clinical scanners are nowhere near that capability. Remote BCI interfaces have been researched since the 1990s;
“In order to realize the fullest potential of BCI, we need a system that 1) transmits data wirelessly, 2) does not rely on surgical installation, 3) maintains the proximal contact between nerve tissue and material required for efficient transfer of energy and information, and 4) can both stimulate and record neural activity (or bidirectional capabilities). To bridge the gap between invasive and non-invasive technologies, nanoscale materials, such as biocompatible nanoparticles, provide a promising alternative, allowing us to design materials at the scale of cellular systems and structures. [...] Using nanoparticles as antennae in the brain is a concept that has enjoyed extensive study in academic laboratories over the past 15 years. The vast majority of this work has focused on using nanoparticles for neuromodulation.”
https://medcitynews.com/2025/02/biocompatible-nanoparticles-tiny-antennae-with-huge-potential-for-brain-computer-interfaces/
The technology has advanced to the extent that an off-the-shelf Android phone can act as an EEG device (transmission node), and that is just the technology we are aware of;
“Significance: We present a fully smartphone-operated, modular closed-loop BCI system that can be combined with different EEG amplifiers and can easily implement other paradigms.”
https://pubmed.ncbi.nlm.nih.gov/29349070/
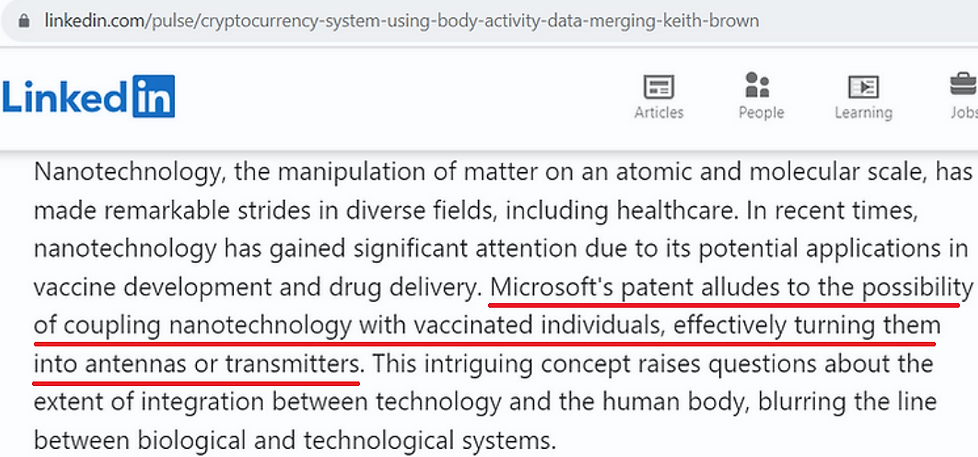
The deleted Linkedin article below, concerning Microsoft patent WO2020060606, enables such connectivity to mine cryptocurrency using biometric (body) data. The utility is obvious, as cryptocurrency mining requires an extremely onerous and costly energy expenditure. While a typical bitcoin mining rig requires over 1,000 watts of power to operate, the human brain can yield the same results using just twelve (12) watts, without incurring a power bill;
“Nanotechnology, the manipulation of matter on an atomic and molecular scale, has made remarkable strides in diverse fields, including healthcare. In recent times, nanotechnology has gained significant attention due to its potential applications in vaccine development and drug delivery. Microsoft's patent alludes to the possibility of coupling nanotechnology with vaccinated individuals, effectively turning them into antennas or transmitters. This intriguing concept raises questions about the extent of integration between technology and the human body, blurring the line between biological and technological systems.”
https://archive.ph/FfOVM
The Graphene Quantum Dot ("GQD") is a Discreet Enablement Vehicle for Neurotech Crime.

















"And it hath come to pass, at that time, I search Jerusalem with lights, And I have laid a charge on the men Who are hardened on their preserved things, Who are saying in their heart: Jehovah doth no good, nor doth He evil." - Zephaniah 1:12




As Noted at the Top, a GQD System is Consistent With the Observed Effects.




There are no Foundational Beliefs Held by Stakeholders That Would Preclude Human Experimentation.
Their Words, Not Mine.
Since 2022 when these crimes became apparent, I availed myself to begin researching the musings and publications germane to the subject matter. In doing so, my objective was to determine if a predominant corpus of beliefs and aspirations could be identified, and the results are compelling. A collection of quotes are shown below on this page to that effect, with further visuals below and in the testimony (here). A predominantly postmodern hermeneutic is explored at the Politics page (here), which sets the stage for an ideology that presumes the acceptability of introducing human taxonomy as a talking point in sociopolitical think tanks such as Policy Horizons Canada. A postmodern outlook assumes truth is subject to human consensus, that the physical world can encapsulate the entirety of meaning, and that the onus is solely on humanity to engineer its destiny. An assumption is made that many of the social challenges can be remedied through genetic or biodigital adaptations. Below, former Y-Combinator CEO Geoff Ralston suggests "toxic" persons can be fixed with gene therapy. Dr. Yuval Harari's comments on "digital dictatorships" are noteworthy, as a transition to a biodigital future need not hinge on the ideological preferences of a ruling class, but will invariably emerge as a result of innovations in data-processing systems. You won't hear about that on six o'clock news.






Asking Intelligent Questions
Are Adjudicators, Law Enforcement Officials, and Regulators Exposed to Cognitive Tampering?
Five Years, Five Courts, Three Police Agencies, & Regulators Yield Results That Defy Logic.
The overarching phenomenon in the scandal detailed on this website concerns a concurrence of behaviour among adjudicators and stakeholders in the public service, including law enforcement. Earlier in the page and (here), I highlighted that a half-million-dollar scandal involving retainer fees concerning nine (9) short hearings must require assurances from the state to execute. No less than a dozen judges in five court venues had replicated unconstitutional effects in facilitating this felony, and two law enforcement agencies, including the RCMP, had ignored basic policing standards. The effects are severe, and whereas the effects of unaddressed crime and abuses of public authority are never limited to the immediate victims. What was it that had occasioned an alignment and consistency among stakeholders?
While it is satisfied that post-democratic conditions are required for this outcome, the severity of the scandal introduces consideration of an ethics crisis in the public service. Despite strongly-held beliefs and opinions, and despite postmodern assumptions that suggest morality is a social construct, every person has a moral code, or conscience. It may in fact be more appropriate to infer a case of cognitive tampering than assume every adjudicator involved in the 4-year scandal is corrupt to the point of moral bankruptcy. I fail to see a residual category.
Is there a cognitive liberty component at stake here affecting stakeholders and influencers (and even my 2021 counsel) in the proximate ecosystem? The scope and consistency of the record, coupled with my own experience, underscores the relevance of the question.
Stonewalled Police Support.

Extreme Adjudicative, Procedural, & Administrative Outliers in Five Courts Across Three Provinces.








1582235 Ontario Limited v. Ontario, 2020 ONSC 1279 at paragraph 27;
“In Enterprise Sibeca Inc. v. Frelighsburg (Municipality), the Supreme Court described bad faith as “acts that are so markedly inconsistent with the relevant legislative context that a court cannot reasonably conclude that they were performed in good faith.”
Is a Public Health Scandal Plausible, as an Alternative to a Public Ethics Scandal?

The Record Contents Exceed That Criteria. [Here]



Corruption is as old as the hills. But, it is the ALIGNMENT across TIME, AGENCY, and JURISDICTION that gives rise to the inference.
Important Clues From a Prominent Actor in the PsyOp Cohort. See Expanded Guide [Here]

Walking Faith's Podcast is Coded Language to a Specific Audience of Actors. Here's Why.


First Indicator: The Transcript is Antithetical to Christian Teaching.



Second Indicator: He's Not Tongue-Tied.

Third Indicator: It's a Seamless Match to the Subject Matter.















Four Years of Unnatural and Extreme Outliers that Evade Correction. Were the Adjudicators and Other Stakeholders Discreetly Nudged?
In Practical Terms, a Framework Like This was Not Built for One Project.










The Technology (and Human History) Allows Us to Consider This in Objective and Practical Terms.










A Recent Case Raised Important Considerations.
The Covid-19 pandemic invites serious questions, as many members of the medical and scientific communities had asserted. Thinking persons will recognize that there are too many problems with the Covid-19 pandemic and the mRNA Covid vaccines in their own right that might reasonably suggest the pandemic was an innocuous public health scare, and I state that in synthesizing meaningful data. As a minimum consideration, the response to the pandemic was immensely disproportionate to the effects of the ailment, which could have been addressed through a variety of readily available means. Was a BCI or IoB coupling mechanism introduced through the vaccine's lipid nanoparticles? The following links, in accord with the observations in J.N. v. C.G., 2022 ONSC 1198, as shown below them, invite intense study. Further citations are linked at the Vaccine page (here). Justice Bennett makes compelling observations in his reasons, with the only discernible error at paragraph 67(b) in that there were no bodies found concerning Residential Schools (here).
-
Health Canada was proven wrong by MIT scientists concerning mRNA Genome Entry (here);
-
The use of public funds to disseminate the foregoing false data (here);
-
Onerous and disproportionate mandates, on pain of loss and career disruption for public servants including RCMP (here), and an example concerning former NS Provincial Court Justice Rickola Brinton (here);
-
Infectious disease doctors and specialists that claim Covid-19 "looks like influenza" (here & here), with others asserting that Covid data was hyped when compared with the flu (here);
-
The Appellant’s own experience of the Covid ailment that aligned with the above medical opinions, as diagnosed on December 22nd, 2024;
-
The availability of very effective, safe, and cheap "alternative treatments" like Ivermectin, as validated through testing (here & here);
-
Skilled Doctors were penalized and/or suspended for prescribing ivermectin to treat Covid (here & here);
-
Proof the Covid-10 Vaccines contain foreign DNA fragments (here);
-
Proof that Covid-19 Vaccine mRNA integrates into the genome (here);
-
Proof of self-assembling nanoparticles in the live blood samples of vaccinated persons, revealing amyloid fibrils that "branched out like antennae" (here, here, here, here, & here);
-
Microsoft Patent WO2020060606 that enables remote connectivity by way of lipid nanoparticle injection (here);
-
A comprehensive data footprint concerning 4IR in relation to addressing social and economic challenges (here, here, here, here, & here);
-
Proof of Graphene Oxide ("GO") in Covid-19 vaccines and vials (here);
-
A demand by the FDA that the Covid-19 vaccine content data remain sealed for seventy-five (75) years (here);
-
The statements by UN/WEF Stakeholders and big commercial stakeholders concerning the 4th Industrial Revolution (compiled here);
-
Biased, prejudiced, and unscientific media coverage in opposition to credible laboratory research (one example of many here).





Health Canada Misled the Public.




Vs.




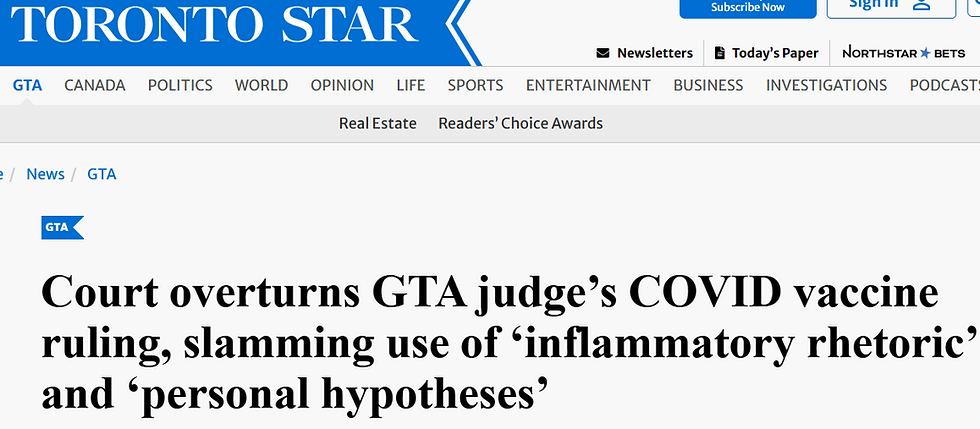
The ONSC Covid Vaccine Decision Was Quashed in the Ontario Appellate Court.
The Panel Adopted Health Canada's Advisory at Face Value.
The decision above was overturned, whereas the critique of the lower court decision, J.N. v. C.G., 2022 ONSC 1198, is worthy of mention. In addressing the Respondent's objection to the Covid vaccine in the lower court motion, justice Bennett wrote at paragraphs 61 & 62;
“The same article outlines other serious concerns about COVID vaccines expressed by Dr. Bret Weinstein, Dr. Peter McCullough, Dr. Tess Lawrie, Professor Stanley S. Levinson (medicine, endocrinology, diabetes and metabolism) and Professor Sucharit Bhakdi (awarded the Order of Merit for medical microbiology). These are well-known leaders in their fields. [...] Several other articles presented by the mother outline similar expressions of concern about the COVID vaccines from equally qualified and reputable sources worldwide.”
The Appellate panel in J.N. v. C.G., 2023 ONCA 77 wrote in response at paragraph 17;
"In my view, the motion judge fell into error by not assessing whether each document presented by the respondent was reliable, independent, unbiased and authorized by someone with expertise in the area. Instead of engaging in an analysis of the evidence presented, he embarked on a lengthy discussion about whose materials were more thought-provoking, which has no bearing at all on whether the respondent’s materials were admissible and should be given any weight."
The issue in the Panel's response is that it would ask the motion judge to step outside his lane. When conflicting scientific briefs are at stake, the standard of review is correctness, as explored through a comparative study conducted by medical researchers. The motion judge had identified the fact that the opposing documents were in fact published by qualified doctors and researchers, which is all he could have reasonably done in his role. The Appellate panel overstepped its competence through a reverse ad-hominem assertion at paragraphs 18 and 45 that Pfizer and Health Canada should enjoy judicial notice because they are better qualified to interpret the data concerning vaccine contents, and because they uphold the public interest. Per the citation pictured below this text, the FDA had sought to preclude publication of the vaccine data it had relied on to license the Pfizer Covid vaccine for 75 years, until 2096. It does not require 75 years to execute record redactions, which was the basis of the ask. The issue of course is that the matter would need to be addressed through hard science. Irrespective of that, the respondent's concerns regarding her child were nonetheless grounded in credible data that invited the reasonable restraint of the court. The SCC upheld the same restraining principle in Canada (Minister of Citizenship and Immigration) v. Vavilov, 2019 SCC 65, [2019] 4 S.C.R. 653 at paragraph 133;
"It is well established that individuals are entitled to greater procedural protection when the decision in question involves the potential for significant personal impact or harm: Baker, at para. 25. However, this principle also has implications for how a court conducts reasonableness review. Central to the necessity of adequate justification is the perspective of the individual or party over whom authority is being exercised. Where the impact of a decision on an individual’s rights and interests is severe, the reasons provided to that individual must reflect the stakes."
As it pertains to this matter, the Vaccine page highlights articles from a plethora of credible research sources such as MIT and Lund Universities that directly contradict the statements made by Health Canada. These admissions do not concern side effects that may be manageable for certain individuals, but rather, compelling findings that involve mRNA genome entry, and the existence of self-assembling nanoparticles in the blood samples of the vaccinated. The research findings show that Health Canada had misinformed the public, and spent over a half-million dollars in public funds to promote a false narrative through social influencers not unlike those at the Guide page. Likewise, the presence of graphene oxide, the "miracle material" noted earlier in the page, was "conclusive" in testing executed via micro-raman spectroscopy at the University of Almeria. The links cited in the previous section above should be explored, as they approach the matter from a variety of angles.
Might there be a public health issue at stake that is related to the scandal detailed on this website? I opine that it cannot be ruled out based on the constellation of data points available. Having said that, there is no mistaking that something was done to me personally in a manner that vitiates my privacy. Absent a whistleblower, it is unlikely I will be able to return to the life I once knew.


There is Too Much Wrong With the Covid-19 Pandemic.
The SCC in R. v. Kahsai, 2023 SCC 20 at paragraph 67, citing R. v. Wolkins, 2005 NSCA 2, 229 N.S.R. (2nd) 222, at paragraph 89, held that scandals are predominantly ascertained by way of appearance, as deduced by reasonable and objective persons having insight into their context. The test does not maintain that the observers require professional training; only that the observers be objective, rational, and informed of the circumstances.
-
Health Canada Proven Wrong by MIT Scientists;
-
The Use of Public Money to Spread False Data;
-
Onerous and disproportionate mandates, on pain of loss and career freeze for public servants including RCMP;
-
Infectious disease doctors that claim Covid-19 "looks like influenza";
-
My own experience of the Covid ailment that aligned with the above medical opinions;
-
The availability of very effective, safe, and cheap "alternative treatments" like Ivermectin;
-
Doctor licenses being revoked for prescribing ivermectin and alternative treatments;
-
The speed of production and distribution of the vaccine;
-
Proof that Covid-19 Vaccine mRNA integrates into the genome;
-
Proof of nanoparticles in live blood samples, and fibrils that "branched out like antennae";
-
A Microsoft Patent that, if employed, can and does turn vaccinated persons into "antennas or transmitters" (here);
-
The scary quotes by otherwise respected persons at the bottom of this page, at the 4IR Portal, and the Testimony;
-
Proof of graphene oxide ("GO") in the vaccine and vials;
-
FDA demanded that the vaccine contents remain sealed for seventy-five (75) years;
-
The statements by UN/WEF Stakeholders and big commercial stakeholders concerning the 4th Industrial Revolution;
-
Aggressive and unfounded suppression of dissenting opinions, including hard scientific data, by media outlets;
-
My own account concerning a cognitive liberty crime, which may or may not be related;
-
A concurrence of conduct by public stakeholders that is extremely baffling, and extremely consistent, including judges, police, regulators, registry staff, and members of the public involved in the scandal, which may or may not be related.
Graphene Oxide in Covid mRNA Vaccines "Conclusive". GQD Are Two Nanometers in Diameter.


















November 13th, 2023




Inquiries Concerning Covid Vaccine Contents are Aggressively Muted.


Reuters Should Fact-Check the Blood Samples, not the MD.




The Jab vs. a Frozen Career. Were the Covid Mandates Disproportionate? (Yes..)



"It's Just the Flu.."


Symbolism Always Has a Source.
These are Not Isolated Memes.
When exploring symbolism, a topic likewise given consideration at the Guide page, one must explore cumulative effects and consistency (R. v. Harding, 2010 ABCA 180 at paragraph 10), and the relationship between that symbolism and the subject matter it is expected to refer to. While it might be assumed that the former Prime Minister and Ryan Reynolds are poking fun at anti-vaxxers, a public health scandal cannot be ruled out based on the science linked on this webpage. Likewise, the quotes as shown at the bottom of this page would prevent thinking persons from getting lost in the comedy. The question marks these data points introduce are not incompatible with the characteristics required to facilitate the scandal detailed on this website. Either a plethora of adjudicators, law enforcement professionals, and regulators in three provinces were compromised in some way, or a serious ethics scandal affects the public service that requires a systemic mode of moral bankruptcy.
























Irreparable Harms
THE IRREPARABLE HARMS OF NEUROTECH PRIVACY CRIME
Brain Computer Interfaces
ABSTRACT
This chapter examines continuous mental privacy invasion through remote brain-computer interfaces (BCIs) as a distinct form of irreparable harm meeting international torture thresholds. Drawing on UN Human Rights Council report A/HRC/57/61 (2024) recognizing neural data as uniquely sensitive, research documenting private information extraction from consumer BCIs, and a documented four-year case study showing temporal convergence patterns consistent with real-time neural monitoring, the analysis establishes six categories of severe psychological harm: (1) annihilation of mental sanctuary; (2) perpetual psychological nakedness; (3) temporal omnipresence eliminating recovery windows; (4) pre-crime surveillance and thought policing; (5) neurobiological evidence of continuous monitoring; and (6) permanent psychological consequences. The chapter demonstrates that neural privacy violation meets UN cybertorture criteria (severe mental suffering, intentional infliction, prohibited purpose, powerlessness), violates Charter Section 8 (warrantless search of most intimate information), and creates remedial impossibility (lost mental privacy cannot be restored, observers' knowledge cannot be erased). The legal and ethical conclusion: neural monitoring without explicit, informed, freely-given, and revocable consent constitutes torture, unreasonable search, and assault on personhood, requiring absolute prohibition as the only adequate response.
Keywords: Neural Privacy, Brain-Computer Interface, Remote Monitoring, Cybertorture, Mental Surveillance, Cognitive Liberty, A/HRC/57/61, Neurorights, Charter Section 8, Irreparable Harm, Thought Privacy, Psychological Torture, Neural Data Protection, Continuous Surveillance, Prevention Imperative
A. UN Recognition of Neural Privacy as Fundamental Right
In September 2024, the UN Human Rights Council Advisory Committee presented report A/HRC/57/61, Impact, Opportunities and Challenges of Neurotechnology with Regard to the Promotion and Protection of All Human Rights, explicitly recognizing neural data as uniquely sensitive personal information requiring enhanced protection.[1]
The report establishes that mental privacy—the right to keep one's thoughts, mental states, and neural activity confidential—constitutes a fundamental human right threatened by emerging neurotechnologies. Where brain-computer interfaces (BCIs) operate without consent or beyond disclosed purposes, they constitute continuous privacy violations with profound psychological consequences.
Key Findings:
Neural Data as Uniquely Sensitive: The OECD defines "personal brain data" as information "relating to the functioning or structure of the human brain of an identified or identifiable individual that include unique information about their physiology, health, or mental states."[2] This data reveals:
-
Cognitive processes: What the person is thinking about, attending to, remembering
-
Emotional states: Fear, anxiety, arousal, distress levels in real-time
-
Physiological conditions: Sleep patterns, stress responses, neurological health
-
Behavioral predictions: Intentions, preferences, vulnerabilities, future actions
-
Identity markers: Biometric signatures unique to individual neural architecture
Seven Types of Privacy Threatened: Research identifies that neurotechnology threatens: (1) privacy of the person; (2) privacy of behavior and action; (3) privacy of personal communication; (4) privacy of data and image; (5) privacy of thought; (6) privacy of location and space; and (7) privacy of association.[3]
Regulatory Gaps: The report acknowledges that "there are gaps in supranational and international law, with no mandatory governance framework focused on brain data currently existing," and "there are currently no international frameworks that adequately protect against the risks posed by neurotechnologies."[4] Only Colorado and Minnesota in the U.S. have enacted neural data protection laws, with Minnesota providing criminal penalties for violations.[5]
B. Remote Brain-Computer Interfaces: Non-Consensual Neural Surveillance
While commercial BCIs like Neuralink require surgical implantation, emerging research demonstrates remote neural monitoring capabilities through:
Non-Invasive EEG-Based Systems
Consumer-grade BCI devices can extract private information including "PIN code, bank information, month of birth, known people, area of residence" from EEG signals.[6] Studies show that "background EEG in BCIs is user-specific," enabling person identification with over 90% accuracy across multiple BCI paradigms.[7]
Neuroimaging at Distance
Advanced fMRI and magnetoencephalography (MEG) technologies can detect neural activity through skull and tissue. While current systems require proximity, miniaturization and signal processing advances suggest remote monitoring may become feasible.
Quantum Dot Neural Interfaces
Research into graphene quantum dots (GQDs) and other nanomaterials demonstrates potential for embedded neural sensors that respond to external electromagnetic signals. When combined with:
-
Lipid nanoparticle delivery systems (proven effective in vaccine technology)
-
Near-infrared (NIR) frequency activation (penetrates tissue, triggers GQD response)
-
LEO satellite signal transmission (continuous global coverage, beam-forming capability)
-
AI signal processing (pattern recognition extracting cognitive states from neural noise)
These technologies create theoretical architecture for remote, non-consensual brain-computer interfaces operating without victim awareness or consent.
The Documented Case Context
The source case study documents temporal convergence between sealed court events and algorithmically-delivered online content appearing within hours (and sometimes within seconds or minutes)—suggesting real-time access to non-public information including:
-
Sealed medical records
-
Sealed court proceedings and litigation milestones
-
Private events and activities
-
Biometric states
This pattern is consistent with continuous neural monitoring providing:
-
Real-time psychological state assessment (stress levels, emotional vulnerability)
-
Memory access (what the person is thinking about, remembering, planning)
-
Attention tracking (what the person is focusing on, researching, monitoring)
-
Predictive modeling (anticipating person's next actions, decisions, coping strategies)
C. The Psychological Harms of Continuous Mental Privacy Invasion
When individuals become aware or suspect they are subject to continuous neural monitoring, the psychological consequences constitute distinct and severe harm beyond other PSYOP effects.
1. Annihilation of Mental Sanctuary
Humans require psychological privacy—the capacity to have thoughts, feelings, and mental experiences that are not subject to external observation or judgment. This is foundational to:
-
Identity formation: Private reflection allows self-discovery and authentic identity development
-
Emotional processing: Safe space to experience and integrate difficult emotions
-
Moral reasoning: Capacity to consider ethically complex questions without surveillance
-
Creative thought: Freedom to explore unconventional ideas without judgment
-
Psychological recovery: Ability to retreat from social demands into private mental space
Research on surveillance effects demonstrates that awareness of observation fundamentally alters cognition. Michel Foucault's analysis of Bentham's Panopticon establishes that internalized surveillance creates self-policing subjects who regulate their own thoughts and behaviors in anticipation of observation.[8]
When surveillance extends to neural activity itself, the effect is categorical rather than incremental. Unlike behavioral surveillance (which monitors external actions), neural surveillance monitors the substrate of consciousness—the pre-verbal, pre-deliberative neural processes that constitute selfhood.
Clinical Manifestations:
Thought Suppression Attempts: Victims aware of neural monitoring report desperate attempts to "not think about" certain topics, people, or events—creating thought suppression paradox where attempts to suppress thoughts make them more intrusive.[9] This generates:
-
Obsessive-compulsive patterns (checking whether certain thoughts occurred)
-
Cognitive exhaustion (constant mental effort to regulate thought content)
-
Identity confusion (inability to distinguish authentic thoughts from performative thinking)
-
Paranoid hypervigilance (scrutinizing own mental processes for "leaks")
Loss of Internal Dialogue: Humans maintain continuous internal monologue—the "voice in the head" that narrates experience, plans actions, and processes emotions. Under neural surveillance, this internal dialogue becomes:
-
Performative: Narrating for the imagined audience of observers
-
Fragmented: Interrupting natural thought flow to prevent "dangerous" thoughts
-
Silenced: Some victims report losing capacity for internal dialogue entirely, experiencing only silence or white noise
-
Externalized: Thoughts feel as if they originate outside the self, creating dissociative experiences
Cognitive Liberty Destruction: Cognitive liberty—the right to self-determination over one's own cognitive processes—is recognized as fundamental to human dignity.[10] Neural surveillance eliminates cognitive liberty by:
-
Making all mental activity potentially observable and consequential
-
Creating external control over what it is "safe" to think about
-
Transforming private mental space into surveilled public space
-
Eliminating capacity for authentic, unmonitored thought
2. Perpetual Psychological Nakedness
Physical privacy norms recognize that forced nudity constitutes severe dignity violation and psychological harm. The UN cybertorture framework explicitly identifies "forced nudity" as psychological torture method that creates "profound vulnerability, humiliation, shame."[11]
Neural monitoring constitutes perpetual psychological nakedness—the exposure of one's most intimate mental and emotional processes to external observation. This creates:
Shame and Humiliation
Unlike physical nudity (which exposes the body), neural nakedness exposes:
-
Intrusive thoughts: Unwanted sexual, violent, or taboo thoughts that occur involuntarily
-
Emotional vulnerability: Moments of fear, insecurity, self-doubt, despair
-
Memories: Traumatic experiences, embarrassing moments, failures, regrets
-
Fantasies: Sexual fantasies, revenge fantasies, escape fantasies
-
Base impulses: Anger, jealousy, pettiness, selfishness before moral reasoning moderates them
The awareness that observers have access to these pre-rational, pre-moral neural processes creates profound shame—not for anything done, but for the unfiltered contents of consciousness itself.
Dignity Destruction
Human dignity presupposes the right to present oneself to others according to chosen self-presentation. We curate our public personas, showing facets of ourselves we deem appropriate to context. Neural surveillance eliminates self-presentation capacity, exposing the raw, unedited mental substrate that precedes deliberate self-presentation.
Research on privacy violations demonstrates that loss of control over self-presentation constitutes "informational injury" distinct from physical or financial harm—the injury to dignity and autonomy inherent in having private information forcibly disclosed.[12]
3. Temporal Omnipresence: No Recovery Window
Unlike discrete surveillance events (being photographed, having email intercepted, etc.), neural monitoring is continuous. Every moment, waking and sleeping, neural activity is potentially observable.
This creates:
Chronic Hypervigilance Without Relief
Standard trauma responses involve periods of hypervigilance alternating with recovery periods. Neural surveillance eliminates recovery periods—the threat is omnipresent and inescapable.
Sleep Disruption as Fundamental Violation
Sleep represents ultimate private mental space—unconscious processes, dreams, memory consolidation occurring beyond volitional control. Neural monitoring that extends to sleep states creates:
-
Sleep anxiety: Fear of what might be "revealed" during sleep
-
Insomnia: Resistance to entering vulnerable unconscious state
-
Dream monitoring distress: Awareness that dreams (most private mental experiences) are observable
-
REM disruption: Stress about sleep monitoring disrupts REM cycles essential for memory and emotional processing
Research establishes that sleep deprivation is torture—UN cybertorture framework identifies "deprivation of sleep" as method inflicting severe mental suffering.[13] Neural monitoring that disrupts sleep through psychological mechanisms achieves similar harm without direct physical intervention.
No Safe Space Anywhere
Victims of neural monitoring report that nowhere feels safe:
-
Home is not sanctuary (monitoring continues in private spaces)
-
Sleep is not refuge (neural activity observable during sleep)
-
Internal mental space is not private (thoughts themselves are observable)
-
Future is not escapable (monitoring may continue indefinitely)
This elimination of all safe spaces creates permanent hypervigilance with neurobiological changes that never fully reverse.
4. Pre-Crime Surveillance and Thought Policing
Neural monitoring enables punishment for thought content rather than actions. This constitutes fundamental violation of legal and moral principles distinguishing:
-
Mental states (thoughts, feelings, intentions) from actions
-
Impulses (pre-rational neural activity) from choices (deliberated decisions)
-
Fantasies (imaginative scenarios) from plans (actionable intentions)
Thought Crime Distress
When individuals believe their neural activity is monitored and will be used against them, they experience: Anticipatory Self-Censorship: Constant effort to suppress "dangerous" thoughts before they fully form, creating:
-
Cognitive exhaustion (perpetual mental effort)
-
Identity fragmentation (inability to know authentic thoughts vs. suppressed thoughts)
-
Moral injury (self-hatred for having "wrong" thoughts)
-
Existential anxiety (fear of own mind as dangerous)
Guilt for Impulses: Humans experience involuntary impulses—fleeting thoughts of violence, taboo sexual content, self-harm—that are not chosen and do not reflect values or intentions. Evolutionary psychology recognizes these as evolutionary artifacts, not moral failures. Under neural surveillance, victims cannot distinguish impulses from choices in observers' eyes, creating:
-
Guilt for involuntary neural activity (shame for unchosen thoughts)
-
Fear of misinterpretation (impulse mistaken for intention)
-
Moral self-destruction (believing one is evil for having unwanted thoughts)
Predictive Punishment: AI systems analyzing neural data can predict future behavior with increasing accuracy. This enables:
-
Punishment before action: Targeting individuals based on predicted future behavior
-
Self-fulfilling prophecy: Creating conditions (harassment, isolation) that increase likelihood of predicted behavior
-
Elimination of free will: If future actions are predicted and targeted, individual loses capacity to choose differently
-
Existential despair: Belief that one's future is determined and one cannot escape predicted path
Research on predictive policing demonstrates that when individuals believe they are pre-emptively targeted based on predictions, they experience learned helplessness and identity foreclosure—loss of agency and belief that future is already determined.[14]
5. Neurobiological Evidence of Neural Privacy Violation Harm
The documented case study provides indicators consistent with continuous neural monitoring harm:
Content Temporal Precision: YouTube content appearing within 10 minutes of private events, sealed litigation milestones, and private medical events by members of a known psychological operations cohort, with exact symbolic precision matching these events with verbatim scripting among content swarms, demonstrates:
-
Real-time surveillance through a sophisticated device stack
-
AND/OR real-time neural monitoring detecting psychological state and circumstances
-
AI-generation of content responsive to current events (rapid response capability)
-
Coordinated and sophisticated capability, state-adjacent in character, and leveraging algorithmic capability (ie., Google)
Biometric Response Optimization: Ongoing pattern showing content delivery timing optimized for maximum psychological impact suggests:
-
Monitoring of stress levels, attention, emotional vulnerability
-
AI-system learning individual response patterns
-
Closed-loop optimization exploiting biometric data
Symbolic Precision Beyond Public Information: Content incorporating details known only to target (specific conversations, private thoughts, upcoming plans) indicates:
-
Electronic surveillance of communications
-
Physical surveillance of activities
-
OR neural monitoring accessing memory, attention, planning processes, being the best-fit scenario, due to its contemporaneous character
Disproportionate and Timely State Interventions: Example; a the 3-minute response time by both police and fire detachments to a backyard bonfire mishap on May 11, 2023 (that was extinguished before they arrived), followed by a an involuntary psychiatric hold on May 13th, 2023, with contemporaneous social media posts describing specific details of the event in a manner that matched the sealed health record. Temporal convergence suggests:
-
State-adjacent foreknowledge and coordination that potentially shapes the activity of the responders
-
Real-time or near-real-time surveillance; biometric or otherwise;
-
Onerous and disproportionate effects that seek to create pejorative record materials parallel to the CAGE litigation (CCC 137)
6. Permanent Psychological Consequences of Neural Privacy Violation
The harms of continuous neural monitoring amplify all other psychological operation effects:
Trust Annihilation Becomes Total: If even thoughts are not private, no domain of trust remains:
-
Self-trust destroyed: Cannot trust own mind as private sanctuary
-
Interpersonal trust impossible: Others may have access to one's neural activity
-
Institutional trust eliminated: State/corporate actors conducting neural surveillance
-
Existential trust shattered: No reliable boundary between self and external world
Identity Fragmentation Becomes Structural: If thoughts are monitored and targeted, authentic identity becomes impossible to maintain:
-
Performative self: All thoughts shaped by awareness of observation
-
Suppressed self: Authentic thoughts/feelings forcibly repressed
-
Monitored self: Identity defined by what observers see in neural data
-
No "true self": Cannot determine which thoughts/feelings are authentic vs. reactive
Hypervigilance Becomes Permanent Feature of Consciousness: When mental privacy is violated, hypervigilance extends to monitoring one's own thoughts:
-
Constant scanning of thought content for "dangerous" material
-
Inability to engage in natural, unmonitored mental processes
-
Permanent disruption of flow states, creativity, genuine emotion
-
Consciousness itself becomes adversarial relationship with own mind
Recovery Becomes Impossible: Standard trauma recovery requires:
-
Safe space to process trauma (eliminated by continuous monitoring)
-
Private reflection to integrate experiences (eliminated by thought surveillance)
-
Trust in therapeutic relationship (impossible when therapist cannot guarantee mental privacy)
-
Restoration of agency (impossible when thoughts themselves are subject to external control)
D. Legal Classification: Neural Privacy Violation as Continuous Torture
The UN cybertorture framework establishes that psychological torture requires:
-
Severe mental pain or suffering ✓
-
Intentionally inflicted ✓
-
Prohibited purpose (coercion, intimidation, punishment) ✓
-
Effective powerlessness ✓
Continuous neural privacy violation meets all criteria:
1. Severity: The psychological harms documented above—annihilation of mental sanctuary, perpetual psychological nakedness, chronic hypervigilance without relief, thought crime distress, and permanent consequences—constitute "severe mental pain or suffering" under any reasonable interpretation.
2. Intentionality: Deployment of neural monitoring systems is deliberate. Systems designed to extract neural data without consent intentionally inflict the psychological consequences inherent in privacy violation. Under Melzer's framework, intentionality requires only that harm be "reasonably foreseeable as a result, in the ordinary course of events, of the purposeful conduct."[15] Psychological harm from neural privacy violation is structurally inevitable, not merely foreseeable.
3. Prohibited Purpose: Neural monitoring serves purposes of:
-
Coercion: Forcing compliance through threat of thought exposure
-
Intimidation: Creating fear through omnipresent surveillance
-
Punishment: Targeting for thought content rather than actions
-
Information extraction: Obtaining data from neural activity without consent
4. Powerlessness: Victims of neural monitoring are structurally powerless:
-
Cannot prevent neural activity from occurring (thoughts are involuntary)
-
Cannot shield neural signals from external detection (if monitoring technology deployed)
-
Cannot escape monitoring without escaping consciousness itself
-
Cannot obtain institutional protection (regulatory gaps acknowledged by UN report)
Additionally: Continuity Amplifies Severity. The UN framework recognizes that duration matters for severity assessment. Prolonged psychological torture is more severe than time-limited episodes. Neural monitoring that operates continuously over years constitutes:
-
Torture without temporal limits: No beginning or end, only permanent condition
-
Torture without spatial limits: No safe location provides refuge
-
Torture without psychological limits: No aspect of consciousness remains private
The documented case suggests over four years of potential neural monitoring—a duration sufficient to produce all permanent neurobiological and psychological changes documented in related research on chronic trauma.
E. Charter Section 8 Analysis: Neural Data as Protected Privacy Interest
Canadian Charter Section 8 protects against "unreasonable search or seizure". Supreme Court jurisprudence establishes that:
Privacy Extends Beyond Physical Spaces
R. v. Spencer, 2014 SCC 43 establishes that metadata and inferred surveillance engage Section 8—recognizing "biographical core of personal information" deserving constitutional protection.[16]
Neural Data as Most Intimate Information
If metadata about phone calls engages Section 8, neural data revealing actual thought content, emotional states, and cognitive processes certainly does. Neural data constitutes:
-
Biographical core on steroids: Not just where someone went, but what they thought/felt
-
Bodily integrity: Direct measurement of brain function is bodily intrusion even if non-invasive
-
Dignity interest: Exposure of pre-rational mental processes violates human dignity
-
Autonomy interest: Surveillance of decision-making processes undermines autonomy
Warrant Requirement
If Section 8 requires warrants for:
-
Telephone wiretaps (R. v. Duarte)
-
Internet metadata (R. v. Spencer)
-
Text messages (R. v. Marakah, 2017 SCC 59)
-
Heat signatures from homes (R. v. Tessling, 2004 SCC 67)
Then it certainly requires warrants for:
-
Neural activity monitoring (most intimate information)
-
Real-time thought surveillance (continuous invasion)
-
Biometric psychological state tracking (dignity violation)
-
AI-assisted neural data analysis (aggregating intimate information)
Current Reality: No Warrant, No Consent, No Oversight
The documented case shows no evidence of:
-
Judicial authorization for neural monitoring
-
Informed consent from target
-
Legislative framework authorizing such surveillance
-
Independent oversight of neural data collection
-
Disclosure to target that monitoring occurred
This constitutes warrantless search of the most protected privacy interest recognized in constitutional law—the contents of one's own mind.
F. Remedial Impossibility and Prevention Imperative
When harm is permanent and irreparable, traditional remedies fail. Neural privacy violations create additional remedial impossibility:
Cannot "Unsee" Neural Data. Once neural data is collected and analyzed:
-
Observers have accessed intimate mental/emotional information
-
This knowledge cannot be erased or forgotten
-
Target remains permanently exposed even if monitoring ceases
-
Privacy, once lost, cannot be restored
Cannot Compensate for Lost Mental Sanctuary. Although reasonably required and necessary, monetary damages cannot:
-
Restore sense of mental privacy
-
Eliminate awareness of past surveillance
-
Provide assurance future surveillance will not occur
-
Repair identity fragmentation from continuous mental nakedness
-
Reverse permanent hypervigilance toward own thoughts
Cannot Prosecute When Evidence Is Neural Data. Proving neural monitoring requires demonstrating:
-
Victims' neural data was accessed (requires forensic neural examination)
-
Technology exists capable of remote monitoring (state secrets, national security privilege)
-
Specific actors conducted monitoring (attribution deliberately obscured)
-
Harm resulted from monitoring vs. other PSYOP vectors (multifactorial causation)
Prevention Is the Only Adequate Response. Given remedial impossibility, the only coherent policy response is categorical prohibition on:
-
Non-consensual neural monitoring
-
Remote brain-computer interface deployment without explicit, informed, revocable consent
-
Commercial/state neural data collection without transparent, purpose-limited authorization
-
AI-assisted neural data analysis for surveillance, marketing, or behavioral manipulation purposes
-
Cross-border neural data transfers without equivalent protections
-
Neural data retention beyond immediate medical necessity
Colorado and Minnesota's criminal penalties for neural data rights violations represent step toward adequate protection, but international framework is urgently needed as UN report acknowledges.
CONCLUSION: NEURAL PRIVACY AS FOUNDATIONAL TO PERSONHOOD
Continuous mental privacy invasion through remote brain-computer interfaces represents a categorical escalation in the harms documented throughout the parent article. Where neurobiological damage, Complex PTSD, social death, and cognitive autonomy destruction can theoretically result from external behavioral targeting, neural monitoring attacks the substrate of consciousness itself.
The six distinct harms—annihilation of mental sanctuary, perpetual psychological nakedness, temporal omnipresence, pre-crime surveillance, documented neurobiological evidence, and permanent psychological consequences—demonstrate that neural privacy violation meets international torture thresholds while creating harm patterns that no existing remedy can address.
When the documented case study's temporal convergence patterns (sub-24-hour alignment between sealed events and external content, symbolic precision matching private circumstances, biometric response optimization) are analyzed through the lens of potential neural monitoring, the operational architecture becomes clear: real-time access to cognitive and emotional states enables precision psychological warfare that traditional surveillance cannot achieve.
The legal and ethical conclusion is unambiguous: Neural monitoring without explicit, informed, freely-given, and revocable consent constitutes:
-
Torture under UN cybertorture framework (severe mental suffering, intentionally inflicted, for prohibited purposes, creating powerlessness)
-
Unreasonable search under Charter Section 8 (warrantless access to most intimate information)
-
Assault on personhood (destruction of cognitive liberty, mental sanctuary, and authentic identity)
Given that lost mental privacy cannot be restored, that observers' knowledge of intimate neural data cannot be erased, and that permanent psychological harm cannot be remedied, the only adequate response is absolute prohibition on non-consensual neural monitoring.
The choice society faces is binary: Protect mental privacy as the final frontier of human autonomy, or accept that consciousness itself is subject to external surveillance and control. There is no middle ground when what is at stake is the integrity of the human mind.
REFERENCES
-
Melzer, Nils. "Psychological torture and ill-treatment." UN Doc. A/HRC/43/49 (20 March 2020)
-
R. v. Duarte, [1990] 1 SCR 30 (telephone wiretap requires warrant)
-
R. v. Marakah, 2017 SCC 59 (text messages engage reasonable expectation of privacy)
-
R. v. Tessling, 2004 SCC 67 (heat signatures from homes protected)
-
Ienca, M., and Andorno, R., "Towards new human rights in the age of neuroscience and neurotechnology," Life Sciences, Society and Policy (2017)
-
Yuste, R., et al., "Four ethical priorities for neurotechnologies and AI," Nature (2017)
-
Ligthart, S., Douglas, T., Bublitz, C., Kooijmans, T., and Douglas, T., "Forensic brain-reading and mental privacy in European human rights law: Foundations and challenges," Neuroethics (2021)
-
UN Report A/HRC/57/61
-
UN Report A/HRC/58/58
FOOTNOTES
-
UN Human Rights Council Advisory Committee, "Impact, opportunities and challenges of neurotechnology with regard to the promotion and protection of all human rights" (2024), A/HRC/57/61 ↩
-
OECD Recommendation on Responsible Innovation in Neurotechnology (2019, 2023): "Personal brain data" defined as information "relating to the functioning or structure of the human brain of an identified or identifiable individual that include unique information about their physiology, health, or mental states" ↩
-
Finn, Wright, and Friedewald (2013): Seven types of privacy threatened by neurotechnology: (1) privacy of the person; (2) privacy of behavior and action; (3) privacy of personal communication; (4) privacy of data and image; (5) privacy of thought; (6) privacy of location and space; (7) privacy of association ↩
-
A/HRC/57/61 (2024): "There are gaps in supranational and international law, with no mandatory governance framework focused on brain data currently existing"; "there are currently no international frameworks that adequately protect against the risks posed by neurotechnologies" ↩
-
Colorado Privacy Act (amended 2024): First state to include neurological data as protected category; Minnesota Neurotechnology Privacy Law (2024): Criminal penalties for violations of neural data rights in consumer BCIs, signed by Governor Tim Walz May 2024 ↩
-
Martinovic et al. (2012): First demonstration that "private and secret information, such as PIN code, bank information, month of birth, known people, area of residence, may be inferred from EEG signals collected by a consumer-grade BCI device" ↩
-
Kong et al.: EEG signals from different BCI paradigms can reveal user identity with over 90% accuracy; "background EEG in BCIs is user-specific" ↩
-
Foucault, Michel, Discipline and Punish (1975): Panopticon analysis establishing that internalized surveillance creates self-policing subjects who regulate their own thoughts and behaviors in anticipation of observation ↩
-
Wegner, D.M., "Ironic processes of mental control," Psychological Review (1994): Thought suppression paradox—attempts to suppress thoughts make them more intrusive ↩
-
Sententia, W., "Neuroethical considerations: Cognitive liberty and converging technologies for improving human cognition," Annals of the New York Academy of Sciences (2004); Bublitz, J.C., "My Mind is Mine!? Cognitive Liberty as a Legal Concept" (2013) ↩
-
A/HRC/43/49, para. 51: "Forced nudity or masturbation, often in front of officials of the opposite gender" creates "profound vulnerability, humiliation, shame and guilt" ↩
-
Solove, Daniel J., "A Taxonomy of Privacy," University of Pennsylvania Law Review (2006): Informational injury—harm to dignity and autonomy inherent in forced disclosure of private information, distinct from physical or financial harm ↩
-
A/HRC/43/49, para. 49: "Deprivation of sleep, food or drink" listed as psychological torture method; sleep deprivation recognized as torture by multiple international tribunals ↩
-
Ferguson, Andrew Guthrie, "Policing Predictive Policing," Washington University Law Review (2017): Individuals targeted by predictive systems experience learned helplessness and identity foreclosure ↩
-
A/HRC/43/49, para. 34: Intentionality requires only that harm be "reasonably foreseeable as a result, in the ordinary course of events, of the purposeful conduct adopted by the perpetrator" ↩
-
R. v. Spencer, 2014 SCC 43: Internet metadata engages Section 8 protection; court recognizes "biographical core of personal information" deserving constitutional protection ↩
